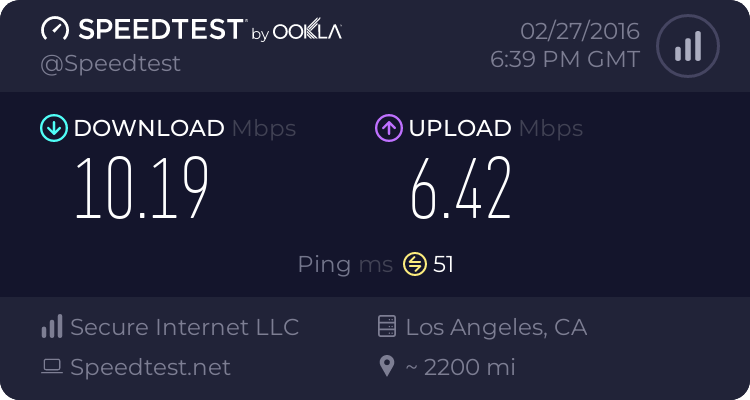
Not for everybody. With or without markings doesn't make a difference here, CTF enabled. 24mbps connection, server 3500 miles away (to avoid censorship), I get steady 20/21mbps.
P.S.: forgot to mention the AC56U is overclocked: 1000,800.
I believe you're testing OpenVPN client. Joegreat above also didn't see any improvement. The packet marking thing seems killing some brain cells from a few folks. What if it turns out a red herring..
I'm going to give another try with the latest alpha 3 later tonight. Will report back..
EDIT:
TL;DR I cannot reproduce the same tremendous effect in the latest Alpha 3..
Previous Alpha 3 I built with the stock Buildroot toolchains. The latest Alpha 3 I built with NPTL (
http://www.snbforums.com/threads/arm-toolchains-with-nptl-for-asuswrt-merlin.27938/). Other than that no major difference. I know latest Alpha 3 has marking rules added. So flush everything in iptables before my quick tests.
Test scenario
A kind of road warrior. That is the router acting as VPN server and the road warrior connects from Internet to the VPN server and access the Internet through the VPN server. Data access uses speedtest dot net. CTF on. RT-AC56U.
It's the same test scenario before and now. With marking or not, ultimately no difference in the maximum throughput in tonight's tests.
One caveat that I observed tonight is that without marking the first run usually shows bumpy speed and less than half of max achievable.
But the second and sequent runs of the same speedtest server will bring back the speed.
With marking, the first run almost near maximum achievable throughput. Perhaps coincidence.. I'm not sure. I didn't do repeat enough number of times to statistically prove a thing.