You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Installing and configuring authoritative, recursive, and DoT/DNSSEC DNS server with Unbound
- Thread starter rgnldo
- Start date
So now it doesn't do DNSSEC validation right? if so, when you enable DNSSEC in gui , it doesn't work because it needs more than 0 chache-size configured in dnsmsaq.conf which gets zeroed because of dnsmasq.postconfI changed the steps to configure the unbound. The Unbound will only cache services, and authoritative dns recursion. All services with Diversion, Stubby and Skynet will continue with dnsmasq.
rgnldo
Very Senior Member
Review the steps in the post. Works, Yes.So now it doesn't do DNSSEC validation right?
rgnldo
Very Senior Member
Tested on FW Merlin 384.12. In FW 384.13-Alpha will not be possible.DNSSEC


Swistheater
Very Senior Member
i see you borrowed a page from my book. it should be noted that those modifications do not work well for the new 384.13 alpha as the style of DNSSEC has changed within dnsmasq, and the combination can be quite unstable.How to start unbound from Entware (I assume default prefix /opt is used). I still forward queries from dnsmasq (well it is a query forwarder) to unbound, listening to port 5453. The Unbound will cache services, and authoritative dns recursion. All services with Diversion, Stubby and Skynet will continue with dnsmasq.
Credits contributions [B][COLOR=#b30000]@SomeWhereOverTheRainBow[/COLOR][/B] @Swistheater (for Stubby.yml)
Contributions to this post are well received
Install unbound
Run unbound-control-setup for Unbound monitoring
Create /opt/var/lib/unbound directory
Change directory ownership to nobody, in case you want to drop daemon privileges from root to nobody
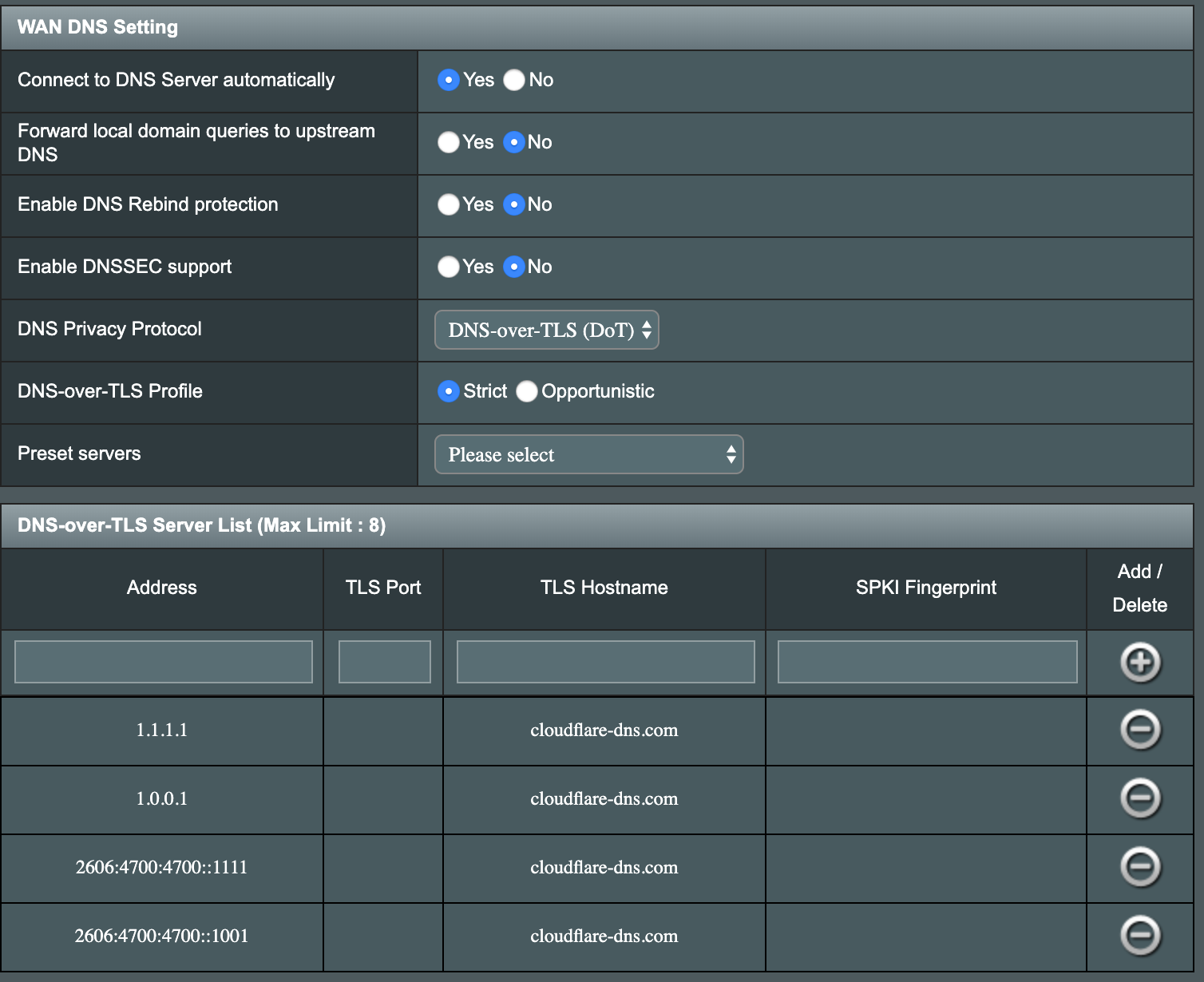
Edit /opt/etc/unbound/unbound.conf
Get root DNS server:
Code:curl -o /opt/var/lib/unbound/root.hints https://www.internic.net/domain/named.cache
Edit and start unbound daemon
Code:#!/bin/sh export PATH=/sbin:/bin:/usr/sbin:/usr/bin:$PATH export TZ=$(cat /etc/TZ) ENABLED=yes PROCS=unbound ARGS="-c /opt/var/lib/unbound/unbound.conf" PREARGS="nohup" DESC=$PROCS PATH=/opt/sbin:/opt/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin . /opt/etc/init.d/rc.func
Create dnsmasq custom configuration in /jffs/scripts/dnsmasq.postconf:
Code:CONFIG=$1 source /usr/sbin/helper.sh pc_delete "no-negcache" /etc/dnsmasq.conf pc_delete "bogus-priv" /etc/dnsmasq.conf pc_delete "domain-needed" /etc/dnsmasq.conf pc_append "server=127.0.1.1#5453" /etc/dnsmasq.conf pc_replace "cache-size=1500" "cache-size=0" /etc/dnsmasq.conf
Configure Stubby for DNSSEC validation:
nano /jffs/configs/stubby.yml.add
chmod +x /jffs/configs/stubby.yml.addCode:tls_min_version: GETDNS_TLS1_2 tls_cipher_list: "EECDH+AESGCM:EECDH+CHACHA20" tls_max_version: GETDNS_TLS1_3 tls_ciphersuites: "TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256"
nano /jffs/scripts/stubby.postconf
chmod +x /jffs/scripts/stubby.postconfCode:#!/bin/sh CONFIG=$1 source /usr/sbin/helper.sh pc_insert " - GETDNS_TRANSPORT_TLS" "dnssec_return_status: GETDNS_EXTENSION_TRUE" $CONFIG pc_replace "idle_timeout: 9000" "idle_timeout: 2000" $CONFIG pc_replace "tls_connection_retries: 2" "tls_connection_retries: 5" $CONFIG pc_replace "timeout: 3000" "timeout: 2000" $CONFIG pc_insert "dnssec_return_status: GETDNS_EXTENSION_TRUE" "return_both_v4_and_v6: GETDNS_EXTENSION_TRUE" $CONFIG
run service restart_stubby
this sets the TZ for accurate sysloging, and nohup allows for commands to be used to verify active listening addresses these different commands can be runned via command line
ps | grep unbound | grep -v grep
netstat -lnptu | grep unbound
netstat -lnpt | grep -E '^Active|^Proto|/unbound'
last thing, I treated this like a headless server situation
i opted to install haveged with
opkg install haveged
then I modified /opt/etc/init.d/S02haveged
nano /opt/etc/init.d/S02haveged
NOTE: It is advisable to configure swap memory.Code:#!/bin/sh if [ "$1" = "start" ] || [ "$1" = "restart" ]; then # Wait for NTP before starting logger -st "S02haveged" "Waiting for NTP to sync before starting..." ntptimer=0 while [ "$(nvram get ntp_ready)" = "0" ] && [ "$ntptimer" -lt "300" ]; do ntptimer=$((ntptimer+1)) sleep 1 done if [ "$ntptimer" -ge "300" ]; then logger -st "S02haveged" "NTP failed to sync after 5 minutes - please check immediately!" echo "" exit 1 fi fi export TZ=$(cat /etc/TZ) ENABLED=yes PROCS=haveged ARGS="-w 1024 -d 32 -i 32 -v 1" PREARGS="" DESC=$PROCS PATH=/opt/sbin:/opt/bin:/opt/usr/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin . /opt/etc/init.d/rc.func
rgnldo
Very Senior Member
Yes, it had noticed. Not even the Unbound works in the FW 384.13. I will stay a good time in the FW 384.12, if the incompatibility remains.those modifications do not work well for the new 384.13 alpha
Thanks, So for those with 384.13 beta, we don't need to edit Stubby ? we skip the steps below the green headline? With 384.13 beta we need to enable DNSSEC in gui ?Update tips for FW 384.13_beta1
rgnldo
Very Senior Member
Yeswe skip the steps below the green headline?
NoWith 384.13 beta we need to enable DNSSEC in gui ?
Should only mark Wan local DNS so query lookups are on 127.0.0.1

rgnldo
Very Senior Member
Don't forget to report your experience here.So for those with 384.13 beta
Mutzli
Very Senior Member
With 384.13 beta-1 the 1.1.1.1 help page reports that I'm not on 1.1.1.1 and I'm not using DoT? Is that a false negative, I'm sure the router config was not changed from 384.12

Attachments
I get the same regardless of Unbound with 1.1.1.1 test page, if you look down, it does say you are using 1.1.1.1 server and also cloudflare's ipv6 serverWith 384.13 beta-1 the 1.1.1.1 help page reports that I'm not on 1.1.1.1 and I'm not using DoT? Is that a false negative, I'm sure the router config was not changed from 384.12
View attachment 18746
rgnldo
Very Senior Member
Don't trust Cloudflaire to verify DoT, it's pure marketing. Use these options:With 384.13 beta-1 the 1.1.1.1 help page reports that I'm not on 1.1.1.1 and I'm not using DoT? Is that a false negative
dig pir.org +dnssec +multi
-> result NOERROR
dig www.dnssec-failed.org
-> result SERVFAIL
https://rootcanary.org/test.html
-> result level security
DoT verify:
https://www.dnsleaktest.com/results.html
-> result only ISP server DoT
Last edited:
Seems to work fine . DNSSEC and DoT working. But which one does the DNSSEC velidation? Unbound or Merlin's firmware?Don't forget to report your experience here.
rgnldo
Very Senior Member
Unbound+StubbyBut which one does the DNSSEC velidation? Unbound or Merlin's firmware?
dig pir.org +dnssec +multi
-> result NOERROR
dig www.dnssec-failed.org
-> result SERVFAIL
https://rootcanary.org/test.html
-> result level security
Mutzli
Very Senior Member
Don't trust Cloudflaire to verify DoT, it's pure marketing. Use these options:
dig pir.org +dnssec +multi
-> result NOERROR
dig www.dnssec-failed.org
-> result SERVFAIL
https://rootcanary.org/test.html
-> result level security
DoT verify:
https://www.dnsleaktest.com/results.html
-> result only ISP server DoT
Excellent, no leaks reported:
rgnldo
Very Senior Member
Note, if you have done this test in the same browser, you should clear the cache.https://rootcanary.org/test.html
-> result level security
Similar threads
- Replies
- 16
- Views
- 1K
- Replies
- 6
- Views
- 6K
- Replies
- 1
- Views
- 3K
Similar threads
Similar threads
-
-
Looking for advice: Would I benefit from installing Asuswrt-Merlin on my setup?
- Started by Jarenback
- Replies: 4
-
Two DNS requests to amazonaws every 30 seconds since installing AIMesh
- Started by Qwinn
- Replies: 61
Latest threads
-
-
Looking for Feedback: RT-BE92U stability issues
- Started by RMerlin
- Replies: 8
-
Entware Unsuccessful Entware installation on Asus RX-AX68U with Asuswrt-Merlin 3004.388.11
- Started by jt99999
- Replies: 7
-
-
Upgrade from Asus RT-AX88U (RT-BE88U / ROG Strix GS-BE18000 / ROG Rapture GT-BE19000AI)?..
- Started by JarleH
- Replies: 8
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 4,664 (members: 20, guests: 4,644)