Router: GT-AX11000
Firmware: 3004.388.11_0_rog
No idea why this is happening. It works for a few days then I will restart my router or come in and change a totally unrelated setting and the guest network isn't able to reach the DNS suddenly. My last router, an AC68U never had this intermittent issue, it just connected to my DNS through the guest.
I thought I resolved the issue when I realized I forgot to disable my router firewall, I disabled it and it worked for awhile, but now the issue has started again and it's so damn annoying.
The DNS is my pihole which permits all origins


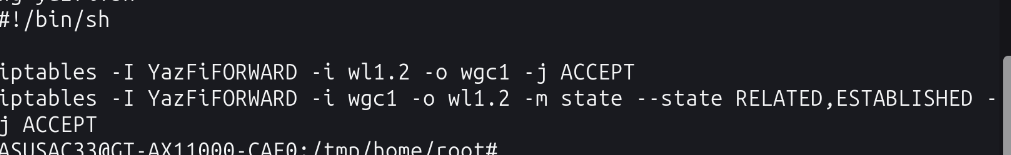
Even tried to add a stupid rule that would hopefully do something but no joy:

During the time it doesn't work I can ping something like 1.1.1.1 but if i try to say nslookup google.com 192.168.50.8 - just straight errors. How can I force my guest to use the pi-hole and figure out what's causing the issue? I thought this is what YazFi was for, pinhole access for DNS? Why after power cycling my router a thousand times it starts working again?
Firmware: 3004.388.11_0_rog
No idea why this is happening. It works for a few days then I will restart my router or come in and change a totally unrelated setting and the guest network isn't able to reach the DNS suddenly. My last router, an AC68U never had this intermittent issue, it just connected to my DNS through the guest.
I thought I resolved the issue when I realized I forgot to disable my router firewall, I disabled it and it worked for awhile, but now the issue has started again and it's so damn annoying.
The DNS is my pihole which permits all origins
Even tried to add a stupid rule that would hopefully do something but no joy:
During the time it doesn't work I can ping something like 1.1.1.1 but if i try to say nslookup google.com 192.168.50.8 - just straight errors. How can I force my guest to use the pi-hole and figure out what's causing the issue? I thought this is what YazFi was for, pinhole access for DNS? Why after power cycling my router a thousand times it starts working again?