alwaysCurious
New Around Here
Setup: Cable modem --> AC86U (router, WiFi off, OpenVPN Client) --> AC1900P (AP Mode) --> WiFi clients
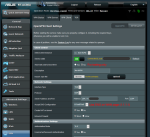
I just added an AC86U to my setup to boost OpenVPN speeds. However, my FireTV Stick (FTS) won't play Prime Videos when connected to a VPN (i.e., "You are connected to a VPN. Please disconnect..."). I expected this. When I had only the AC1900P, I created a VPN rule to redirect traffic from the FTS to the WAN iface. Everything worked.
Using the AC86U, the same rule causes all traffic from the FTS to get dropped. It connects to the network, but not the internet. Here is a summary of what I've tried:
- Restarted FTS, modem, AC86U, and AC1900P --> no internet access
- Used WiFi on AC86U --> no internet access
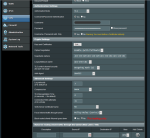
- "Block routed clients if tunnel goes down" Yes/No --> no internet access
- Turned off VPN client connection --> no internet access
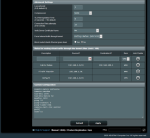
- Kept VPN connected, but removed FTS rule (i.e., it used the VPN) --> can access internet (but can't play Prime Video because of VPN connection)
- Kept VPN connected on, and changed FTS rule to explicitly use the VPN --> can access internet (but can't play Prime Video because of VPN connection)
I was able to recreate the issue with my Android phone by adding a VPN rule for it. However, doing the same with my Windows laptop (WiFi) does not recreate the issue. I am perplexed as to what this could be.
I am perplexed as to what this could be.
How can I get my FTS to bypass the VPN? Please let me know what additional information would be pertinent to add. Thanks
I just added an AC86U to my setup to boost OpenVPN speeds. However, my FireTV Stick (FTS) won't play Prime Videos when connected to a VPN (i.e., "You are connected to a VPN. Please disconnect..."). I expected this. When I had only the AC1900P, I created a VPN rule to redirect traffic from the FTS to the WAN iface. Everything worked.
Using the AC86U, the same rule causes all traffic from the FTS to get dropped. It connects to the network, but not the internet. Here is a summary of what I've tried:
- Restarted FTS, modem, AC86U, and AC1900P --> no internet access
- Used WiFi on AC86U --> no internet access
- "Block routed clients if tunnel goes down" Yes/No --> no internet access
- Turned off VPN client connection --> no internet access
- Kept VPN connected, but removed FTS rule (i.e., it used the VPN) --> can access internet (but can't play Prime Video because of VPN connection)
- Kept VPN connected on, and changed FTS rule to explicitly use the VPN --> can access internet (but can't play Prime Video because of VPN connection)
I was able to recreate the issue with my Android phone by adding a VPN rule for it. However, doing the same with my Windows laptop (WiFi) does not recreate the issue.
How can I get my FTS to bypass the VPN? Please let me know what additional information would be pertinent to add. Thanks