You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
“GreyNoise Discovers Stealthy Backdoor Campaign Affecting Thousands of ASUS Routers”
- Thread starter XIII
- Start date
I'm taking your answer as a Yes.That CVE is from September 2023. 386.14_2 was released over a year later, in November 2024.
Thanks for your reply.
randomName
Very Senior Member
So having the latest firmware installed and performing a factory reset is all that is needed to avoid this issue?
That's my understanding.
joegreat
Very Senior Member
AND: Disable the WAN-Acces to router - why the hell you have it turned on?So having the latest firmware installed and performing a factory reset is all that is needed to avoid this issue?
I would never turn that on, I keep most settings at default. Good to know my router is safe.AND: Disable the WAN-Acces to router - why the hell you have it turned on?
dave14305
Part of the Furniture
Seems the last persistent vulnerability is in the human owning the router and setting the password to something strong enough to resist brute force login attempts.
- Attackers gain access using brute-force login attempts and authentication bypasses, including techniques not assigned CVEs.
randomName
Very Senior Member
So passwords like 'sm3llmyf4rt5" are no good?
Damn, foiled again!
Damn, foiled again!
ibex
Occasional Visitor
Same article from LifeHacker which gives more technical explanation If You Have an Asus Router, You Need to Check If It's Been Hacked
I think I am not affected b/c the "hacker SSH key" is not in my system. However I am a bit confused. Can you please guide me through a proper fix. Here is my current config:
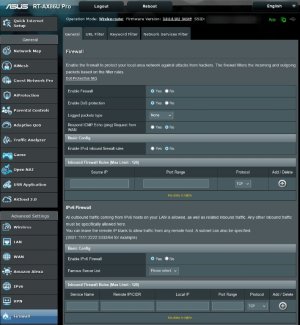
Q2. The author recommends blocking incoming requests from 4 IP addresses: 101.99.91.151, 101.99.94.173, 79.141.163.179, 111.90.146.237. Can I go a bit more strict? Block ALL unsolicited incoming requests. The way I use my router, the only legitimate incoming traffic is a response to an outgoing request originated from the home network. If "blocking all unsolicited incoming requests" is a valid security setting, can you please show me how to do that? Attached is a screenshot showing the Firewall settings. All default, excepted "Enable DoS protection" has been enabled.
I think I am not affected b/c the "hacker SSH key" is not in my system. However I am a bit confused. Can you please guide me through a proper fix. Here is my current config:
- Asus RT-AZ86U Pro, stock firmware 3.0.0.6.102_34349
- Router Login Password = 28 chars, totally random lower, upper, digits, symbols
- System settings: Telnet = No, SSH = LAN Only, Pwd Login = no
- Authorized Keys = only mine (ssh-ed25519)
- Enable Web Access from WAN = no
- Enable Access Restrictions = no
Q2. The author recommends blocking incoming requests from 4 IP addresses: 101.99.91.151, 101.99.94.173, 79.141.163.179, 111.90.146.237. Can I go a bit more strict? Block ALL unsolicited incoming requests. The way I use my router, the only legitimate incoming traffic is a response to an outgoing request originated from the home network. If "blocking all unsolicited incoming requests" is a valid security setting, can you please show me how to do that? Attached is a screenshot showing the Firewall settings. All default, excepted "Enable DoS protection" has been enabled.
Attachments
Last edited:
dave14305
Part of the Furniture
This is the default behavior of the firewall. But when the exploit enables SSH on WAN, it opens the firewall for the SSH port.If "blocking all unsolicited incoming requests" is a valid security setting, can you please show me how to do that?
ibex
Occasional Visitor
As unsollicited incoming requests are dropped by default, I assume Asus routers are immune to the attack described by GreyNoise. So the 9000+ routers which are reported as "infected" are those where the user had explicitly changed the config to allow SSH from WAN, right?This is the default behavior of the firewall. But when the exploit enables SSH on WAN, it opens the firewall for the SSH port.
Unless there is another exploit? Which can bypass Asus default settings in maybe old Asus firmware? If so since when (or which stock firmware version) that exploit has been fixed?
Last edited:
dave14305
Part of the Furniture
Based on the write up, the bad guys used another exploit to enable SSH over the WAN using the normal firmware setting. This firmware setting for SSH over the WAN informs the firewall to accept incoming WAN connections on the SSH port. That is normal firmware functionality. Gaining access to the router in the first place is the scary exploit; the persistent SSH access is just the evidence of the exploit.As unsollicited incoming requests are dropped. If the exploit could do anything to configure the router, does that mean there was/is a security defect somewhere that allow to bypass the firewall?
Judging from your question you should in the following order immediately discard all saved router configs, check the latest firmware is installed, factory reset your router, then manually configure any changes. Enjoy life
ASUS router backdoors affect 9K devices, persist after firmware updates
Authentication bypass and command injection flaws facilitate the malicious activity.www.scworld.com
Can anyone shed light on what this really means? It's all gobbledygook to me, but sounds serious!
Is there anything we can do to reduce the problem?
Even GamersNexus reported on it... now people are going to parrot "AsUs RoUtErS nOt SaFe"
Even low level just reported on it. Comments are like ASUS is so slow to fix bugs, not indicating this was fixed awhile back.
Unfortunately it’s true people don’t often update their routers and yes ASUS needs a smack for allowing remote management and even encouraging it’s use with how the mobile ASUS router app promotes it.
Similar threads
- Replies
- 4
- Views
- 2K
- Locked
- Replies
- 24
- Views
- 2K
- Replies
- 3
- Views
- 548
- Replies
- 12
- Views
- 2K
Latest threads
-
-
Release ASUS ZenWiFi BT8 Firmware version 3.0.0.6.102_58394 (2026/02/04)
- Started by fruitcornbread
- Replies: 0
-
Does Unifi ever update their OpenVPN server software?
- Started by HarryH3
- Replies: 11
-
-
Kamoj Kamoj Addon 5.5 b47 for Netgear R7800/R8900/R9000 with Voxel FW
- Started by kamoj
- Replies: 2
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!