Script to terminate any access to the Internet including stopping existing connections.
This script should be better for performance than the original script. It only has 2 or 4 rules before the "RELATED,ESTABLISHED" rule to check during the day. It also handles school days and weekends with different times.
Remember to edit the script to replace my examples for time, IP address list and mac address list.
Do a "chmod 750 time-restrict-by-ip.sh" to make the file executable and remove the world write permission.
You may find the following commands useful while testing
List the iptables chains by
iptables -nvL FORWARD --lin
iptables -nvL dropkids --lin
To delete the first rule in the FORWARD chain
iptables -D FORWARD 1
Remember that the rules get renumbered after each delete, so list the table just before you delete a rule.
All the rules in the chain dropkids get flushed (deleted) by the script before adding the rules, so no need to delete of it's rules.
Until you copy the file into place in /jffs/scripts/firewall-start, you can reboot the router, and your changes will be undone.
Once tested, copy to file to /jffs/scripts/firewall-start script and it will last over a reboot.
[EDIT to add fix]
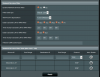
Found problem the router we have is too good! It is optimizing a streaming connection.
What you need to do is disable NAT Acceleration under "LAN" then tab "Switch Control".
Then if you check under "tools" it should say HW acceleration is Disabled (by user)
Reboot and it now works as expected.
This post talks about performance hit of turning off acceleration.
http://forums.smallnetbuilder.com/showpost.php?p=63184&postcount=21
Following code is also in attached zip
Code:
#!/bin/sh
# uncomment next line to see commands as they are read from this file
# set -v
# uncomment next line to see commands as they are executed
# set -x
#
# this script is to turn off machines Internet access by IP address at night
# it will break existing connections.
# if the kid is smart enough to change IP address, the mac address will prevent controlling an existing connection
# IP version 6 is not addressed here
#
# start and stop times for school days (hh:mm)
SchoolNiteTime=21:00
SchoolMornTime=06:59
# comma delimit list of school days
SchoolDays="Mon,Tue,Wed,Thu,Fri,Sat,Sun"
#
# start and stop times for non school days
WeekendNiteTime=23:00
WeekendMornTime=05:59
# comma delimit list of non school days ("" means not used )
# if a day is not in either SchoolDays or WeekendDays list, then no restriction on the missing day
WeekendDays=""
#
# Change line below to the space delimited list of IP addresses of the kids machines
StaticIPList="192.168.1.101 192.168.1.102"
#
# the mac restriction does not totally break connections,
# but prevents kid who change IP address from starting new connections.
# Change line below the space delimited list of mac address of the kids machines ("" means not used )
MaCList="12:34:56:78:9a:bc"
# define a user chain and fill with rules
iptables -N dropkids
iptables -F dropkids
# first by MaCList
for MaC in $MaCList
do
iptables -I dropkids 1 -m mac --mac-source $MaC -j DROP
done
# then the StaticIPList
for StaticIP in $StaticIPList
do
iptables -I dropkids 1 -s $StaticIP -j DROP
iptables -I dropkids 1 -d $StaticIP -j DROP
done
#
iptables -I FORWARD 1 -m time --timestart $SchoolNiteTime --days $SchoolDays -j dropkids
iptables -I FORWARD 1 -m time --timestop $SchoolMornTime --days $SchoolDays -j dropkids
# optional Weekend restriction
if test "x$WeekendDays" != "x"
then
iptables -I FORWARD 1 -m time --timestart $WeekendNiteTime --days $WeekendDays -j dropkids
iptables -I FORWARD 1 -m time --timestop $WeekendMornTime --days $WeekendDays -j dropkids
fi