Hello! I've got an RT-BE88U running the latest stock firmware, and using Guest Network Pro I've setup 2 wireless VLANs for IoT and guest devices, and an additional VLAN for my home lab/server running services like Pi-Hole, Nextcloud and others.
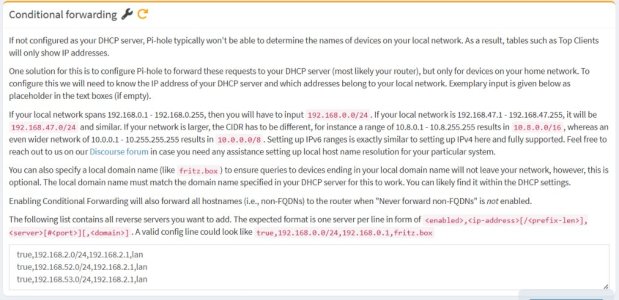
The problem I've run into is that inter-VLAN connectivity is quite primitive on the stock software, you can either isolate them completely or interconnect them completely, without the ability to configure firewall rules between VLANs. So right now, my main LAN is just fully connected to the server VLAN to use its services, which is not ideal, as I want to expose Nextcloud to the internet using a reverse proxy, and I want to reduce the blast radius as much as possible in case of a breach. Plus, the IoT and guest networks are isolated, so they can't access Pi-Hole directly, and have to use the router as the indirect DNS server. I want to do two things:
P.S. Feel free to poke holes in my setup, I'm still in the process of learning home networking.
The problem I've run into is that inter-VLAN connectivity is quite primitive on the stock software, you can either isolate them completely or interconnect them completely, without the ability to configure firewall rules between VLANs. So right now, my main LAN is just fully connected to the server VLAN to use its services, which is not ideal, as I want to expose Nextcloud to the internet using a reverse proxy, and I want to reduce the blast radius as much as possible in case of a breach. Plus, the IoT and guest networks are isolated, so they can't access Pi-Hole directly, and have to use the router as the indirect DNS server. I want to do two things:
- Isolate all VLANs and just open port 53 between all of them so they can use Pi-Hole directly.
- Open certain ports between my homelab VLAN and my main network so I can both control my services and access data on them from my PC on the main network.
P.S. Feel free to poke holes in my setup, I'm still in the process of learning home networking.