#TY
Senior Member
Time to see what's actually happening there by dumping the relevant data structures.
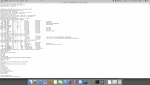
On the OpenVPN *server*, post the output from the following commands.
Code:ip route iptables -vnL INPUT iptables -vnL FORWARD iptables -t nat -vnL POSTROUTING cat /tmp/etc/openvpn/server1/config.ovpn
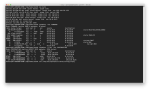
On the OpenVPN *client*, post the output from the following commands.
Code:ip route iptables -vnL FORWARD iptables -t nat -vnL POSTROUTING cat /tmp/etc/openvpn/client1/config.ovpn
From the server (white Terminal):
From the client (Black Terminal)