Leo Martin Lim
Occasional Visitor
Hi guys,
I have been a victim of prolonged hacking, intimidation, disruption for 3 years... this is personal hacks. the hacker(s) always tries to disrupt what i am doing.
so here's the latest hack.
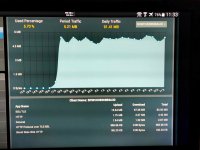
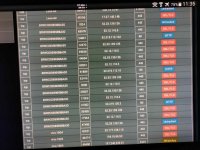
below is the print out of netstat with "display listening server sockets" from my asus RT-AX56U.
the first 2 lines with yellow font are very suspicous open ports. from what i understand it's not by asus-merlin.
i have tried factory reset, update firware, and asus firmware restoration utility. it was still there. after i reported to asus via "feedback button" it was gone for a couple days.
and it came back later. i also tried to port scan from my mobile to router, those ports ware not opened.
on the device/computer site, in this case macbook air, my wifi usage is being disrupted constantly on daily basis. it's like your current connection in your prefered network being clicked and becomes deactivated in your menu bar. (not wifi button). i have to click my ssid again to get connected. this drives me nuts after awhile.
i recently moved to mac, thinking that it's a safe platform. sigh....
on windows things are worse... they can BSOD your computer and restart without any SSD/HDD to boot. also manipulate your touchpad/trackpad becomes erratic.
i need help...
thank you,
Martin.
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 192.168.50.1:49152 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:49152 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:5152 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:18017 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:47753 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:7788 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.1.1:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8888 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:8443 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:5916 0.0.0.0:* LISTEN
udp 12480 0 127.0.0.1:45064 0.0.0.0:*
udp 0 0 0.0.0.0:9999 0.0.0.0:*
udp 0 0 127.0.0.1:42000 0.0.0.0:*
udp 0 0 0.0.0.0:46354 0.0.0.0:*
udp 0 0 127.0.0.1:52000 0.0.0.0:*
udp 0 0 127.0.0.1:42032 0.0.0.0:*
udp 0 0 127.0.1.1:53 0.0.0.0:*
udp 0 0 127.0.0.1:53 0.0.0.0:*
udp 0 0 192.168.50.1:53 0.0.0.0:*
udp 0 0 0.0.0.0:67 0.0.0.0:*
udp 0 0 0.0.0.0:18018 0.0.0.0:*
udp 0 0 0.0.0.0:7788 0.0.0.0:*
udp 0 0 0.0.0.0:1900 0.0.0.0:*
udp 0 0 0.0.0.0:1900 0.0.0.0:*
udp 0 0 127.0.0.1:38000 0.0.0.0:*
udp 0 0 0.0.0.0:59000 0.0.0.0:*
udp 0 0 127.0.0.1:37000 0.0.0.0:*
udp 0 0 127.0.0.1:58000 0.0.0.0:*
udp 0 0 127.0.0.1:59032 0.0.0.0:*
udp 0 0 127.0.0.1:47000 0.0.0.0:*
udp 0 0 127.0.0.1:47032 0.0.0.0:*
udp 0 0 127.0.0.1:45000 0.0.0.0:*
udp 0 0 127.0.0.1:45032 0.0.0.0:*
udp 0 0 0.0.0.0:5353 0.0.0.0:*
udp 0 0 127.0.0.1:43000 0.0.0.0:*
udp 0 0 127.0.0.1:61689 0.0.0.0:*
raw 0 0 0.0.0.0:2 0.0.0.0:* 2
raw 0 0 ::%2032824:58 ::%542280:* 58
Active UNIX domain sockets (only servers)
Proto RefCnt Flags Type State I-Node Path
unix 2 [ ACC ] STREAM LISTENING 3082 /var/run/protect_srv_socket
unix 2 [ ACC ] STREAM LISTENING 7197 /var/conf_serv_sock
unix 2 [ ACC ] STREAM LISTENING 5953 /var/run/cfgmnt_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 3148 /var/run/bsd_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 1868 /var/run/lldpd.socket
unix 2 [ ACC ] STREAM LISTENING 3155 /var/run/wlcnt_socket
unix 2 [ ACC ] STREAM LISTENING 6283 /var/run/rast_internal_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 2699 /var/run/avahi-daemon/socket
unix 2 [ ACC ] STREAM LISTENING 3480 /var/run/amas_lib_socket
unix 2 [ ACC ] STREAM LISTENING 2741 /var/run/nt_actMail_socket
unix 2 [ ACC ] STREAM LISTENING 695 /tmp/ps_sock
unix 2 [ ACC ] STREAM LISTENING 6102 /var/run/rast_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 1002 /var/run/netool_socket
unix 2 [ ACC ] STREAM LISTENING 1020 /var/run/nt_center_socket
I have been a victim of prolonged hacking, intimidation, disruption for 3 years... this is personal hacks. the hacker(s) always tries to disrupt what i am doing.
so here's the latest hack.
below is the print out of netstat with "display listening server sockets" from my asus RT-AX56U.
the first 2 lines with yellow font are very suspicous open ports. from what i understand it's not by asus-merlin.
i have tried factory reset, update firware, and asus firmware restoration utility. it was still there. after i reported to asus via "feedback button" it was gone for a couple days.
and it came back later. i also tried to port scan from my mobile to router, those ports ware not opened.
on the device/computer site, in this case macbook air, my wifi usage is being disrupted constantly on daily basis. it's like your current connection in your prefered network being clicked and becomes deactivated in your menu bar. (not wifi button). i have to click my ssid again to get connected. this drives me nuts after awhile.
i recently moved to mac, thinking that it's a safe platform. sigh....
on windows things are worse... they can BSOD your computer and restart without any SSD/HDD to boot. also manipulate your touchpad/trackpad becomes erratic.
i need help...
thank you,
Martin.
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 192.168.50.1:49152 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:49152 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:5152 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:18017 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:47753 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:7788 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.1.1:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8888 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN
tcp 0 0 192.168.50.1:8443 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:5916 0.0.0.0:* LISTEN
udp 12480 0 127.0.0.1:45064 0.0.0.0:*
udp 0 0 0.0.0.0:9999 0.0.0.0:*
udp 0 0 127.0.0.1:42000 0.0.0.0:*
udp 0 0 0.0.0.0:46354 0.0.0.0:*
udp 0 0 127.0.0.1:52000 0.0.0.0:*
udp 0 0 127.0.0.1:42032 0.0.0.0:*
udp 0 0 127.0.1.1:53 0.0.0.0:*
udp 0 0 127.0.0.1:53 0.0.0.0:*
udp 0 0 192.168.50.1:53 0.0.0.0:*
udp 0 0 0.0.0.0:67 0.0.0.0:*
udp 0 0 0.0.0.0:18018 0.0.0.0:*
udp 0 0 0.0.0.0:7788 0.0.0.0:*
udp 0 0 0.0.0.0:1900 0.0.0.0:*
udp 0 0 0.0.0.0:1900 0.0.0.0:*
udp 0 0 127.0.0.1:38000 0.0.0.0:*
udp 0 0 0.0.0.0:59000 0.0.0.0:*
udp 0 0 127.0.0.1:37000 0.0.0.0:*
udp 0 0 127.0.0.1:58000 0.0.0.0:*
udp 0 0 127.0.0.1:59032 0.0.0.0:*
udp 0 0 127.0.0.1:47000 0.0.0.0:*
udp 0 0 127.0.0.1:47032 0.0.0.0:*
udp 0 0 127.0.0.1:45000 0.0.0.0:*
udp 0 0 127.0.0.1:45032 0.0.0.0:*
udp 0 0 0.0.0.0:5353 0.0.0.0:*
udp 0 0 127.0.0.1:43000 0.0.0.0:*
udp 0 0 127.0.0.1:61689 0.0.0.0:*
raw 0 0 0.0.0.0:2 0.0.0.0:* 2
raw 0 0 ::%2032824:58 ::%542280:* 58
Active UNIX domain sockets (only servers)
Proto RefCnt Flags Type State I-Node Path
unix 2 [ ACC ] STREAM LISTENING 3082 /var/run/protect_srv_socket
unix 2 [ ACC ] STREAM LISTENING 7197 /var/conf_serv_sock
unix 2 [ ACC ] STREAM LISTENING 5953 /var/run/cfgmnt_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 3148 /var/run/bsd_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 1868 /var/run/lldpd.socket
unix 2 [ ACC ] STREAM LISTENING 3155 /var/run/wlcnt_socket
unix 2 [ ACC ] STREAM LISTENING 6283 /var/run/rast_internal_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 2699 /var/run/avahi-daemon/socket
unix 2 [ ACC ] STREAM LISTENING 3480 /var/run/amas_lib_socket
unix 2 [ ACC ] STREAM LISTENING 2741 /var/run/nt_actMail_socket
unix 2 [ ACC ] STREAM LISTENING 695 /tmp/ps_sock
unix 2 [ ACC ] STREAM LISTENING 6102 /var/run/rast_ipc_socket
unix 2 [ ACC ] STREAM LISTENING 1002 /var/run/netool_socket
unix 2 [ ACC ] STREAM LISTENING 1020 /var/run/nt_center_socket