InductionForced
New Around Here
Hi folks,
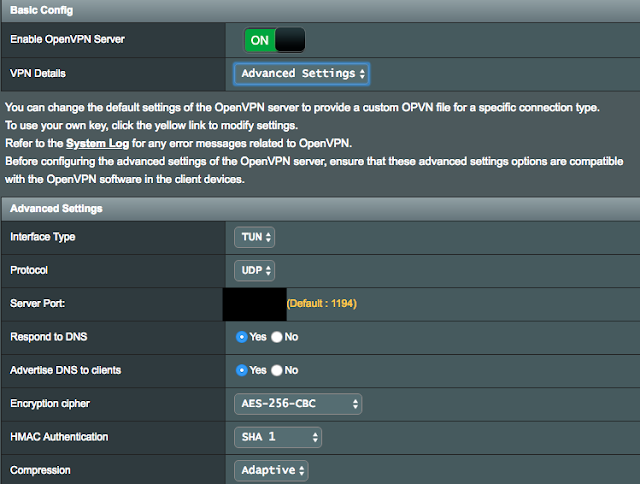
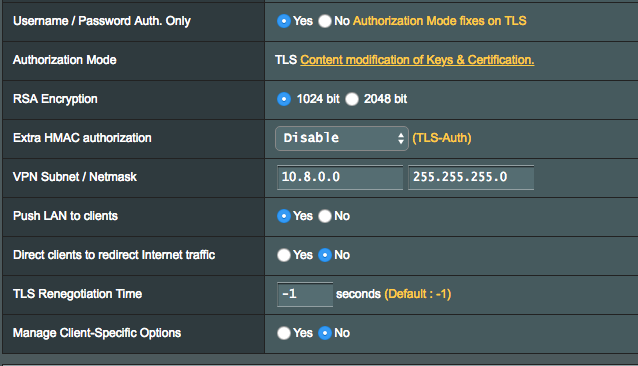
I setup the server and export the config file to my Android. I press the toggle button to connect and then I am prompted with
To see if it isn't just an Android issue I try to connect to the server on a laptop and then get a similar error
Here is the ASUS log file too when connecting to Android. Apologies for all the 'redacted' lines, not sure what I was meant to exclude so I excluded everything (IP Addresses)
Thanks in advance!
I'm very new to OpenVPN and am looking to get it a private VPN server setup on my ASUS DSL-AC68R router. I am strictly following this guide so the settings in the ASUS router are exactly the same as shown below: https://randyshomeprojects.blogspot.com/2016/11/openvpn-on-asus-router.html


I setup the server and export the config file to my Android. I press the toggle button to connect and then I am prompted with
I press continue and bypass the 'no certificate' prompt and it connects with no problems. The VPN connection is successful and all is running fine.Select Certificate. This profile doesn't include a client certificate. Continue connecting without a certificate or select one from the Android keychain?
To see if it isn't just an Android issue I try to connect to the server on a laptop and then get a similar error
My config file looks like this:Connection Error. Missing external certificate
Code:
redacted
float
nobind
proto udp
dev tun
sndbuf 0
rcvbuf 0
keepalive 10 30
comp-lzo adaptive
auth-user-pass
client
auth SHA1
cipher AES-256-CBC
remote-cert-tls server
<ca>
-----BEGIN CERTIFICATE-----
redacted
-----END CERTIFICATE-----
</ca>Here is the ASUS log file too when connecting to Android. Apologies for all the 'redacted' lines, not sure what I was meant to exclude so I excluded everything (IP Addresses)
Code:
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_VER=3.git:released:662eae9a:Release
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_PLAT=android
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_NCP=2
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_TCPNL=1
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_PROTO=2
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_LZO_STUB=1
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_COMP_STUB=1
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_COMP_STUBv2=1
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.4-5891
Feb 17 23:17:53 vpnserver1[--]: ----- peer info: IV_SSO=openurl
Feb 17 23:17:53 vpnserver1[--]: ----- PLUGIN_CALL: POST /usr/lib/openvpn-plugin-auth-pam.so/PLUGIN_AUTH_USER_PASS_VERIFY status=0
Feb 17 23:17:53 vpnserver1[--]: ----- TLS: Username/Password authentication succeeded for username 'asus' [CN SET]
Feb 17 23:17:54 vpnserver1[--]: ----- Control Channel: TLSv1.3, cipher TLSv1.3 TLS_CHACHA20_POLY1305_SHA256
Feb 17 23:17:54 vpnserver1[--]: ----- [asus] Peer Connection Initiated with [AF_INET]redacted (via [AF_INET]redacted%ppp0)
Feb 17 23:17:54 vpnserver1[--]: asus/----- MULTI_sva: pool returned IPv4=redacted, IPv6=(Not enabled)
Feb 17 23:17:54 vpnserver1[--]: asus/----- MULTI: Learn: redacted -> redacted
Feb 17 23:17:54 vpnserver1[--]: asus/----- MULTI: primary virtual IP for redacted
Feb 17 23:17:54 vpnserver1[--]: asus/----- PUSH: Received control message: 'PUSH_REQUEST'
Feb 17 23:17:54 vpnserver1[--]: asus/----- SENT CONTROL [asus]: 'PUSH_REPLY,route redacted redacted vpn_gateway 500,redirect-gateway def1,dhcp-option DNS redacted,route redacted,topology net30,ping 10,ping-restart 30,ifconfig redacted redacted,peer-id 0,cipher AES-256-GCM' (status=1)
Feb 17 23:17:54 vpnserver1[--]: asus/----- Data Channel: using negotiated cipher 'AES-256-GCM'
Feb 17 23:17:54 vpnserver1[--]: asus/----- Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Feb 17 23:17:54 vpnserver1[--]: asus/----- Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit keyThere is a certificate section in the config file as shown above so I am bit confused as to why it is saying there is no certificate as I thought when exporting that client.opvn file, everything should all be in there including the certificates to make a secure connection. I thought it was as simple as exporting the client.opvn file from the ASUS server to the client device and connecting. Although I can get away without using a certificate and successfully making a VPN connection with the server, ideally I want my VPN connection to be as secure as possible so I was wondering how I can go about implementing this certificate properly? I understand from research that one can simply add the line "--verify-client-cert none" to the server config file but that completely avoids the issue and compromises the security of the connection? I have also performed a factory hard reset to no avail.
Thanks in advance!
Last edited:




