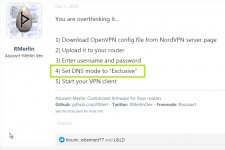
Hi. I have a problem with setting up my VPN connection. I used this procedure to configure:

 support.nordvpn.com
support.nordvpn.com
This procedure is for another router but I thought it might work .. I have an Asus RT-AC68U router and FW version 386.1_2
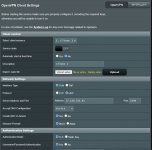
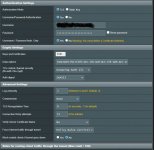
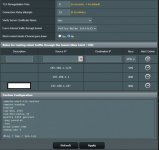
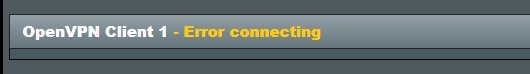
When I downloaded the configuration from the NORD VPN and uploaded it to the router, I entered the credentials and did not change any configuration, I was able to connect to the NORD but after a few hours I saw that I was already disconnected. Then I tried the procedure from NORD VPN - link attached above, but it does not work with this procedure. I have VDSL internet and my router is establishing a PPPoE connection. I will ask for advice. well thank you

AsusWRT Merlin setup with NordVPN
Fortunately, you can use NordVPN with your Asus router. These instructions will help you set up an OpenVPN connection with NordVPN on your ASUS router flashed with AsusWRT-Merlin firmware. The inst...
This procedure is for another router but I thought it might work .. I have an Asus RT-AC68U router and FW version 386.1_2
When I downloaded the configuration from the NORD VPN and uploaded it to the router, I entered the credentials and did not change any configuration, I was able to connect to the NORD but after a few hours I saw that I was already disconnected. Then I tried the procedure from NORD VPN - link attached above, but it does not work with this procedure. I have VDSL internet and my router is establishing a PPPoE connection. I will ask for advice. well thank you