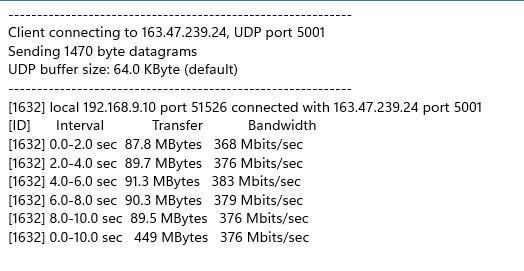
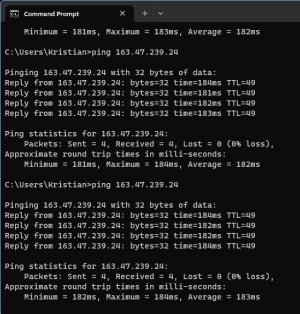
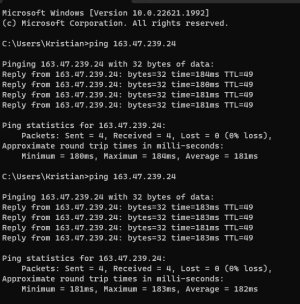
Thanks for the prompt reply! The "old" router is still up and running while I'm setting up the AX88U so easy to grab the values. An old AC1900P has been providing 2.4 GHz for the last few weeks.
Edit: The nvram commands don't see to be working. Perhaps I need to clarify, I'm trying to get the information from the AC86U running WireGuard Session Manager.
View attachment 54429
ooh, sorry... I didnt read your post properly. so you cant get the keys that way then.
I dont remember how much you could get the keys from the CLI/GUI but all config files should be in
/opt/etc/wireguard.d/ both wg21.conf and your client configs.
in wg21.conf [interface] section you should find the PrivateKey= directive. this would be your [wgs1_priv]
in wg21.conf [Peer] section you should find each PublicKey= directive (for each peer). this would be your [wgs1_cX_pub]
in wg21.conf [Peer] section you should find each PresharedKey= directive (for each peer). this would be your [wgs1_cX_psk]
for the rest of the keys, they are actually not needed on your server, only needed if you ever need to generate new config files... but I would recommend to update these as well.
in the same folder you should find all client configs that wgm have created, so you need to open each one.
on i.e. peer1.conf [interface] section you should find the PrivateKey= directive. this would be your [wgs1_c1_priv]
in peer1.conf [Peer] section you should find PublicKey= directive (for wgs1). this would be your [wgs1_pub] (this would be same for all peers, so no need fetch for all)
on i.e. peer2.conf [interface] section you should find the PrivateKey= directive. this would be your [wgs1_c2_priv]
continue like this until you have collected all keys needed... then you can update the keys on your new router, using "nvram set ..." commands from post #1.