postoronnim-v
Regular Contributor
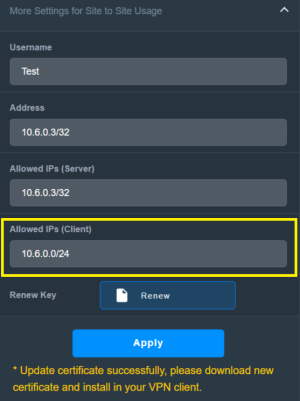
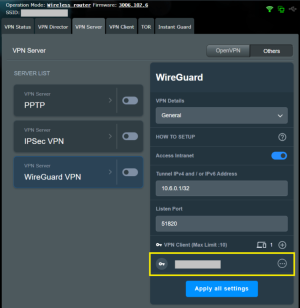
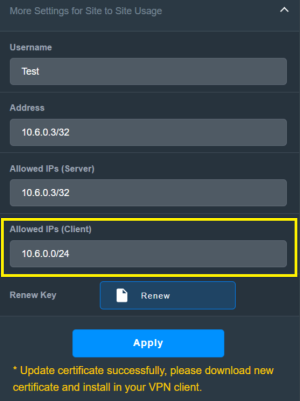
I have an RT-BE88U router. The Wireguard VPN server (10.6.0.1/32) is enabled. The "Access Intranet" and "Allow DNS" options are disabled. However, a client connected to this server can access the router's login (192.168.50.1). For security, I tried enabling https login on the router. I successfully obtained a Let's Encrypt certificate, but I couldn't access the router via https://name.asuscomm.com:8443.
Questions: 1. Why is access to 192.168.50.1 open through the Wireguard VPN server?
2. Why isn't login using the Let's Encrypt certificate working?
Questions: 1. Why is access to 192.168.50.1 open through the Wireguard VPN server?
2. Why isn't login using the Let's Encrypt certificate working?