Wallace_n_Gromit
Senior Member

What's CNAME of your game? This DNS-based tracking defies your browser privacy defenses
Study sees increasing adoption of cloaking to bypass cookie barriers
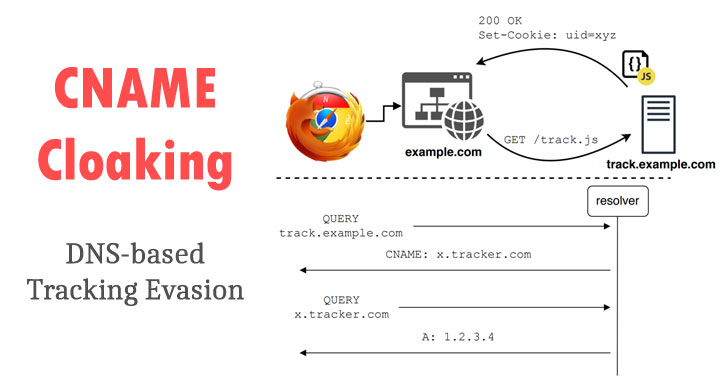
Online Trackers Increasingly Switching to Invasive CNAME Cloaking Technique
Online Trackers Increasingly Switching to Invasive DNS-based CNAME Cloaking Technique
 thehackernews.com
thehackernews.com
Ultimately what caught my eye about this issue is that 3rd parties (advertising/analytics and by extension even malware vendors--some good guys can go bad) can with the cooperation/collusion of the website (isn't that what they do now anyway to monetize your visit?), in effect plant cookies as first parties thus effectively negating any 3rd party cookie blocking and under the radar of adblocking, analytics blocking software (that rely upon 3rd party "fixed hostname-based block lists").
BUT THERE'S MORE!The researchers found this technique currently in use on a total of 10,474 websites. And of the top 10,000 websites overall, 9.98% — 1 in 10 — of those top 10,000 are currently employing this form of CNAME tracking, cloaking, subdomain collusion.
But perhaps an unintended consequence of this feature can, additionally, due to it's nature, in the hands of bad actors, effectively authenticate/login/impersonate YOU. Since their cookies are part of the hosting websites domain/subdomain and if there exists a still-valid authentication cookie (you haven't explicitly logged off); that same 3rd party now has access to ALL COOKIES, including the authenticating cookies, from that website you visit.
[Subject is discussed 1:26:40 into Podcast]
The Podcast Notes about CNAME Collusion issue begin on page 7
Security Now! #808 - 03-02-21 - CNAME Collusion (grc.com)
Countermeasures
In response to a report that a tracker was using CNAMEs to circumvent privacy blocklists, uBlock Origin released an update for its Firefox version that thwarts CNAME cloaking. The extension blocks requests to CNAME trackers by resolving the domain names using the [browser's own] browser.dns.resolve API method to obtain the last CNAME record (if any) before each request is sent. Subsequently, the extension checks whether the domain name matches any of the rules in its blocklists, and blocks requests with matching domains while adding the outcome to a local cache. Although uBlock Origin also has a version for Chromium-based browsers, the same defense cannot be applied because Chromium-based browser extensions do not have access to an API to perform DNS queries. As such, at the time of this writing, it is technically impossible for these extensions to block requests to trackers that leverage CNAME records to avoid detection. uBlock Origin for Chrome, which does not have an explicit defense for CNAME-based tracking, still manages to block several trackers. This is because the requests to the trackers matched an entry of the blocklist with a URL pattern that did not consider the hostname. Unfortunately, it is fairly straightforward for the tracker to circumvent such a fixed rule-based measure, e.g.by randomizing the path of the tracking script and analytics endpoint, as is evidenced by the various trackers that could only be blocked by the uBlock Origin version on Firefox
On page 10 of the show notes a chart does show that uBlock Origin and the NextDNS CNAME blocklist are partially able to mitigate this behavior.
Attachments
Last edited:

