So i've been using Voxel's firmware on my R9000 for a while now, along with all the known mods. I am using the OpenVpn client talking to one of my servers to tunnel all our devices in the house out...
I am wanting to use the SoftEther VPN client, and I have it installed via Entware out to /opt/libexec/softethervpn/. I do know that after the client has been configured, you still have to modify/add routes to redirect your gateway through the tunnel as the gateway. However, here is the problem i'm trying to address first:
First off, I know the server is ok as I have installed the SoftEther VPN client on my Windows machine, and am able to establish a connection. Seems really quick compared to IPVanish/OpenVpn.
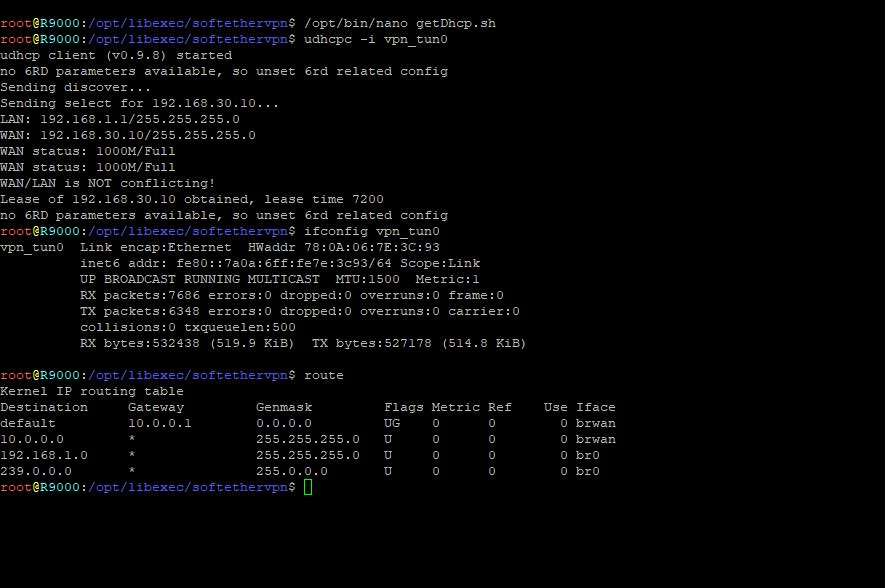
I have created the tunnel via the SoftEther client named "vpn_tun0", and you can see in the screenshot that I am using udhcpc to get a lease from the remote VPN server. Done, it gets a lease.
I then run an ifconfig on the interface, and i'm not see that it has an ip address assigned to it (not gonna blur anything else, it'll all change):
So at this point, we know the client is talking to the remote VPN server, as that is where its getting its ip. Again, if i do an ifconfig on that adapter, it still doesn't show an IP, yet its communicating.
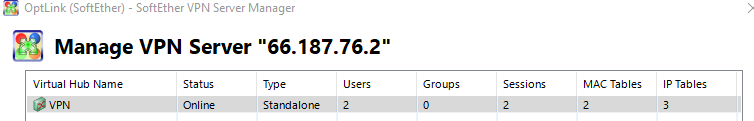
The server manager does show it has a new session:
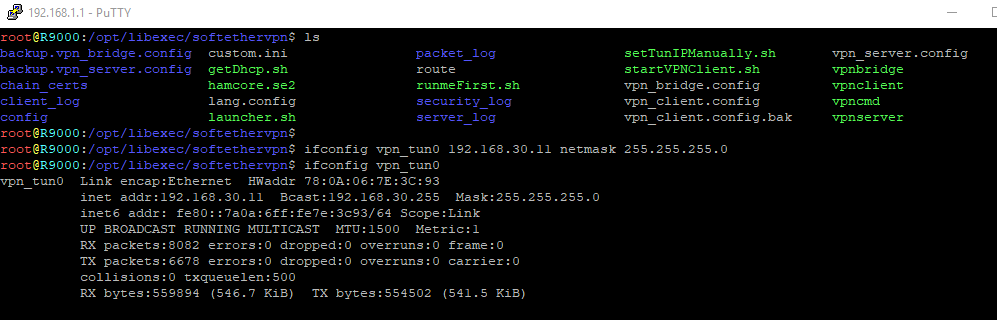
If I assign the IP manually, it sticks, but I dont want to do that. I would like DHCP to function properly:
(yeah, I need to clean it up)
So I guess my questions are, what is the proper way to assign a dhcp ip? Is udhcpc the proper way to do it? is there another method?
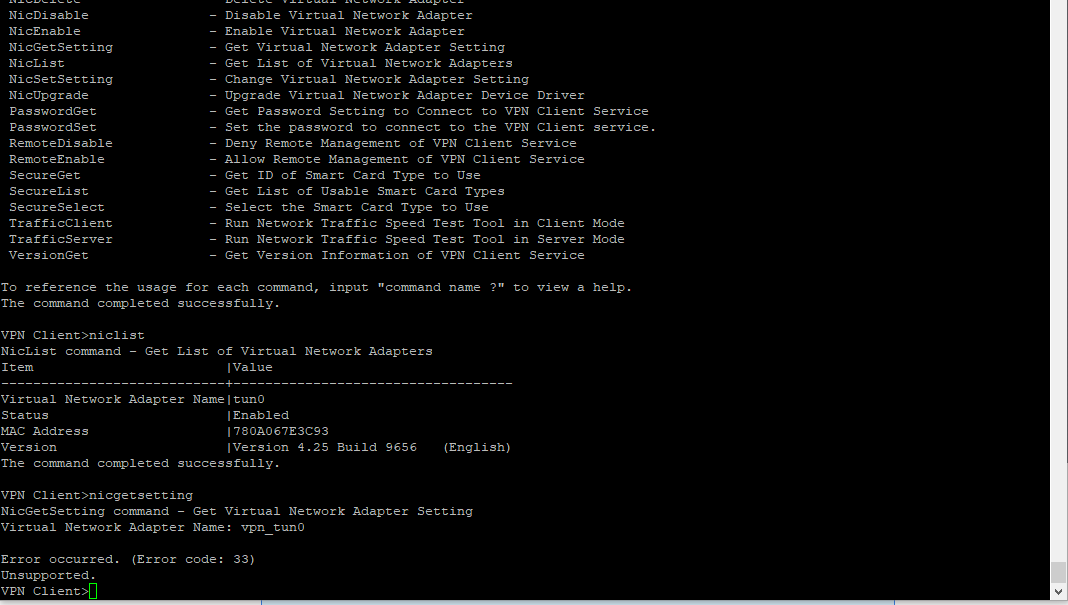
My other question is related to the way my "vpn_tun0" interface was created. I created it via "Entware/SoftEther --> ./vpncmd". ./vpncmd --> menu --> "niccreate", and it creates the virtual adapter. However, when I look at the nic properties within ./vpncmd, it errors out with an error;33. When researched, they are saying that I have to modprobe tun in order to enable Tunneling. However, modprobe has been removed and cant use it. Is this even needed at all? OpenVpn worked fine without modprobe'ing anything:
I don't suppose there many who use this, but do appreciate any feedback. (I'm thinking it may have something to do with my new routes not set up yet)
Going to bed now...