Thanks Colin and Marco!

Colin, that is really interesting, I wonder if it may have been a coincidence, because today I ran IG again, and the connection was up for 71 minutes, before it suddenly died. I saved the new log and here it is:
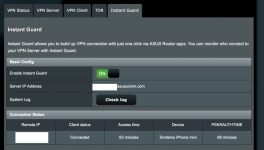
https://pastebin.com/CatCFPS7 71 minutes alive
INTERESTING FINDS AT FIRST GLANCE:
1) REKEY JOBS ARE CREATED AT 43minutes
After 43 minutes my asus router starts creating rekey-jobs for Instant Guard, and then 4 minutes after that rekeying for the router itself. which I understand is an effort to renew the lease before it runs out and keep my conenction alive?
Code:
Mar 29 10:58:07 08[KNL] creating rekey job for CHILD_SA ESP/0x09dac318/Y.Y.Y.Y (IPHONE INSTANT GUARD CLIENT ON 4G)\
Mar 29 10:58:07 07[IKE] CHILD_SA Host-to-Net\{2\} established with SPIs c796cf42_i 0d643f0b_o and TS 0.0.0.0/0 === 10.10.10.1/32\
Mar 29 11:02:28 07[KNL] creating rekey job for CHILD_SA ESP/0xceda57cb/X.X.X.X (ASUS ROUTER VPN SERVER)
2) DELETE JOB CREATED AT 60minutes
Then PRECISELY at the 60minutes mark it creates a Delete job, which doesn't run succesfully, for some reason.
Code:
Mar 29 11:13:05 07[KNL] creating delete job for CHILD_SA ESP/0xceda57cb/X.X.X.X (ASUS ROUTER VPN SERVER)\
Mar 29 11:13:05 07[IKE] closing expired CHILD_SA Host-to-Net\{1\} with SPIs ceda57cb_i 09dac318_o and TS 0.0.0.0/0 === 10.10.10.1/32\
Mar 29 11:13:05 07[IKE] sending DELETE for ESP CHILD_SA with SPI ceda57cb\
Mar 29 11:13:05 08[KNL] creating delete job for CHILD_SA ESP/0x09dac318/Y.Y.Y.Y (IPHONE INSTANT GUARD CLIENT ON 4G)\
Mar 29 11:13:05 05[JOB] CHILD_SA ESP/0x09dac318/Y.Y.Y.Y (IPHONE INSTANT GUARD CLIENT ON 4G) not found for delete
"Child (...) Not found for delete". Is it a bug that the delete job didn't manage to kill my connection precisely at 60 minutes? It wanted to kill the connection, but couldn't for some reason. Was the reason me who artifically and unintentionally interrupted the Delete Job because frantically was opening webpages on my phone from the 59th minute? (I did that to get the precise moment the connection dies) Maybe it wasnt so smart to unintentionally interrupt the delete job like that.
I'll try one more time now and see if it dies exactly on the 60 minute mark, only this time I wont be unintentionally interrupting anything, I'll just look at the connection status in my router and watch it die out.
3) THE CONNECTION IS FINALLY KILLED AT 71minutes
Finally the connection is killed at 71 minutes, rather unceremoniously. It does what i'ts supposed to to send dpd request, genereate Information request, sending the packet from router to instant guard on my phone, and then boom, DPD check times out, and the connection is killed. Weird, and so random, no?
Code:
Mar 29 11:24:24 08[NET] sending packet: from X.X.X.X (ASUS ROUTER VPN SERVER)[4500] to Y.Y.Y.Y (IPHONE INSTANT GUARD CLIENT ON 4G)[22846] (92 bytes)\
Mar 29 11:24:34 06[IKE] sending DPD request\
Mar 29 11:24:34 06[ENC] generating INFORMATIONAL_V1 request 1480663402 [ HASH N(DPD) ]\
Mar 29 11:24:34 06[NET] sending packet: from X.X.X.X (ASUS ROUTER VPN SERVER)[4500] to Y.Y.Y.Y (IPHONE INSTANT GUARD CLIENT ON 4G)[22846] (92 bytes)\
Mar 29 11:24:44 05[JOB] DPD check timed out, enforcing DPD action\
Mar 29 11:24:44 05[CFG] lease 10.10.10.1 by '2B0FD7355F4F4F8CAF52CC440EE471BA' went offline
MORE INTERESTING FINDS
Code:
\f0\fs24 \cf0 Mar 29 10:12:28 00[DMN] Starting IKE charon daemon (strongSwan 5.7.2, Linux 4.1.52, armv7l)\
1) INSTANT GUARD RUNS STRONGSWANS IPSEC IMPLEMENTATION
Maybe this is a given, and everybody knew this. I guess you knew this since you linked to strongswan... I'm silly haha. I'm not sure if the fact that IG uses Strongswan means anything, but from the link you sent Colin, it says there that
Strongswans default TIME ALIVE for Ipsec is 1 hour. So maybe it is by design, and /or maybe Asus "forgot" to remove the 1hour limitation? Or maybe they want it there, like you said to save battery?
2) IKE_SA LIFETIME AND REAUTHENTICATION
This part is interesting, as the log specifies a a scheduled reauthentication of 2h49m (10199s) and a maximum IKE_SA lifetime of 2h59m(10739s)… Does this have something to do with the Delete Job signal that happens after precisely 60 minutes? Is it supposed to last almost 3 hours? Or is this something completely different? You find them on line 74 and 75 in pastebin.
Code:
Mar 29 10:13:05 08[IKE] scheduling reauthentication in 10199s
Mar 29 10:13:05 08[IKE] maximum IKE_SA lifetime 10739s
SIDENOTES:
CUSTOMER SUOPPORT
I called ASUS customer support, btw... they didn't know anything, and hadn't even used Instant Guard themselves... they assumed it should work longer than 60 minutes, but she didn't know for sure. Ugh... customer support always frustrates me, they rarely know the answer to anything, do they?
CONFIGURE IPSEC MYSELF?
Is there a way for the user to configure how asuswrt-merlin handles IPSec ie increase the leaste to longer than 60 minutes? or is that entirely up to ASUS developers?
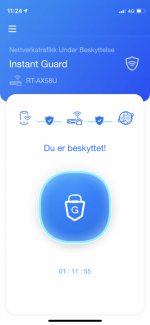
Text in attached photo:
In the photo "Du er besktyttet!" means "You are protected". It's norwegian
**** UPDATE 1.5 hours later********
https://pastebin.com/aLcQTuRj ( 63 MINUTES ALIVE)
Ran another Instant Guard session, and this time it lived for 63 minutes before dying. I didn't touch my phone for the entire session, but watched the connection from the router Instant Guard connection status page.
Again, as per your observation Colin, the Dele Job is created presicely 60 minutes after session start, but the time it takes to kill the session varies a lot, and I don't know on what. Previously it took 11 minutes to kill the connection, and now only 3 minutes.