FernandoF
Regular Contributor
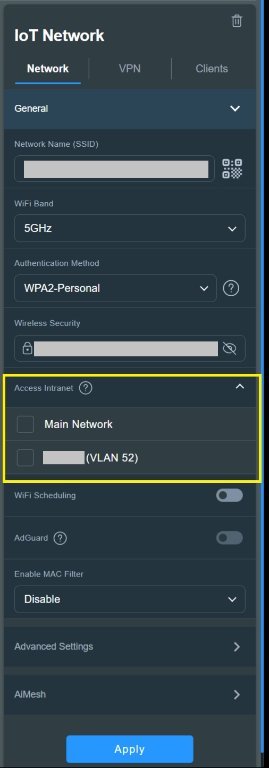
With the introduction of firmware 3006.102.x, many of us have been trying to understand what Guest Network Pro can and cannot do. In my particular case, the requirements for visitors using the guest network are the following:
Despite my inexperience, after lots of reading and experimentation, I believe I’ve finally succeeded to replicate that behavior with 3006.102.4, which I’d like to share in case anybody has a similar use case. The starting point is a Customized Guest Network Pro with
I hope this may help others (please adjust the subnet and guest network ID, if needed). I realize this approach may not be as tight as fully segregating the guest network with a different VLAN, but I still feel it's probably good enough.
Any comments or results will be greatly appreciated. Thanks in advance!
(EDIT #1: Small adjustment to ensure the rules are inserted at the very top of the chains)
(EDIT #2: Added a rule to also allow tcp protocol for DNS queries via port 53 from the guest network to the router, which may be required under certain circumstances)
- Devices must use the same subnet as the main network
- Devices must be able to access the internet
- Devices must not be able to access the intranet
Access Intranet disabled. With 3006.102.x, however, that doesn’t seem to be possible.Despite my inexperience, after lots of reading and experimentation, I believe I’ve finally succeeded to replicate that behavior with 3006.102.4, which I’d like to share in case anybody has a similar use case. The starting point is a Customized Guest Network Pro with
Use same subnet as main network enabled. I also have Set AP Isolated enabled, although I suspect that setting is not doing anything. Then I had to, either manually or via scripts, set 5 "ebtables" firewall rules:
Code:
ebtables -t broute -I BROUTING 1 -p IPv4 -i wl0.1 --ip-dst 192.168.50.1 --ip-proto udp --ip-dport 53 -j ACCEPT # Allows connections with udp protocol via port 53 from the guest network to the router, for DNS queries
ebtables -t broute -I BROUTING 2 -p IPv4 -i wl0.1 --ip-dst 192.168.50.1 --ip-proto tcp --ip-dport 53 -j ACCEPT # Allows connections with tcp protocol via port 53 from the guest network to the router, for larger DNS queries
ebtables -t broute -I BROUTING 3 -p IPv4 -i wl0.1 --ip-dst 192.168.50.0/24 -j DROP # Blocks connections with all other protocols and ports from the guest network to the local network (intranet)
ebtables -I FORWARD 1 -i wl0.1 -j DROP # Blocks outgoing packets from the guest network
ebtables -I FORWARD 2 -o wl0.1 -j DROP # Blocks incoming packets to the guest network
service restart_firewall # Restarts the firewallI hope this may help others (please adjust the subnet and guest network ID, if needed). I realize this approach may not be as tight as fully segregating the guest network with a different VLAN, but I still feel it's probably good enough.
Any comments or results will be greatly appreciated. Thanks in advance!
(EDIT #1: Small adjustment to ensure the rules are inserted at the very top of the chains)
(EDIT #2: Added a rule to also allow tcp protocol for DNS queries via port 53 from the guest network to the router, which may be required under certain circumstances)
Last edited: