Thanks, its very similar to other tutorials that I read during these days.
My problem is that even if I'm really familiar with network & security, there are a lot of aspects more related to the linux word that I don't know and I feel myself lost trying to give an explanation.
For example, what are the "chains"? If I issue the following command on my router running Skynet:
iptables -L | grep Chain
I get the following output:
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
Chain FORWARD (policy DROP 0 packets, 0 bytes)
Chain OUTPUT (policy ACCEPT 313K packets, 99M bytes)
Chain ACCESS_RESTRICTION (0 references)
Chain FUPNP (0 references)
Chain INPUT_ICMP (1 references)
Chain NSFW (1 references)
Chain PControls (0 references)
Chain PTCSRVLAN (1 references)
Chain PTCSRVWAN (1 references)
Chain SECURITY (1 references)
Chain default_block (0 references)
Chain logaccept (0 references)
Chain logdrop (8 references)
What is the scope/use of each chain? I read something on this:
https://www.digitalocean.com/commun...dive-into-iptables-and-netfilter-architecture
and
https://wiki.archlinux.org/index.php/iptables
but for AsusWRT I didn't find a specific howto with the chain traversal order for the possible flows that can exist.
If I issue a "iptables -L " I got an output only partially readable for me like this:
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- tun21 any anywhere anywhere
0 0 ACCEPT udp -- any any anywhere anywhere udp dpt:1194
0 0 logdrop icmp -- eth0 any anywhere anywhere icmp echo-request
218K 42M ACCEPT all -- any any anywhere anywhere state RELATED,ESTABLISHED
1344 58410 logdrop all -- any any anywhere anywhere state INVALID
58144 9797K PTCSRVWAN all -- !br0 any anywhere anywhere
What is the "target" column?
What is the column after "destination"?
If I issue the same command with -vv after the first part related to the chains I got something more similar to an enterprise approach with rules in sequence, but even there, I have many dark points:
Table `filter'
Hooks: pre/in/fwd/out/post = ffffffff/0/818/f18/ffffffff
Underflows: pre/in/fwd/out/post = ffffffff/780/e80/f18/ffffffff
Entry 0 (0):
SRC IP: 0.0.0.0/0.0.0.0
DST IP: 0.0.0.0/0.0.0.0
Interface: `tun21'/XXXXXX..........to `'/................
Protocol: 0
Flags: 00
Invflags: 00
Counters: 0 packets, 0 bytes
Cache: 00000000
Target name: `' [40]
verdict=NF_ACCEPT
According to the previous http link there is not only the filter table but I didn't find a command to show alla tables present so I can only search the ones listed in the link so:
filter
nat
mangle
raw
table security seems to be not existent in AsusWRT
What is the number between parentesis after the one that seems to be the rule ID?
What are Hooks and Underflows?
What is "Invflags"? (Inverse flag, related to SPI?)
What are the "Target name", "verdict" and "Match name" fields that may appear in some rules?
Also, when an iptables command is issued I see that are always present the following options that I don't know how to use/manage:
- Chain related, so the new/append/delete/check
- Match (-m) that seems to be something mandatory that tells iptables whats coming next, so if the rule that is going to be set will match destination port or state or ip address or whatever
- Jump (-j) that seems to be something that tells the kernel that after having matched the rule it must jump to another section. That look strange because I expect that there will be the "first match" behavior.
Where have I to put a rule if for example I want to drop all packet to/from internet coming from/to a specific internal host except for some specific sourceIP-destinationIP-SourcePort-DestinationPort sets? Which Table& Chain? I can think that the table is "filter" and the chain is "input"
What kind of match/jump? If I want to log all dropped packet only for that specific host, what have I to do?
I tried to issue a sh /jffs/scripts/firewall stats
but I don't find any of the autoban IP in any rules of all 4 tables, nor with ip address than under the Blacklist label used in the ipset.
I used these commands:
iptables -vL (or -vvL) -t filter
iptables -vL (or -vvL) -t nat
iptables -vL (or -vvL) -t mangle
iptables -vL (or -vvL) -t raw
even using | grep with the IP address or the keywords
Blacklist
BanMalware
Skynet (that from ipsets seems to be a composite objects like group of groups"
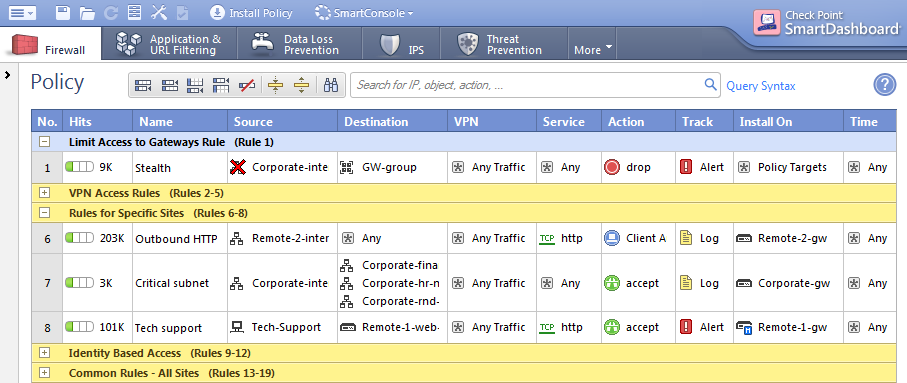
To close that very long post (I apologize for that), with enterprise firewalls and their GUI its really easy to do that than with iptables. You have simply to put a permit rule for each allowed flow, add nat if needed, and add a drop rule for specific host with log enabled or relay on the "any drop" rule that every serious enterprise firewall must be set up with. Then you can see logs with another application and search or do statistics as you want.
With iptables it seems a frustrating nightmare, I like to know exactly what I'm doing and I have a lot to walk to reach even a just decent knowledge. There are plenty of pages with explanations but not a single one that explains all in a clear order with schemas and whatelse. Building a puzzle in which every piece is almost new is really challenging