v1rt
Occasional Visitor
My firewall script never worked really well. I configured it earlier this year. Today, I need help again because it's still not working well. I'm wondering why son's network connection doesn't get killed even when the router has firewall rules to block the traffic on certain time. Here is my firewall-start script
admin@RT-AC68U-6000:/jffs/scripts# cat firewall-start
#!/bin/sh
# Locate both "RELATED,ESTABLISHED" and "INVALID" rules to place the Inserts after
InsLoc=`iptables -nvL FORWARD --lin | grep -A 1 -i "RELATED,ESTABLISHED" | tail -n 1 | awk '{ print $1 }'`
if [ "x$InsLoc" == "x" ]
then
# echo "Rule RELATED,ESTABLISHED not found"
# Add rule to continue existing connections
iptables -I FORWARD 1 -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
InsLoc=2
fi
#
InsLoc1=`iptables -nvL FORWARD --lin | grep -A 1 -i "INVALID" | tail -n 1 | awk '{ print $1 }'`
if [ "x$InsLoc1" == "x" ]
then
# echo "Rule INVALID not found"
# Add rule to Drop unexpected traffic
iptables -I FORWARD $InsLoc -m conntrack --ctstate INVALID -j DROP
InsLoc1=`expr $InsLoc + 1`
fi
#
if [ $InsLoc1 -gt $InsLoc ]
then
# use which ever comes last
InsLoc=$InsLoc1
fi
echo "InsLoc=$InsLoc"
#
# League of Legends Game Client
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# Patcher and Maestro
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 2099 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 5223 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 5222 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 02:30 --timestop 08:00 --weekdays Fri,Sat -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 12:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 8088 Spectator Mode
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
iptables -I FORWARD $InsLoc -i br0 -o eth0 -m tcp -p tcp --dport 5222 -j ACCEPT
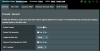
Please see attached screenshots of my configuration. If I missed a setting, please let me know. My son's computer is connected to a lan port.
Firmware is Firmware:378.51
I've also played with the timezone because I noticed something weird. I tried UTC hoping it would work but still didn't. Right now the time here in Chicago is 8:58am and the time on my router is Sat Dec 19 08:58:35 UTC 2015
admin@RT-AC68U-6000:/jffs/scripts# cat firewall-start
#!/bin/sh
# Locate both "RELATED,ESTABLISHED" and "INVALID" rules to place the Inserts after
InsLoc=`iptables -nvL FORWARD --lin | grep -A 1 -i "RELATED,ESTABLISHED" | tail -n 1 | awk '{ print $1 }'`
if [ "x$InsLoc" == "x" ]
then
# echo "Rule RELATED,ESTABLISHED not found"
# Add rule to continue existing connections
iptables -I FORWARD 1 -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
InsLoc=2
fi
#
InsLoc1=`iptables -nvL FORWARD --lin | grep -A 1 -i "INVALID" | tail -n 1 | awk '{ print $1 }'`
if [ "x$InsLoc1" == "x" ]
then
# echo "Rule INVALID not found"
# Add rule to Drop unexpected traffic
iptables -I FORWARD $InsLoc -m conntrack --ctstate INVALID -j DROP
InsLoc1=`expr $InsLoc + 1`
fi
#
if [ $InsLoc1 -gt $InsLoc ]
then
# use which ever comes last
InsLoc=$InsLoc1
fi
echo "InsLoc=$InsLoc"
#
# League of Legends Game Client
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p udp --dport 5000:5500 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# Patcher and Maestro
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8393:8400 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 2099 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 2099 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 5223 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5223 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 5222 TCP - PVP.Net
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 02:30 --timestop 08:00 --weekdays Fri,Sat -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 5222 -m time --timestart 12:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
# 8088 Spectator Mode
iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Mon,Tue,Wed,Thu,Fri,Sat,Sun -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Fri,Sat --kerneltz -j DROP
#iptables -I FORWARD $InsLoc -i br0 -o eth0 -p tcp --dport 8088 -m time --timestart 22:00 --timestop 08:00 --weekdays Sun --kerneltz -j DROP
iptables -I FORWARD $InsLoc -i br0 -o eth0 -m tcp -p tcp --dport 5222 -j ACCEPT
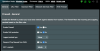
Please see attached screenshots of my configuration. If I missed a setting, please let me know. My son's computer is connected to a lan port.
Firmware is Firmware:378.51
I've also played with the timezone because I noticed something weird. I tried UTC hoping it would work but still didn't. Right now the time here in Chicago is 8:58am and the time on my router is Sat Dec 19 08:58:35 UTC 2015