You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Kingp1n
Very Senior Member
I manually made the change inside the script. Everything is running smoothly. Not sure what the code does behind the scenes but I haven't notice any hiccups. I'll continue to monitor. Thanks.I don’t understand the syntax of this function. Why is logger in $(…) ?
Seems it should be:Code:Post_log() { $(logger -st "($(basename "$0"))" $$ "$1") }
Code:Post_log() { logger -st "($(basename "$0"))" $$ "$1" }
Thanks @dave14305I think you need to replace all0x1000/0x1000with0x2000/0x2000to route through ovpnc2.
Tried this, no luck. Now the DNS leak shows my IP address instead of any VPN.
Not sure if you need to add this
Code:
# Create RPDB rules
ip rule add from 0/0 fwmark "0x2000/0x2000" table ovpnc2 prio 9994 # create VPN 2 fwmarkThanks for the steps. Swinson script need to have "start" or "stop" argument to run. Any other argument is invalid. I run through the debug mode and noticed that rules are deleted before checking the argument entry. His early version check argument entry first and will not do anything if wrong argument is entered. I modified the current version by move Delete_Rules to match the earlier version.As a quick hack... try passing two arguments to the script... and might as well run in debug mode to confirm the root cause (and the other error!)
e.g.
Code:sh -x /jffs/scripts/unbound_via_vc2.sh start start
Anyway, usually we run this in openvpn up/down event with corresponding start/stop argument. So I don't think we will see the difference in normal use case.
Code:
#!/bin/sh
Check_Tun11_Con() {
ping -c1 -w1 -I tun11 1.1.1.1
}
Delete_Rules() {
iptables-save | grep "unbound_rule" | sed 's/^-A/iptables -t mangle -D/' | while read CMD;do $CMD;done
}
Add_Rules() {
iptables -t mangle -A OUTPUT -d "$wan0_dns0"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "$wan0_dns1"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "$wan0_dns0"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "$wan0_dns1"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
}
Unbound_vc1() {
Add_Rules
/jffs/addons/unbound/unbound_manager.sh vpn=1 &
logger -st "($(basename "$0"))" $$ Ending Script Execution
}
Unbound_vpnDisable() {
Delete_Rules
/jffs/addons/unbound/unbound_manager.sh vpn=disable &
logger -st "($(basename "$0"))" $$ Ending Script Execution
}
Poll_Tun11() {
Delete_Rules
sleep 5
timer=5
while [ $timer -lt 300 ]; do
Check_Tun11_Con
if [ "$?" -eq 0 ]; then
Unbound_vc1
logger -st "($(basename "$0"))" $$ Ending Script Execution
exit 0
fi
sleep 1
timer++
done
logger -st "($(basename "$0"))" $$ Script Execution Timeout
exit 3
}
if [ -z "$1" ]; then
logger -st "($(basename "$0"))" $$ Script Arg Missing
exit 1
else
logger -st "($(basename "$0"))" $$ Starting Script Execution
wan0_dns0="$( (nvram get wan0_dns) | awk '{print $1}' )"
wan0_dns1="$( (nvram get wan0_dns) | awk '{print $2}' )"
if [ "$wan0_dns1" = "" ]; then
wan0_dns1 = $wan0_dns0
elif [ "$wan0_dns0" = "" ]; then
wan0_dns0 = $wan0_dns1
if [ "$wan0_dns1" = "" ]; then
logger -st "($(basename "$0"))" $$ wan0_dns is NULL
exit 2
fi
else
case "$1" in
start)
Poll_Tun11
exit 0;;
stop)
Unbound_vpnDisable
exit -1;;
*)
logger -st "($(basename "$0"))" $$ Script Arg Invalid
exit 1;;
esac
fi
fi
Code:
#!/bin/sh
Check_Tun11_Con() {
ping -c1 -w1 -I tun11 1.1.1.1
}
Delete_Rules() {
iptables-save | grep "unbound_rule" | sed 's/^-A/iptables -t mangle -D/' | while read CMD;do $CMD;done
}
Add_Rules(){
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
}
Call_unbound_manager() {
/jffs/addons/unbound/unbound_manager.sh vpn="$1"
}
Poll_Tun11() {
timer=$1
[ -z $timer ] && Post_log "Error Timeout" && exit 1 || sleep 2
Check_Tun11_Con && Add_Rules && Call_unbound_manager "1" || Poll_Tun11 "$((timer--))"
}
Post_log() {
$(logger -st "($(basename "$0"))" $$ "$1")
}
[ -z "$1" ] && Post_log "Script Arg Missing" && exit 1 || Post_log "Starting Script Execution"
wan0_dns="$(nvram get wan0_dns)"
Delete_Rules
case "$1" in
start)
Poll_Tun11 "150" && Post_log "Ending Script Execution" && exit 0;;
stop)
Call_unbound_manager "disable" && Post_log "Ending Script Execution" && exit 0;;
*)
Post_log "Script Arg Invalid" && exit 1;;
esac
Code:
#!/bin/sh
Check_Tun11_Con() {
ping -c1 -w1 -I tun11 1.1.1.1
}
Delete_Rules() {
iptables-save | grep "unbound_rule" | sed 's/^-A/iptables -t mangle -D/' | while read CMD;do $CMD;done
}
Add_Rules(){
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
iptables -t mangle -A OUTPUT -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
}
Call_unbound_manager() {
/jffs/addons/unbound/unbound_manager.sh vpn="$1"
}
Poll_Tun11() {
Delete_Rules
timer=$1
[ -z $timer ] && Post_log "Error Timeout" && exit 1 || sleep 2
Check_Tun11_Con && Add_Rules && Call_unbound_manager "1" || Poll_Tun11 "$((timer--))"
}
Post_log() {
$(logger -st "($(basename "$0"))" $$ "$1")
}
[ -z "$1" ] && Post_log "Script Arg Missing" && exit 1 || Post_log "Starting Script Execution"
wan0_dns="$(nvram get wan0_dns)"
case "$1" in
start)
Poll_Tun11 "150" && Post_log "Ending Script Execution" && exit 0;;
stop)
Delete_Rules && Call_unbound_manager "disable" && Post_log "Ending Script Execution" && exit 0;;
*)
Post_log "Script Arg Invalid" && exit 1;;
esac
Last edited:
Martineau
Part of the Furniture
In an ideal world, you would use meaningful/descriptive variable names (denoted by the '$' prefix) to make it easier to follow/describe what the code is doing, together with not hardcoding the function names to include name of the VPN instance...@Martineau - I tried this and make some tweaks (trial and error) I noticed that in the original script this line has a "$"
/jffs/addons/unbound/unbound_manager.sh vpn="$1"
When I use vpn="$2" or "$3" or "$4" or "$5" I get an error.
(unbound_manager.sh): 2691 ***ERROR Invalid argument '' must be numeric '1-5' or 'disable'.
It appears to work when I remove $
Could this be the issue?
e.g.
becomes
Code like this is very confusing/ambiguous as per your tweak of
which implies that you wish to explicitly pass VPN 1 as the interface instance number to function Call_unbound_manager(), but hardcoding the action of function Call_unbound_manager() to actually always use VPN 2 !
When you used
The variable "$3" doesn't have a value so is empty/blank/uninitialised, so the literal text string 'vpn=' is passed to '/jffs/addons/unbound/unbound_manager.sh' which it doesn't recognise! - hence the error message.
So you could make the code a little more robust
Code:
iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
Code:
VPN_ID=2 # Change this to the desired VPN instance
TAG_MARK_VPN2="0x${VPN_ID}000/0x${VPN_ID}000" # VPN 1 use 0x1000; VPN 2 use 0x2000 etc.
TAG_MARK_WAN="0x8000/0x8000"
iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark $TAG_MARK_VPN2
iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark $TAG_MARK_WANCode like this is very confusing/ambiguous as per your tweak of
Code:
Call_unbound_manager() {
/jffs/addons/unbound/unbound_manager.sh vpn="2"
}
Check_Tun12_Con && Add_Rules && Call_unbound_manager "1" || Poll_Tun12 "$((timer--))"When you used
Code:
/jffs/addons/unbound/unbound_manager.sh vpn="$3"So you could make the code a little more robust
Code:
Call_unbound_manager() {
/jffs/addons/unbound/unbound_manager.sh vpn="$1" # Use the first arg passed to this function as the VPN interface instance literal.
}
Check_Tun_Con && Add_Rules && Call_unbound_manager "$VPN_ID" || Poll_Tun12 "$((timer--))" # Pass variable '$VPN_ID' to function Call_unbound_manager(), as passed to this script!Trial and error can achieve the ultimate goal of the code performing as you desire/expect, and if the code never needs to be modified/maintained/reviewed again, then the use of good programming practice is moot, but as you have found, there is a world of difference between the interpretation of using a variable '$1' and the literal '1' (intentional or not) which still results in potentially hours of frustration for even experienced professional programmers tediously debugging a single character typo!
Glad you finally got it working.
Thanks for taking the time to explain this, @Martineau.In an ideal world, you would use meaningful/descriptive variable names (denoted by the '$' prefix) to make it easier to follow/describe what the code is doing, together with not hardcoding the function names to include name of the VPN instance...
e.g.
becomesCode:iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000 iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000
Code:VPN_ID=2 # Change this to the desired VPN instance TAG_MARK_VPN2="0x${VPN_ID}000/0x${VPN_ID}000" # VPN 1 use 0x1000; VPN 2 use 0x2000 etc. TAG_MARK_WAN="0x8000/0x8000" iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark $TAG_MARK_VPN2 iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark $TAG_MARK_WAN
Code like this is very confusing/ambiguous as per your tweak of
which implies that you wish to explicitly pass VPN 1 as the interface instance number to function Call_unbound_manager(), but hardcoding the action of function Call_unbound_manager() to actually always use VPN 2 !Code:Call_unbound_manager() { /jffs/addons/unbound/unbound_manager.sh vpn="2" } Check_Tun12_Con && Add_Rules && Call_unbound_manager "1" || Poll_Tun12 "$((timer--))"
When you used
The variable "$3" doesn't have a value so is empty/blank/uninitialised, so the literal text string 'vpn=' is passed to '/jffs/addons/unbound/unbound_manager.sh' which it doesn't recognise! - hence the error message.Code:/jffs/addons/unbound/unbound_manager.sh vpn="$3"
So you could make the code a little more robust
Code:Call_unbound_manager() { /jffs/addons/unbound/unbound_manager.sh vpn="$1" # Use the first arg passed to this function as the VPN interface instance literal. } Check_Tun_Con && Add_Rules && Call_unbound_manager "$VPN_ID" || Poll_Tun12 "$((timer--))" # Pass variable '$VPN_ID' to function Call_unbound_manager(), as passed to this script!
Trial and error can achieve the ultimate goal of the code performing as you desire/expect, and if the code never needs to be modified/maintained/reviewed again, then the use of good programming practice is moot, but as you have found, there is a world of difference between the interpretation of using a variable '$1' and the literal '1' (intentional or not) which still results in potentially hours of frustration for even experienced professional programmers tediously debugging a single character typo!
Glad you finally got it working.
I have been running the modified script to route DNS queries through VPN other than #1, and I'm sad to say the script is not consistent/working all the time. I'm getting DNS leaks sometimes.
I'm going to leave the scripting to the pros like yourself @Martineau and revert to the original one. Maybe someday a feature like this can be implemented in unbound_manager.
Does BIND unbound to VPN not do something like this in the advanced features?
I have tried to implement the DNS routing via vpn1 with unbound.
But I didn´t get them working. If I use the "l" command in unbound I get the following error messages. Any ideas why that happens ?
For information: I am using adguard home on my raspberry pi which has my asus router as DNS server.
Thanks a lot.
Hugo
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <data.meethue.com. AAAA IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <d3p8zr0ffa9t17.cloudfront.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <connectivitycheck.gstatic.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 connectivitycheck.gstatic.com. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <forcesafesearch.google.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 www.google.com. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN
Oct 29 08:54:47 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:47 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
But I didn´t get them working. If I use the "l" command in unbound I get the following error messages. Any ideas why that happens ?
For information: I am using adguard home on my raspberry pi which has my asus router as DNS server.
Thanks a lot.
Hugo
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <data.meethue.com. AAAA IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <d3p8zr0ffa9t17.cloudfront.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <connectivitycheck.gstatic.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 connectivitycheck.gstatic.com. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <forcesafesearch.google.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 www.google.com. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN
Oct 29 08:54:47 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:47 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
Was it working before you implement route DNS query to VPN?I have tried to implement the DNS routing via vpn1 with unbound.
But I didn´t get them working. If I use the "l" command in unbound I get the following error messages. Any ideas why that happens ?
For information: I am using adguard home on my raspberry pi which has my asus router as DNS server.
Thanks a lot.
Hugo
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <data.meethue.com. AAAA IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <d3p8zr0ffa9t17.cloudfront.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <connectivitycheck.gstatic.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 connectivitycheck.gstatic.com. A IN
Oct 29 08:54:45 unbound[9589:0] error: SERVFAIL <forcesafesearch.google.com. A IN>: exceeded the maximum number of sends
Oct 29 08:54:45 unbound[9589:0] query: 127.0.0.1 www.google.com. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ubl1jewud0anxkyrtyjg6p5ykb4e15swd8j6avv3.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 o5ijrxlj98qk7a0urekherno05x806phdi0r5v4b.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 s7uvfe251lokkvmfzlblze0wa19rtraztkpxiyj4.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 ub2uevw05r7dsdusomnfbn06d968juuf2m9wa2h5.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 3su7zk6n2ocecmu5jbdlhl14uj8tieqwudwe0yvm.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 iwcu7lyekr0j2ed4u59wlw1v0rituy6dxaam019m.ipleak.net. A IN
Oct 29 08:54:46 unbound[9589:0] error: SERVFAIL <0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:46 unbound[9589:0] query: 127.0.0.1 0yh7m6ktv9gdmo2z1ftqwrpt9se263o8cs2aj0a7.ipleak.net. A IN
Oct 29 08:54:47 unbound[9589:0] error: SERVFAIL <8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN>: exceeded the maximum number of sends
Oct 29 08:54:47 unbound[9589:0] query: 127.0.0.1 8bnyg004jepzfr6221hr69cvq6xg5c32pozcb1jf.ipleak.net. A IN
I have not see this error. Can you run this and see what is the requestlist exceeded count?
Code:
unbound-control stats_noreset | grep -F total.requestlist
unbound-control stats_noreset | grep -F cache.countHi Chongnt,
thanks a lot for your support. I will test and post that result. Before I used unbound in combination with pihole (same combination), but because of DNS Leaks I didn´t use unbound anymore. In the meantime I switched to adguard home on my pi and it is working as expected. As I read this discussion I want to test that. I switched the DNS Server in the LAN section from my pihole to unbound and it was working as expected but ipleak showed the real IP adress for the DNS instead of the VPN DNS adress.
Im made the changes posted on the first side of this discussion, rebooted and since this time it is not working anymore.
thanks a lot for your support. I will test and post that result. Before I used unbound in combination with pihole (same combination), but because of DNS Leaks I didn´t use unbound anymore. In the meantime I switched to adguard home on my pi and it is working as expected. As I read this discussion I want to test that. I switched the DNS Server in the LAN section from my pihole to unbound and it was working as expected but ipleak showed the real IP adress for the DNS instead of the VPN DNS adress.
Im made the changes posted on the first side of this discussion, rebooted and since this time it is not working anymore.
So here are the results:
total.requestlist.avg=5.86594
total.requestlist.max=13
total.requestlist.overwritten=0
total.requestlist.exceeded=0
total.requestlist.current.all=12
total.requestlist.current.user=12
msg.cache.count=85
rrset.cache.count=451
infra.cache.count=53
key.cache.count=0
total.requestlist.avg=5.86594
total.requestlist.max=13
total.requestlist.overwritten=0
total.requestlist.exceeded=0
total.requestlist.current.all=12
total.requestlist.current.user=12
msg.cache.count=85
rrset.cache.count=451
infra.cache.count=53
key.cache.count=0
Hi, I don't see anything abnormal from the output. I would suggest make unbound work without VPN first then retry again. The latest one from @Swinson is posted here: https://github.com/swinsonterry/Unbound_via_vpnHi Chongnt,
thanks a lot for your support. I will test and post that result. Before I used unbound in combination with pihole (same combination), but because of DNS Leaks I didn´t use unbound anymore. In the meantime I switched to adguard home on my pi and it is working as expected. As I read this discussion I want to test that. I switched the DNS Server in the LAN section from my pihole to unbound and it was working as expected but ipleak showed the real IP adress for the DNS instead of the VPN DNS adress.
Im made the changes posted on the first side of this discussion, rebooted and since this time it is not working anymore.
This version is written to bind unbound to open vpn client 1.
@Martineau has updated this to have the flexibility to bind it to any open vpn client.

Unbound - unbound_manager (Manager/Installer utility for unbound - Recursive DNS Server) - General questions / discussion thread 2
Dumb question but how do u add it this list? From diversion -> b (blocking list) -> 1 (change composition custom) -> 2 (customize hosts list) -> 1 (Add hosts list) -> paste new hosts link link here -> e (exit) -> 1 (yes to update list now). It will take some time to update the lists.
 www.snbforums.com
www.snbforums.com
Dear all,
Yesterday I made a several more attempts, but I'm really at a loss , why my setup is not working
.
Objective: DNS requests from Unbound via VPN1
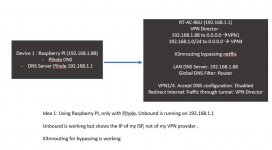
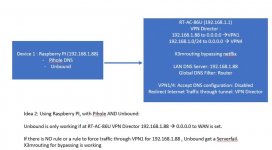
I tried two variants as a setup that I have attached.
In Idea 1 I ran Unbound on the Asus router. I used the Swinson scripts from # 4 in the / jffs / scripts / x3mRouting / vpnclient1-route-up file after the X3mrouting entries, the same with the down entries.
Unsuccessful - always the same error message - server failure.
Then I added modprobe xt_comment to the init-start file according to Post # 237. But I just can't get it to work.
Neither variant 1 nor variant 2.
I wonder why variant 2 doesn't work. I force all traffic from the Raspberry Pi via VPN1 - so the requests from unbound on the Raspberry Pi would also have to be routed via VPN1 - but it does not work.
Since I can no longer see through all the variants here, it would be very nice if someone could explain to me again what exactly I have to do to get my setup running, either over variant1 or over variant2. Would variant2 be better because the pi 4 has more power and so we could increase the prefetch cache for unbound ?
1. Martineau script alone?
2. Martineau script and init start?
3. Edit VPNClient1-route-up and down and Martineau script?
I am totally confused.
Many thanks for the help !
Hugo
Yesterday I made a several more attempts, but I'm really at a loss , why my setup is not working
.
Objective: DNS requests from Unbound via VPN1
I tried two variants as a setup that I have attached.
In Idea 1 I ran Unbound on the Asus router. I used the Swinson scripts from # 4 in the / jffs / scripts / x3mRouting / vpnclient1-route-up file after the X3mrouting entries, the same with the down entries.
Unsuccessful - always the same error message - server failure.
Then I added modprobe xt_comment to the init-start file according to Post # 237. But I just can't get it to work.
Neither variant 1 nor variant 2.
I wonder why variant 2 doesn't work. I force all traffic from the Raspberry Pi via VPN1 - so the requests from unbound on the Raspberry Pi would also have to be routed via VPN1 - but it does not work.
Since I can no longer see through all the variants here, it would be very nice if someone could explain to me again what exactly I have to do to get my setup running, either over variant1 or over variant2. Would variant2 be better because the pi 4 has more power and so we could increase the prefetch cache for unbound ?
1. Martineau script alone?
2. Martineau script and init start?
3. Edit VPNClient1-route-up and down and Martineau script?
I am totally confused.
Many thanks for the help !
Hugo
Attachments
Caesar the Dictator
Regular Contributor
Thank you to everyone who wrote and updated the rules for forwarding Unbound DNS to the tunnels of OpenVPN clients. Should users trying this process for the first time use the method in post #237?

 www.snbforums.com
www.snbforums.com
Can a similar method in this thread be adapted for Diversion (without Unbound)? Or can it be adapted to AdGuard Home which works with the methods suggested in turtoial below?

 www.snbforums.com
www.snbforums.com

Unbound - Unbound DNS VPN Client w/policy rules
I've tried this setup but with only one VPN and ads still get through. Most ads are blocked so it does appear to work until you visit an ad heavy site. You don't get any ads for any devices set not to use a VPN when you visit this site then: https://canyoublockit.com/extreme-test/? The banner...
 www.snbforums.com
www.snbforums.com
Can a similar method in this thread be adapted for Diversion (without Unbound)? Or can it be adapted to AdGuard Home which works with the methods suggested in turtoial below?

Tutorial - AdGuard Home - adblocker - Clean install on Asus Merlin (No 3rd party scripts !!!)
I have finally managed to install AdGuard Home on an Asus Router.... this is without using any special scripts. There was a previous forum post (here) on the same, but that involved installing using a custom script (that asked for your ssh login credentials, installed its own version of Samba...
 www.snbforums.com
www.snbforums.com
SomeWhereOverTheRainBow
Part of the Furniture
It is easy to adapt it to the Adguard home method 2 (or potentially method 1). I only say potentially for method one because I don't know how the iptable rule method will play out. All you have to do is tell Adguard home to use unbounds listening address and port number for dns. To get the OpenVPN to use Adguard home for DNS, you have to specify the right DNS policy that tells OpenVPN to include the router for DNS. It shouldn't be too complicated for the average user such as yourself.Thank you to everyone who wrote and updated the rules for forwarding Unbound DNS to the tunnels of OpenVPN clients. Should users trying this process for the first time use the method in post #237?

Unbound - Unbound DNS VPN Client w/policy rules
I've tried this setup but with only one VPN and ads still get through. Most ads are blocked so it does appear to work until you visit an ad heavy site. You don't get any ads for any devices set not to use a VPN when you visit this site then: https://canyoublockit.com/extreme-test/? The banner...www.snbforums.com
Can a similar method in this thread be adapted for Diversion (without Unbound)? Or can it be adapted to AdGuard Home which works with the methods suggested in turtoial below?

Tutorial - AdGuard Home - adblocker - Clean install on Asus Merlin (No 3rd party scripts !!!)
I have finally managed to install AdGuard Home on an Asus Router.... this is without using any special scripts. There was a previous forum post (here) on the same, but that involved installing using a custom script (that asked for your ssh login credentials, installed its own version of Samba...www.snbforums.com
Last edited:
Caesar the Dictator
Regular Contributor
How to set this up, all info from the thread put into one place.
This script will ensure the VPN IP is used for Unbound DNS when policy rules is set, regardless if the device is set to use the WAN or VPN. It will still work if the VPN IP ever changes or the VPN tunnel goes down, in this case, devices not set to use the VPN will use the ISP IP until the VPN starts up again.
Use PuTTY/Terminal to enter commands and WinSCP to edit scripts.
Pre-requisites:
Unbound - Running as system resolver (Only a basic install is required, you don't need to manually bind Unbound to the VPN).
X3mRouting - Option 3 installed.
DNS lookups - Forced to default gateway.
DNS in WAN tab- Connect to DNS Server automatically set to "No", DNS Server 1 set to a public resolver such as "9.9.9.9" (This is only used until Unbound starts after a reboot).
DNS in LAN tab - Not set/all set to router.
VPN client 1 - Setup and running, DNS set to diabled.
1. Run the following 2 commands to create and populate the "vpnclient1-route-up" and "vpnclient1-route-pre-down" files:
Code:sh /jffs/scripts/x3mRouting/x3mRouting.sh 1 0 WAN_IP dnsmasq=whatsmyip.comCode:sh /jffs/scripts/x3mRouting/x3mRouting.sh ALL 1 VPN_IP dnsmasq=whatismyip.com
2. Add the following line to “/jffs/scripts/x3mRouting/vpnclient1-route-up”:
Code:/jffs/scripts/unbound_via_vc1.sh start &
3. Add the following line to “/jffs/scripts/x3mRouting/vpnclient1-route-pre-down”:
Code:/jffs/scripts/unbound_via_vc1.sh stop &
4. Add the following line to "/jffs/scripts/init-start":
Code:modprobe xt_comment
5a. Go to "/jffs/scripts".
5b. Copy any existing script (to prevent a permission error).
5c. Rename the copy to “unbound_via_vc1.sh”.
5d. Delete any existing code.
5e. Copy and paste the below code into it:
Code:#!/bin/sh Check_Tun11_Con() { ping -c1 -w1 -I tun11 9.9.9.9 } Delete_Rules() { iptables-save | grep "unbound_rule" | sed 's/^-A/iptables -t mangle -D/' | while read CMD;do $CMD;done } Add_Rules(){ Delete_Rules iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000 iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000 iptables -t mangle -A OUTPUT -d "${wan0_dns##*.*.*.* }"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000 iptables -t mangle -A OUTPUT -d "${wan0_dns%% *.*.*.*}"/32 -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x8000/0x8000 iptables -t mangle -A OUTPUT -p tcp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000 iptables -t mangle -A OUTPUT -p udp --dport 53 -m comment --comment unbound_rule -j MARK --set-mark 0x1000/0x1000 } Call_unbound_manager() { /jffs/addons/unbound/unbound_manager.sh vpn="$1" } Poll_Tun11() { timer=$1 [ -z $timer ] && Post_log "Error Timeout" && exit 1 || sleep 2 Check_Tun11_Con && Add_Rules && Call_unbound_manager "1" || Poll_Tun11 "$((timer--))" } Post_log() { $(logger -st "($(basename "$0"))" $$ "$1") } [ -z "$1" ] && Post_log "Script Arg Missing" && exit 1 || Post_log "Starting Script Execution" wan0_dns="$(nvram get wan0_dns)" Delete_Rules case "$1" in start) Poll_Tun11 "150" && Post_log "Ending Script Execution" && exit 0;; stop) Call_unbound_manager "disable" && Post_log "Ending Script Execution" && exit 0;; *) Post_log "Script Arg Invalid" && exit 1;; esac
6. OPTIONAL - Add the following line to "/jffs/scripts/services-start":
(Only required if the VPN doesn't automatically start when the router is rebooted)
Code:sleep 30 && service restart_vpnclient1 &
7a. Ensure your "/jffs/scripts/services-start" file contains the following line, if not add it:
(This will ensure the script automatically starts when the router is rebooted)
Code:/jffs/addons/unbound/unbound_rpz.sh startup # Unbound_RPZ.sh
7b. (Not required anymore but kept here just in case) OPTIONAL - Add the following line to "/jffs/scripts/services-start":
(Only required if this script doesn't automatically start when the router is rebooted)
Code:sleep 30 && sh /jffs/scripts/unbound_via_vc1.sh start &
8. Reboot your router, it is now configured.
A. To manually start the script run the following command:
Code:/jffs/scripts/unbound_via_vc1.sh start
B. To check it's working, run the following command and check the IP tables are populated:
Code:iptables -nvL OUTPUT -t mangle
Ci. Run this to check it's setup correctly:
Code:ip rule
Cii. It should output like below:
Code:0: from all lookup local 9995: from all fwmark 0x1000/0x1000 lookup ovpnc1 10010: from 192.168.1.124 lookup main 10210: from 192.168.1.139 lookup ovpnc1 32766: from all lookup main 32767: from all lookup default
D. Check the VPN IP is showing as the DNS: https://dnsleak.com/
Well, I did all the instructions written in the link I share on the top except step 6. But after writing the "ip rule" command "9995: From All FWMark 0x1000 / 0x1000 Lookup OVPNC1" line is not included in the output. Which stage may I have made mistakes? @SomeWhereOverTheRainBow
Kingp1n
Very Senior Member
Well, I did all the instructions written in the link I share on the top except step 6. But after writing the "ip rule" command "9995: From All FWMark 0x1000 / 0x1000 Lookup OVPNC1" line is not included in the output. Which stage may I have made mistakes? @SomeWhereOverTheRainBow
I'm not sure if you're running x3mRouting but if you're not try installing option 3.expand...
Once you have that that installed, try running this command:
Code:
x3mRouting ALL 1 dummy dnsmasq=dummy.me (might need to change 1 to 5)I was having a similar issue with the previoius script and this pushed the missing “from all fwmark 0x1000/0x1000 lookup ovpnc1.
Well, I did all the instructions written in the link I share on the top except step 6. But after writing the "ip rule" command "9995: From All FWMark 0x1000 / 0x1000 Lookup OVPNC1" line is not included in the output. Which stage may I have made mistakes? @SomeWhereOverTheRainBow
An alternative is add the following in
vpnclient1-route-up. The rule will be created when you start openvpn client 1.
Code:
#Create RPDB rules
ip rule del prio 9995 2>/dev/null
ip rule add from 0/0 fwmark "0x1000/0x1000" table ovpnc1 prio 9995
/jffs/scripts/unbound_via_vc1.sh start &Caesar the Dictator
Regular Contributor
@Kingp1n @chongnt Many thanks for your answers. I formatted the USB and the JFFS partition and took all the steps again. This time I used the "modified unbound_via_vc1" code you wrote in @chongnt post #285 and it seems to have worked. The DNS IP address of each device accessing the Internet from WAN, OpenVPN 1 and OpenVPN 2 clients became the IP address in OpenVPN 1. Thanks again.
To check Unbound's stats, I ran the "amtm" command in PuTTY and keyed in the appropriate option, and then saw that the "DNS firewall" was disabled. Is this an expected change? Because when I first installed Unbound, that setting was enable.
Finally, I want to say this: It would be great if there was a similar guide for users of Diversion and AdGuard Home (which I shared in my post #294) or for users who are happy with DNS providers like NextDNS, Quad9, Cloudflare and AdGuard DNS (I mean users using DoT in WAN setting).
To check Unbound's stats, I ran the "amtm" command in PuTTY and keyed in the appropriate option, and then saw that the "DNS firewall" was disabled. Is this an expected change? Because when I first installed Unbound, that setting was enable.
Finally, I want to say this: It would be great if there was a similar guide for users of Diversion and AdGuard Home (which I shared in my post #294) or for users who are happy with DNS providers like NextDNS, Quad9, Cloudflare and AdGuard DNS (I mean users using DoT in WAN setting).
Similar threads
- Replies
- 16
- Views
- 765
- Replies
- 6
- Views
- 2K
- Replies
- 9
- Views
- 2K
- Replies
- 18
- Views
- 2K
- Replies
- 0
- Views
- 181
Similar threads
Similar threads
-
Unbound Redirect Internet traffic through tunnel best setting for unbound dns and vpn
- Started by Jack-Sparr0w
- Replies: 3
-
DNS works for clients but not router (in ssh terminal mode) using YazDHCP and Unbound.
- Started by CornfieldWin
- Replies: 12
-
Is it possible to add more addresses in unbound dns firewall?
- Started by Jack-Sparr0w
- Replies: 7
-
-
Unbound Tuning for gaming and VPN bind 2.0 (2026)
- Started by Jack-Sparr0w
- Replies: 16
-
-
Error with unbound and VPN all default settings set
- Started by Jack-Sparr0w
- Replies: 14
-
Unbound CVE-2025-11411 domain hijacking security vulnerability affecting up to v1.24.0
- Started by Gen10
- Replies: 1
-
-
How to get Unbound Manager to display logs in Scribe?
- Started by Davidncali001
- Replies: 15
Latest threads
-
-
-
-
-
Release ASUS ZenWiFi BT8 Firmware version 3.0.0.6.102_58394 (2026/02/04)
- Started by fruitcornbread
- Replies: 0
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!