callefreddan
New Around Here
Version: 386.7_2
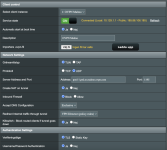
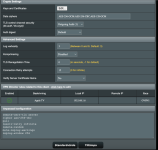
My VPN randomly disconnects for a short period of time. And then i found "ovpn-client1[4000]: SIGUSR1[soft,ping-restart] received, process restarting" in the systemlog.
remote-cert-tls server
cipher aes-256-cbc
pull
resolv-retry infinite
remote-random
mute-replay-warnings
replay-window 256
31 19:31:48 ovpn-client1[4000]: VERIFY OK: depth=1, C=SE, ST=Stockholm, L=Stockholm, OU=Firma David Wibergh, CN=ovpn.se ca, emailAddress=[email protected]
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY KU OK
Oct 31 19:31:48 ovpn-client1[4000]: Validating certificate extended key usage
Oct 31 19:31:48 ovpn-client1[4000]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY EKU OK
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY OK: depth=0, CN=vpn55.prd.malmo.ovpn.com
Oct 31 19:31:48 ovpn-client1[4000]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:31:48 ovpn-client1[4000]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:31:48 ovpn-client1[4000]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Oct 31 19:35:45 ovpn-client1[4000]: [vpn55.prd.malmo.ovpn.com] Inactivity timeout (--ping-restart), restarting
Oct 31 19:35:45 ovpn-client1[4000]: SIGUSR1[soft,ping-restart] received, process restarting
Oct 31 19:35:45 ovpn-client1[4000]: Restart pause, 5 second(s)
Oct 31 19:35:50 ovpn-client1[4000]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 31 19:35:50 ovpn-client1[4000]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Oct 31 19:35:50 ovpn-client1[4000]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Oct 31 19:35:50 ovpn-client1[4000]: TCP/UDP: Preserving recently used remote address: [AF_INET]185.86.106.145:1195
Oct 31 19:35:50 ovpn-client1[4000]: Socket Buffers: R=[524288->524288] S=[524288->524288]
Oct 31 19:35:50 ovpn-client1[4000]: UDP link local: (not bound)
Oct 31 19:35:50 ovpn-client1[4000]: UDP link remote: [AF_INET]185.86.106.145:1195
Oct 31 19:35:50 ovpn-client1[4000]: TLS: Initial packet from [AF_INET]185.86.106.145:1195, sid=764580ce 92ee1ff0
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY OK: depth=1, C=SE, ST=Stockholm, L=Stockholm, OU=Firma David Wibergh, CN=ovpn.se ca, emailAddress=[email protected]
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY KU OK
Oct 31 19:35:50 ovpn-client1[4000]: Validating certificate extended key usage
Oct 31 19:35:50 ovpn-client1[4000]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY EKU OK
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY OK: depth=0, CN=vpn55.prd.malmo.ovpn.com
Oct 31 19:35:50 ovpn-client1[4000]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Oct 31 19:35:50 ovpn-client1[4000]: [vpn55.prd.malmo.ovpn.com] Peer Connection Initiated with [AF_INET]185.86.106.145:1195
Oct 31 19:35:51 ovpn-client1[4000]: SENT CONTROL [vpn55.prd.malmo.ovpn.com]: 'PUSH_REQUEST' (status=1)
Oct 31 19:35:51 ovpn-client1[4000]: PUSH: Received control message: 'PUSH_REPLY,ping 10,ping-restart 60,persist-key,redirect-gateway def1,explicit-exit-notify 2,route-gateway 10.129.0.1,topology subnet,compress lz4-v2,dhcp-option DNS 192.165.9.158,dhcp-option DNS 46.227.67.134,ifconfig 10.129.1.1 255.255.252.0,peer-id 2,cipher AES-256-GCM'
Oct 31 19:35:51 ovpn-client1[4000]: WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: timers and/or timeouts modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: explicit notify parm(s) modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: compression parms modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --persist options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --ifconfig/up options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: route options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: route-related options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: peer-id set
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: adjusting link_mtu to 1625
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: data channel crypto options modified
Oct 31 19:35:51 ovpn-client1[4000]: Data Channel: using negotiated cipher 'AES-256-GCM'
Oct 31 19:35:51 ovpn-client1[4000]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:35:51 ovpn-client1[4000]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:35:51 ovpn-client1[4000]: Preserving previous TUN/TAP instance: tun11
Oct 31 19:35:51 ovpn-client1[4000]: NOTE: Pulled options changed on restart, will need to close and reopen TUN/TAP device.
Oct 31 19:35:51 ovpn-client1[4000]: ovpn-route-pre-down tun11 1500 1553 10.129.0.121 255.255.252.0 init
Oct 31 19:35:51 ovpn-client1[4000]: Closing TUN/TAP interface
Oct 31 19:35:51 ovpn-client1[4000]: /usr/sbin/ip addr del dev tun11 10.129.0.121/22
Oct 31 19:35:51 ovpn-client1[4000]: ovpn-down 1 client tun11 1500 1553 10.129.0.121 255.255.252.0 init
Oct 31 19:35:51 openvpn-routing: Configured killswitch on VPN client 1
Oct 31 19:35:51 dnsmasq[3337]: read /etc/host s - 6 addresses
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.199#53 for domain bredbandsbolaget.se
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.198#53 for domain bredbandsbolaget.se
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.199#53
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.198#53
Oct 31 19:35:52 ovpn-client1[4000]: TUN/TAP device tun11 opened
Oct 31 19:35:52 ovpn-client1[4000]: TUN/TAP TX queue length set to 1000
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip link set dev tun11 up mtu 1500
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip link set dev tun11 up
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip addr add dev tun11 10.129.1.1/22
Oct 31 19:35:52 ovpn-client1[4000]: ovpn-up 1 client tun11 1500 1553 10.129.1.1 255.255.252.0 init
Oct 31 19:35:52 openvpn-routing: Setting client 1 routing table's default route through the tunnel
Oct 31 19:35:52 openvpn-routing: Routing Apple TV from 192.168.1.6 to any through ovpnc1
Oct 31 19:35:52 openvpn: Forcing 192.168.1.6 to use DNS server 192.165.9.158
Oct 31 19:35:52 dnsmasq[3337]: read /etc/host s - 6 addresses
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.199#53 for domain bredbandsbolaget.se
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.198#53 for domain bredbandsbolaget.se
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.199#53
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.198#53
Oct 31 19:35:54 ovpn-client1[4000]: Initialization Sequence Completed
My VPN randomly disconnects for a short period of time. And then i found "ovpn-client1[4000]: SIGUSR1[soft,ping-restart] received, process restarting" in the systemlog.
remote-cert-tls server
cipher aes-256-cbc
pull
resolv-retry infinite
remote-random
mute-replay-warnings
replay-window 256
31 19:31:48 ovpn-client1[4000]: VERIFY OK: depth=1, C=SE, ST=Stockholm, L=Stockholm, OU=Firma David Wibergh, CN=ovpn.se ca, emailAddress=[email protected]
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY KU OK
Oct 31 19:31:48 ovpn-client1[4000]: Validating certificate extended key usage
Oct 31 19:31:48 ovpn-client1[4000]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY EKU OK
Oct 31 19:31:48 ovpn-client1[4000]: VERIFY OK: depth=0, CN=vpn55.prd.malmo.ovpn.com
Oct 31 19:31:48 ovpn-client1[4000]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:31:48 ovpn-client1[4000]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:31:48 ovpn-client1[4000]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Oct 31 19:35:45 ovpn-client1[4000]: [vpn55.prd.malmo.ovpn.com] Inactivity timeout (--ping-restart), restarting
Oct 31 19:35:45 ovpn-client1[4000]: SIGUSR1[soft,ping-restart] received, process restarting
Oct 31 19:35:45 ovpn-client1[4000]: Restart pause, 5 second(s)
Oct 31 19:35:50 ovpn-client1[4000]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 31 19:35:50 ovpn-client1[4000]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Oct 31 19:35:50 ovpn-client1[4000]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Oct 31 19:35:50 ovpn-client1[4000]: TCP/UDP: Preserving recently used remote address: [AF_INET]185.86.106.145:1195
Oct 31 19:35:50 ovpn-client1[4000]: Socket Buffers: R=[524288->524288] S=[524288->524288]
Oct 31 19:35:50 ovpn-client1[4000]: UDP link local: (not bound)
Oct 31 19:35:50 ovpn-client1[4000]: UDP link remote: [AF_INET]185.86.106.145:1195
Oct 31 19:35:50 ovpn-client1[4000]: TLS: Initial packet from [AF_INET]185.86.106.145:1195, sid=764580ce 92ee1ff0
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY OK: depth=1, C=SE, ST=Stockholm, L=Stockholm, OU=Firma David Wibergh, CN=ovpn.se ca, emailAddress=[email protected]
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY KU OK
Oct 31 19:35:50 ovpn-client1[4000]: Validating certificate extended key usage
Oct 31 19:35:50 ovpn-client1[4000]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY EKU OK
Oct 31 19:35:50 ovpn-client1[4000]: VERIFY OK: depth=0, CN=vpn55.prd.malmo.ovpn.com
Oct 31 19:35:50 ovpn-client1[4000]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Oct 31 19:35:50 ovpn-client1[4000]: [vpn55.prd.malmo.ovpn.com] Peer Connection Initiated with [AF_INET]185.86.106.145:1195
Oct 31 19:35:51 ovpn-client1[4000]: SENT CONTROL [vpn55.prd.malmo.ovpn.com]: 'PUSH_REQUEST' (status=1)
Oct 31 19:35:51 ovpn-client1[4000]: PUSH: Received control message: 'PUSH_REPLY,ping 10,ping-restart 60,persist-key,redirect-gateway def1,explicit-exit-notify 2,route-gateway 10.129.0.1,topology subnet,compress lz4-v2,dhcp-option DNS 192.165.9.158,dhcp-option DNS 46.227.67.134,ifconfig 10.129.1.1 255.255.252.0,peer-id 2,cipher AES-256-GCM'
Oct 31 19:35:51 ovpn-client1[4000]: WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: timers and/or timeouts modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: explicit notify parm(s) modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: compression parms modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --persist options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --ifconfig/up options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: route options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: route-related options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: peer-id set
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: adjusting link_mtu to 1625
Oct 31 19:35:51 ovpn-client1[4000]: OPTIONS IMPORT: data channel crypto options modified
Oct 31 19:35:51 ovpn-client1[4000]: Data Channel: using negotiated cipher 'AES-256-GCM'
Oct 31 19:35:51 ovpn-client1[4000]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:35:51 ovpn-client1[4000]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Oct 31 19:35:51 ovpn-client1[4000]: Preserving previous TUN/TAP instance: tun11
Oct 31 19:35:51 ovpn-client1[4000]: NOTE: Pulled options changed on restart, will need to close and reopen TUN/TAP device.
Oct 31 19:35:51 ovpn-client1[4000]: ovpn-route-pre-down tun11 1500 1553 10.129.0.121 255.255.252.0 init
Oct 31 19:35:51 ovpn-client1[4000]: Closing TUN/TAP interface
Oct 31 19:35:51 ovpn-client1[4000]: /usr/sbin/ip addr del dev tun11 10.129.0.121/22
Oct 31 19:35:51 ovpn-client1[4000]: ovpn-down 1 client tun11 1500 1553 10.129.0.121 255.255.252.0 init
Oct 31 19:35:51 openvpn-routing: Configured killswitch on VPN client 1
Oct 31 19:35:51 dnsmasq[3337]: read /etc/host s - 6 addresses
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.199#53 for domain bredbandsbolaget.se
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.198#53 for domain bredbandsbolaget.se
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.199#53
Oct 31 19:35:51 dnsmasq[3337]: using nameserver 195.54.122.198#53
Oct 31 19:35:52 ovpn-client1[4000]: TUN/TAP device tun11 opened
Oct 31 19:35:52 ovpn-client1[4000]: TUN/TAP TX queue length set to 1000
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip link set dev tun11 up mtu 1500
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip link set dev tun11 up
Oct 31 19:35:52 ovpn-client1[4000]: /usr/sbin/ip addr add dev tun11 10.129.1.1/22
Oct 31 19:35:52 ovpn-client1[4000]: ovpn-up 1 client tun11 1500 1553 10.129.1.1 255.255.252.0 init
Oct 31 19:35:52 openvpn-routing: Setting client 1 routing table's default route through the tunnel
Oct 31 19:35:52 openvpn-routing: Routing Apple TV from 192.168.1.6 to any through ovpnc1
Oct 31 19:35:52 openvpn: Forcing 192.168.1.6 to use DNS server 192.165.9.158
Oct 31 19:35:52 dnsmasq[3337]: read /etc/host s - 6 addresses
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.199#53 for domain bredbandsbolaget.se
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.198#53 for domain bredbandsbolaget.se
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.199#53
Oct 31 19:35:52 dnsmasq[3337]: using nameserver 195.54.122.198#53
Oct 31 19:35:54 ovpn-client1[4000]: Initialization Sequence Completed