SO - - - A question;
I have a device that can't be trusted to have internet access. I want to block all internet access to this thing from the router.
BUT. . . I want to access the unit via a VPN connection (from the other side of the planet).
I have set up OpenVPN, and I can successfully dial into my network. Without restrictions in place, I can access the "Device that I don't trust".
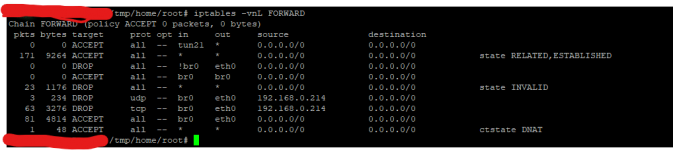
However, if I use Network Services Filter to block this device (using it's IP address) OR if I do "Block Internet Access" from the "Client Status Page" (under network map); The VPN connection is also blocked.
I suspect the block is caused by the fact that the VPN'd computer has a 10.8.x.x assigned address; rather than the 192.168.x.x address assigned to "Device that I don't trust".
Any idea how to work around this?
For one device, filter ALL traffic, except from two subnets? (i.e. 192.168.x.x and 10.8.x.x)
PS: I did find one way to cheat: Once I VPN into the network, I can access the router configuration page. I can then remove the internet block from the "Device I don't trust". But. . .this sounds kinda like something I don't want to do
Thanks for any advice!
I have a device that can't be trusted to have internet access. I want to block all internet access to this thing from the router.
BUT. . . I want to access the unit via a VPN connection (from the other side of the planet).
I have set up OpenVPN, and I can successfully dial into my network. Without restrictions in place, I can access the "Device that I don't trust".
However, if I use Network Services Filter to block this device (using it's IP address) OR if I do "Block Internet Access" from the "Client Status Page" (under network map); The VPN connection is also blocked.
I suspect the block is caused by the fact that the VPN'd computer has a 10.8.x.x assigned address; rather than the 192.168.x.x address assigned to "Device that I don't trust".
Any idea how to work around this?
For one device, filter ALL traffic, except from two subnets? (i.e. 192.168.x.x and 10.8.x.x)
PS: I did find one way to cheat: Once I VPN into the network, I can access the router configuration page. I can then remove the internet block from the "Device I don't trust". But. . .this sounds kinda like something I don't want to do
Thanks for any advice!
Last edited: