Preskitt.man
Senior Member
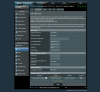
I installed 384.11-2. I then went to the WAN DNS page to implement DNSSEC. There was this message underneath the select box for DNS Privacy Protocol:
Your router's DHCP server is configured to provide a DNS server that's different from your router's IP address. This will prevent clients from using the DNS Privacy servers."
The WAN page currently point DNS1/2 to 1.1.1.1 and 1.0.0.1
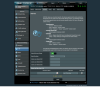
I went over to the DHCP page, and DNS Server1/2 also pointed 1.1.1.1 and 1.0.0.1.
What am I missing?
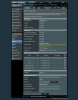
Your router's DHCP server is configured to provide a DNS server that's different from your router's IP address. This will prevent clients from using the DNS Privacy servers."
The WAN page currently point DNS1/2 to 1.1.1.1 and 1.0.0.1
I went over to the DHCP page, and DNS Server1/2 also pointed 1.1.1.1 and 1.0.0.1.
What am I missing?