I have been running 184.19 on an AC66U-B1 for a couple of weeks. I have several LAN devices that run on-device Nordvpn clients and have two devices without. I have set up a single OpenVPN client in Merlin with policy routing for the two devices (static IPs) to route through the VPN, all other devices run through to WAN. I have yaz vpnmgr installed but not managing my Openvpn client ( at this time).
EDIT: I have uninstalled vpnmgr to lessen variables, but problem persists.
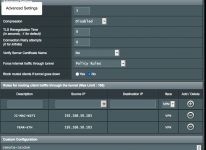
If I set "Force all traffic..etc" to "no", it works as expected.
If set to "yes" it works as expected.
if, however I set it to "policy rules", either strict or not, no traffic travels through the VPN.
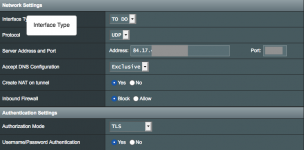
I have read (obsessively) the wiki and all relevant docs, so I have tried about everything I could think of, even re-declaring the default of /24 as "WAN" first and then entering my two exceptions as VPN. Ive tried /24 to VPN, nope. And, yes Ive tried excluding the router from vpn...opposite the example in the wiki. In all cases, Ive been careful to follow the WAN first then VPN evaluation rules. All of my DNS settings are correct and functioning as expected.
Im missing something and its frustrating.
Like I said, the vpn client works great and even leaving the OpenVpn client "on" and "Force all traffic" to "off" work fine together...but policy routing is a no-go.
If anyone has any ideas, Id really appreciate the help. Thanks.
EDIT: I have uninstalled vpnmgr to lessen variables, but problem persists.
If I set "Force all traffic..etc" to "no", it works as expected.
If set to "yes" it works as expected.
if, however I set it to "policy rules", either strict or not, no traffic travels through the VPN.
I have read (obsessively) the wiki and all relevant docs, so I have tried about everything I could think of, even re-declaring the default of /24 as "WAN" first and then entering my two exceptions as VPN. Ive tried /24 to VPN, nope. And, yes Ive tried excluding the router from vpn...opposite the example in the wiki. In all cases, Ive been careful to follow the WAN first then VPN evaluation rules. All of my DNS settings are correct and functioning as expected.
Im missing something and its frustrating.
Like I said, the vpn client works great and even leaving the OpenVpn client "on" and "Force all traffic" to "off" work fine together...but policy routing is a no-go.
If anyone has any ideas, Id really appreciate the help. Thanks.
Last edited: