Dang, lots of replies since my post on Friday. Just read them all. Thanks everyone for your input. I've tried everything suggested, no dice.
I'm pretty sure all of your AiMesh nodes need to be on some version of 3006 to have native Guest Network support. You could hack an ugly fix by binding all your IoT devices to a single node and then inserting the managed switch into the backhaul for that node and tagging all traffic passing through it as VLAN 52, but then ANYTHING that connects to that node is going to be forced onto VLAN 52.
I think you may be right.
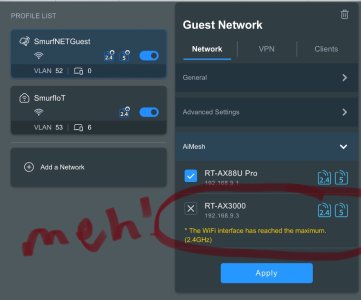
I don't believe that you need a managed switch at all. Any unmanaged switch THAT CORRECTLY PASSES VLAN TAGS will work (TP-Link definitely work, but I have no experience with Netgear), or you can factory reset the TL-SG108E to use it as an unmanaged switch. The step that you may have missed is configuring which guest networks are passed to which AiMesh nodes (different from 3004.x firmware). Select Guest Network Pro (or Network), select the IoT networks to be forwarded, select AiMesh from right column, and select desired node(s).
Tried that. Still no go. All wireless devices that connect with one of the two nodes still get the wrong IP (192.168.
2.XXX) instead of 192.168.
52.XXX). See screenshots below.
He's talking about wireless clients and he's running 3004 firmware on the nodes which I think we've established at this point from previous threads don't support Guest Network Pro. There's three separate cases we've seen so far across previous threads:
A) AiMesh nodes that don't support Guest Network Pro at all
B) AiMesh nodes that support Guest Network Pro but don't support VLAN tagging on the node Ethernet ports
C) AiMesh nodes that support both
The managed switch is going to come into play if you want to add VLAN tagging to wired clients at the node location in cases A and B. You can also use it to force all traffic going across a node Backhaul onto a specific VLAN. So whether you need the managed switch or not depends on what you're trying to accomplish. But in all cases we've seen so far I think it's pretty clear the node has no chance of supporting Guest Network Pro if it's not running 3006-revision firmware.
Based on what I'm reading, it's not just 3004, but 3.0.0.4.
386 vs. 3.0.0.4.
388. Both of my nodes are on 386 which could be the issue here.
VLAN tagging for AiMesh wireless devices works for either 3004
OR 3006 firmware AiMesh nodes when connected to a 3006 primary router with
Guest Network Pro (GNP) configured. The primary router takes care of the VLAN configuration for the AiMesh nodes — this has been the case for 3004 firmware as well for guest network 1 as well (
if you disable intranet access for guest network 1 created VLANs 102 and 103, but they were not configurable).
What you are tryiing to do with the managed switch does in fact work
IF you:
- Connect the switch to one of the downstraem LAN ports of the AiMesh node (i.e., output from the AiMesh Node).
- You properly configure the switch as described in the TP-Link community forum: Setting up VLAN tagging on ports.
This is how my TL-SG108E is configured to connect multiple VLAN 52 IoT devices. I added the switch as a proof of concept — I have successfully moved all of my IoT wired devices to the same IoT VLAN used by IoT guest network. Yes, I could have used an unmanaged switch by configuring one of the VLAN ports, but I needed to buy an extra switch anyway:
NOTE: I left port 1 configured as tagged for VLAN 1 as described at the bottom of the community forum post in order to maintain easy configuration access from the primary network.
I copied your settings identically on my TL-SG108E and still no go. Details below.
That's really the question: if he has not setup VLAN port tagging on his TL-SG108E it should be passing whatever tags are present in the traffic coming from the nodes without altering anything so I'd like to know what happens if that managed switch is used with no VLAN setup whatsoever (i.e. used as a normal switch). But can you confirm you've got/had nodes running 3004-firmware, a main router with 3006 running GNP, and the wireless clients connecting to the nodes can properly get tagged with a GNP VLAN ID other than 1?
I just tried that. Factory reset the TL-SG108E. No luck. Then I enabled VLAN support, but didn't set anything else. Same results.
If you have managed switches as workaround this means you also have Ethernet to nodes available. Not sure why you decided to pair your pfSense gateway with consumer AiMesh as AP and fix deficiencies with extra hardware. Sounds like self-inflicted complication to me. What was the idea behind this setup?
Seth has the manages switches as the work around. I'm the one with the pfSense. To answer your question, the idea behind this setup is merely a result of network changes and improvements I've made over the years:
- Dec 2014: Replaced TrendNet 802.11b router with Asus RT-AC68U.
- May 2018: Added Asus RT-AC86U. The AC-68U demoted to 1st AiMesh node.
- Apr 2020: Added PROTECTLI FW4B 4-port firewall for pfSense and changed Asus to "AP Mode*".
- Mar 2024: Added Asus RT-AX86U Pro. RT-AC86U demoted to 2nd AiMesh node.
*This is something that realy hasn't been mentioned. My RT-AX86U Pro is running in
Access Point (AP) mode, not the default
Wireless Router mode since I'm letting the pfSense handle DHCP, firewall, etc.. On that note, I came across
this post over the weekend where he states "From what I have seen (but haven't tried), it does NOT work in standalone AP mode". So maybe that has something to do with it.
ARE YOU GUYS RUNNING IN AP MODE OR WIRELESS ROUTER MODE? Maybe it matters???
Details on my setup:
- Frontier FIOS ONT > Frontier MOCA/Ethernet converter > pfSense firewall > Asus RT-AX86U Pro.
- 5 bdrm, 3400 sq. ft., 2 story house with the 3 Asus routers/nodes spread around.
- Every Asus router/node is plugged into an Ethernet jack in the wall in their respective room. All Ethernet cables terminate inside an access panel outside next to my gas meter. I have the TP-Link switch inside the access panel.
TP-Link TL-SG108E managed switch:
- Port 1: Connected to LAN port 1 on Asus RT-AX86U Pro router,
- Port 2: Connected to WAN port on Asus RT-AC86U node in the workout room.
- Port 3: Connected to WAN port on Asus RT-AC68U in guest bedroom.
Here you can see the workout room node is handing out the wrong IP address range. Should be 192.168.
52.XXX.
My TP-Link settings:
If I change the PVID on Ports 2 and 3 to "52", the nodes will become disconnected because the backhaul packets (whatever VLAN those use) can't get through anymore.
Lastly, I am retired network engineer so I have the distinct gut feeling that this entire setup simply isn't compatible so I may have to resort to putting everything on one SSID/network/subnet. I know, not best practice, but again, retired = very limited income so I can't just go out and drop a few hundred $$$ on newer, compatible devices.