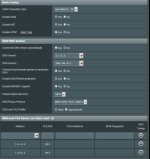
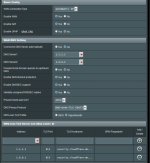
Just updated to 386.3_2 on a AC-88U from an 384 build - router was reset and memory cleared after (was not stable after update until I did this).
I have tried to enable DNS over TLS using CloudFair 1.1.1.1 on port 853.
The addresses are 1.1.1.1 and 1.0.0.1. TLS Host Name and SPKI Fingerprint are blank (Is this correct?).
Everything works fine to for the computers connected to the router via Ethernet. However my cell phone reports "connected without internet". When I disable this feature then the cell phone connects properly.
What am I doing wrong or is there a bug in this feature?
Is this any help?
I would also like to use Level 3 as the 2ndary DNS 209.244.0.3 but unsure if it supports this.
Thanx Hawker
I have tried to enable DNS over TLS using CloudFair 1.1.1.1 on port 853.
The addresses are 1.1.1.1 and 1.0.0.1. TLS Host Name and SPKI Fingerprint are blank (Is this correct?).
Everything works fine to for the computers connected to the router via Ethernet. However my cell phone reports "connected without internet". When I disable this feature then the cell phone connects properly.
What am I doing wrong or is there a bug in this feature?
Is this any help?
I would also like to use Level 3 as the 2ndary DNS 209.244.0.3 but unsure if it supports this.
Thanx Hawker