Hello all,
I am planning to create VLANs on my PfSense appliance, however there are couple of issues I want to overcome. From what I understand I will need layer 2 switches which are VLAN aware to accomplish what I am trying to do. The added complexity is that I want one VLAN to be broadcast on my Asus Aimesh setup. How to wire this setup is something I am struggling with. Specifically where to situate my head node which is a GTX 11000.
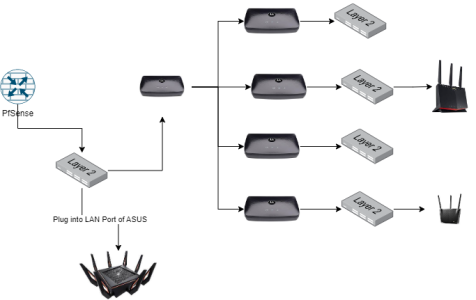
Kindly let me know if the attached diagram is possible especially putting the GTX 11000 where I am putting so that it can AIMESH with other nodes.
Also which L2 switch you would recommend for this homelab setup; I am looking for something inexpensive and functional.
Thanks in advance
I use the TP Link TL-SG108E which is 8 ports and usually runs between $25 and $30. Netgear's GS308E and GS108E (basically the same thing 308 is newer and cheaper) equivalents are nearly the same, a few less features (no LAG and less QOS options) but also usually a bit cheaper too. They each have larger ones too but obviously more expensive. TrendNET has a similar one too, any should work fine. Those are fairly basic smart switches with VLAN and some basic QOS (and in some cases LAG). If you want full features you need to look at fully managed switches.
Aimesh on the Asus without guest wireless 1 (or with guest 1 but intranet access enabled) will work with any switch, even dumb ones, it just uses VLAN 1 untagged. If you want GW1 with intranet disabled, you will need a VLAN aware switch (or at the very least, one that will pass vlan tags, many newer switches with jumbo frame support will, but it is hit or miss) like the ones above and all the links that go to the asus devices will need VLAN 1 untagged, VLAN 501 and 502 tagged, and if any are a tri-band model VLAN 503 tagged too.
You can then set any port on the switch into VLAN 501/502 (and 503 if you have it) to put wired devices into the corresponding guest network. You can also tag those VLANs to your PFsense over a trunk port.
If you want more than to just make use of the Asus built in VLANs (and their corresponding subnets and DHCP pools) you either have to get into scripting or ditch the Asus and go with VLAN aware APs. The scripting for just customizing the built in VLANs and/or IPs/DHCP pools is somewhat straightforward, if you want to assign your own VLAN IDs etc it is a lot more complex.
If you plan to run them all in AP mode then it should still create the VLANs but there will be no subnets or DHCP pools associated, you would configure those on the PFSense. In router mode it default tags the 50x VLANs out all LAN ports, I believe in AP mode it also tags them out the WAN port.
This is of course a bit of a hack, it is not true VLAN support where you can customize everything and have a lot of flexibility, so it is fit for some purposes, not others. You can of course create other VLANs on the PFsense and switches, it just won't be on the Asus unless you first route it (literally L3 routing) through the PFsense onto one of the Asus VLANs).
On the flip side, if all you want is for your Asus APs to be in one VLAN off the PFsense, that is easy, just plug them into any port on the switch and set it as an access port for that VLAN. As far as the Asus is concerned it is VLAN 1 (as long as you put them all on the same VLAN on your switch). You won't have guest wireless or LAN isolation functionality in that setup (unless you put different APs into different VLANs and used the PFSense to control communication between them, and Aimesh won't function if you do that most likely unless you can identify all the traffic needed for Aimesh and forward it between the VLANs.