I am using Sophos UTM since 3 years. Rock solid and easy to use. I am very satisfied with it.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
pfSense/Sophos vs ASUSWRT/RMerlin - Is there any reason to change?
arcticblue
New Around Here
I run Sophos on a http://www.ebay.com/itm/Hot-Lowest-...r-8GB-128GB-/262647921398?hash=item3d27093af6.
CPU load is low, memory consumption low as well. Sitting on a 100/100 line and everything simply works.
The only thing missing is support of OpenVPN in Sophos (it is available in Pfsense), but guess you can't get it all
CPU load is low, memory consumption low as well. Sitting on a 100/100 line and everything simply works.
The only thing missing is support of OpenVPN in Sophos (it is available in Pfsense), but guess you can't get it all
I am starting to figure out why I am looking at an alternative for ASUSWRT: What I am after, I think at least, is that when a device connects over VPN it only needs access for using adblock solution (so to speak) - no more no less. Then we have the internal system so to speak which is a homeseer home controller, my Marantz receiver, DVD/BR/TV unit (IP ocnnected) and so on. With the exception for internet audio streaming all the devices has NO access to the outside at all. Then we have the Synology NAS box which can send email (and only email). And then of course the mobile phones, tablets and PCs.
What I think I am trying to do is to "segment" my network, so that nothing has connections to outside without me so saying (and devices seems to love to connect to what-ever service all the time). And if I VPNs in, well it should have NO access to the internal boxes, and only use Adblock Solution.
Any way to do this with Asuswrt? I can only see this happening with pfsense?
What I think I am trying to do is to "segment" my network, so that nothing has connections to outside without me so saying (and devices seems to love to connect to what-ever service all the time). And if I VPNs in, well it should have NO access to the internal boxes, and only use Adblock Solution.
Any way to do this with Asuswrt? I can only see this happening with pfsense?
muffintastic
Senior Member
I've made the switch to pfSense running on a Dual-Core Optiplex 760 SFF with 4GB and 250GB HDD for £40 ($48.92 as of 22-10-2016) with a dual Intel PCi-E and on board Dell all 3 are 1GB connections, it's best thing since slice bread, pfSense has more features etc.
errrr mah gawd!!! - this is hard work lol!
So me new NUC turned up tuther day - nice bit of kit Intel N3150 1.6Ghz x 4, 4Gb DDR3, 60Gb SSD - sits at 50% RAM useage and never gets to 10% cpu load running Sophos with all stuff turned on.
Problem is I think I'm going to get stuck here and its not going to work out as planned.
Original plan was to leave the Asus Router alone and whack the Sophos NUC between it and the cable modem I have. Had to change all sorts of stuff just to get it working which I'm not that impressed by! Sophos installed on 192.168.2.100 or the same ip range as my network wouldn't allow me to get to the web gui without enabling NAT on the router.
Router is currently set to static IP and is still dishing out IP addresses (which is the way I wanted it) - but I think I'm going to lose out if I do what everyone recommends and just use the AC-88U as an AP - I need the Link aggregation function of the AC-88U - If I put the router in AP mode will Link agg still work?
Whilst I've got it all working - speedtest.net is reporting only 5Mb/s download and 12 upload. My connection is 200 down 12 up so its kinda wierd and I thought the IPS stuff might be screwing with that. Tried the xbone S and that came back with a 58MB/s successfull test (not got xbox live working yet - need to open ports etc).
Before I start opening ports and stuff can anyone make any recommendations on what I'm trying to achieve here - I've had to basically disable all firewall and Protection stuff on the Asus router (was hoping it would just be another layer of protection) and don't want to go the route of using it as just an AP - It has some really fancy features that I like (like traffic monitor from my phone etc).
This is gunna take me a while lol! - Missus and kids not impressed no internet all day lol
So me new NUC turned up tuther day - nice bit of kit Intel N3150 1.6Ghz x 4, 4Gb DDR3, 60Gb SSD - sits at 50% RAM useage and never gets to 10% cpu load running Sophos with all stuff turned on.
Problem is I think I'm going to get stuck here and its not going to work out as planned.
Original plan was to leave the Asus Router alone and whack the Sophos NUC between it and the cable modem I have. Had to change all sorts of stuff just to get it working which I'm not that impressed by! Sophos installed on 192.168.2.100 or the same ip range as my network wouldn't allow me to get to the web gui without enabling NAT on the router.
Router is currently set to static IP and is still dishing out IP addresses (which is the way I wanted it) - but I think I'm going to lose out if I do what everyone recommends and just use the AC-88U as an AP - I need the Link aggregation function of the AC-88U - If I put the router in AP mode will Link agg still work?
Whilst I've got it all working - speedtest.net is reporting only 5Mb/s download and 12 upload. My connection is 200 down 12 up so its kinda wierd and I thought the IPS stuff might be screwing with that. Tried the xbone S and that came back with a 58MB/s successfull test (not got xbox live working yet - need to open ports etc).
Before I start opening ports and stuff can anyone make any recommendations on what I'm trying to achieve here - I've had to basically disable all firewall and Protection stuff on the Asus router (was hoping it would just be another layer of protection) and don't want to go the route of using it as just an AP - It has some really fancy features that I like (like traffic monitor from my phone etc).
This is gunna take me a while lol! - Missus and kids not impressed no internet all day lol
Took a while but I got there in the end! 
Instead of trying to use the routers DHCP and additional firewalls etc - I just set it to AP mode. Having had time to familiarise with the Sophos GUI I reformatted and came up with a plan.
Reinstall Sophos but this time using it as a DHCP server.
Created network definition groups for the following:
PC's - For endpoint management (A/V etc)
Consoles, Mobile, TV's - For all the media stuff
IP Cameras
Achieved all this using MAC address based groups so don't need to worry about IP addresses changing etc.
Rule for Consoles, Mobiles, TV's group to allow full access outbound. Rest was locked down.
Questions - With the AC-88U in AP mode shouldn't it appear in the Access Points list on the UTM?
As it currently stands it works fine (allowing devices to connect and be controlled by the UTM) but it doesn't show up in the UTM as an actual AP - just a device.....
Instead of trying to use the routers DHCP and additional firewalls etc - I just set it to AP mode. Having had time to familiarise with the Sophos GUI I reformatted and came up with a plan.
Reinstall Sophos but this time using it as a DHCP server.
Created network definition groups for the following:
PC's - For endpoint management (A/V etc)
Consoles, Mobile, TV's - For all the media stuff
IP Cameras
Achieved all this using MAC address based groups so don't need to worry about IP addresses changing etc.
Rule for Consoles, Mobiles, TV's group to allow full access outbound. Rest was locked down.
Questions - With the AC-88U in AP mode shouldn't it appear in the Access Points list on the UTM?
As it currently stands it works fine (allowing devices to connect and be controlled by the UTM) but it doesn't show up in the UTM as an actual AP - just a device.....
This is my recommendation. Use OpenBSD as your firewall etc minus wireless. OpenBSD is pretty much the most secure operating system you can use at this point in time. I don't want to get into a debate over security. This is solely my option and recommendation and you should research this yourself. You can also try OPNsense or Pfsense, both based on FreeBSD, if you can't manage an operating system without a GUI. Use your wireless router as an access point only.
Working in IT I know a fair few penetration testers (aka hax0rs!)
Some of which 'claim' they can get past a pfsense firewall in 5 minutes. Sophos take them 20 minutes hence I would say Sophos is the more secure as it uses a closed platform no?
The one feature of Sophos (and the main point of changing from a consumer grade router) is the Reverse Proxy setting - easily allows me to proxy my NAS box through it - adding extra protection to the one unit I will have internet facing.
Some of which 'claim' they can get past a pfsense firewall in 5 minutes. Sophos take them 20 minutes hence I would say Sophos is the more secure as it uses a closed platform no?
The one feature of Sophos (and the main point of changing from a consumer grade router) is the Reverse Proxy setting - easily allows me to proxy my NAS box through it - adding extra protection to the one unit I will have internet facing.
sfx2000
Part of the Furniture
Working in IT I know a fair few penetration testers (aka hax0rs!)
Some of which 'claim' they can get past a pfsense firewall in 5 minutes. Sophos take them 20 minutes hence I would say Sophos is the more secure as it uses a closed platform no?
The one feature of Sophos (and the main point of changing from a consumer grade router) is the Reverse Proxy setting - easily allows me to proxy my NAS box through it - adding extra protection to the one unit I will have internet facing.
Got proof against any current build? Or is is this just locker room chat?
pfSense, like any firewall, might have vulns,... but every platform does...
Pen testers will obviously exploit vulnerabilities bud - and no I didn't get into specifics just asked which is the 'more secure' of the two. Was actually quite surprised he recommended Sophos above pfsense.
Anyways:
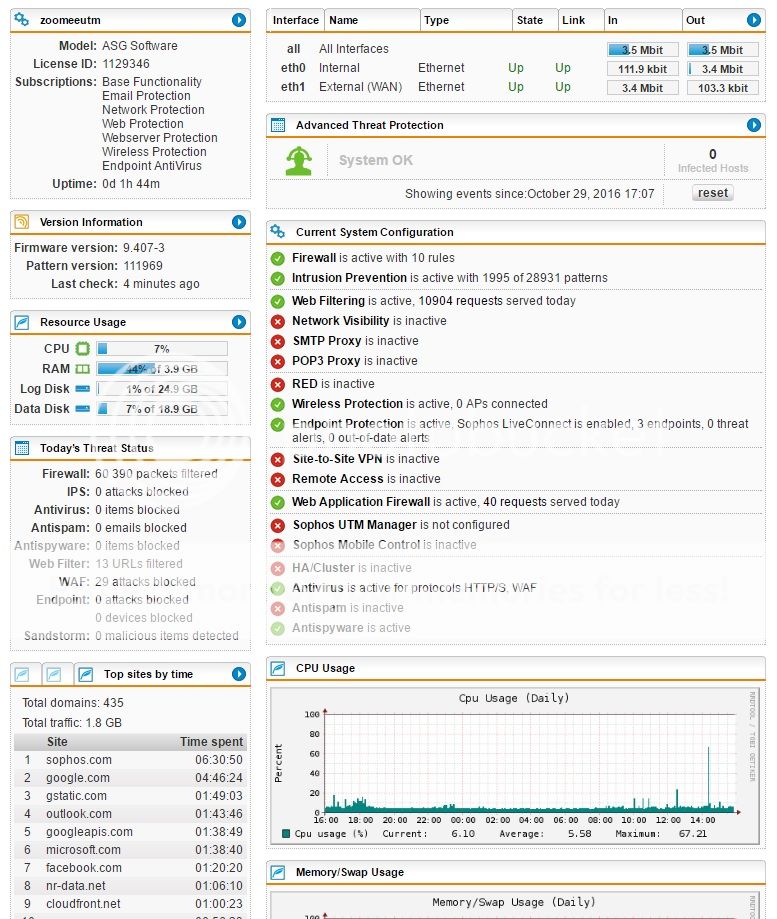
the end result!!! - Don't think I'll ever go back to consumer grade routers after this! - I'm still in awe at the feature set. My liccle imported NUC seems to be holding it down well too - averaging only 40% memory useage and 20% cpu useage (tiny spike up to 60% not sure why but I was messing with settings then).
You can see after setting up my NAS (all four ports for Web, CCTV, Note and SAB) - the system has already picked up some attacks lol! (WAF) - was worth the extra effort just for that alone. It was all pretty straight forward except for the Sabnzbd part of it - That needed some AV and security stuff disabling before it would work properly.
The web filtering is far more customisable than the likes of Asus and I've actually enabled it along with endpoint protection for the 3 PC's I have (extra protection for the kids).
Can't say I'm an expert on this stuff, but wasn't that difficult to sort in the end - Sophos have a huge knowledge base to assist - can't recommend it enough.
Thanks to everyone for the input - its been an adventure - time to sell this over-priced Access point (AC88U) and get somat cheaper whilst its still worth something lol
- time to sell this over-priced Access point (AC88U) and get somat cheaper whilst its still worth something lol
Anyways:

the end result!!! - Don't think I'll ever go back to consumer grade routers after this! - I'm still in awe at the feature set. My liccle imported NUC seems to be holding it down well too - averaging only 40% memory useage and 20% cpu useage (tiny spike up to 60% not sure why but I was messing with settings then).
You can see after setting up my NAS (all four ports for Web, CCTV, Note and SAB) - the system has already picked up some attacks lol! (WAF) - was worth the extra effort just for that alone. It was all pretty straight forward except for the Sabnzbd part of it - That needed some AV and security stuff disabling before it would work properly.
The web filtering is far more customisable than the likes of Asus and I've actually enabled it along with endpoint protection for the 3 PC's I have (extra protection for the kids).
Can't say I'm an expert on this stuff, but wasn't that difficult to sort in the end - Sophos have a huge knowledge base to assist - can't recommend it enough.
Thanks to everyone for the input - its been an adventure
Last edited:
Updated title to pfsense/Sophos....
Sorry to hijack your thread bud lol!
Just looking at your requirements that you've mentioned above I personally feel sophos will be more suited to you than Pfsense. PFsense requires additional modules to be installed for even half of what sophos is capable of and even then they can be a bit hit and miss according to the pfsense forums I've been scouring through.
Whilst the GUI for Sophos doesn't require a masters degree it can take a couple of days to figure out how it all works - basic thing to remember is EVERYTHING is blocked. Oh and a downside / upside of sophos is that there is no upnp support. PFsense has this functionality.
Sophos is a fully functional product with the only limit being 50 ip addresses - I was surprised that I only have about 15 devices yet the ip list showed about 25! lol - switches and ap's count too
btw - quick tip. If you have an AC-88U or Asus router capable of link aggregation it still works in AP mode:
http://www.snbforums.com/threads/rt-ac88u-port-aggregation-problem.30286/
My NAS is still running full pelt saturating the gb link, sitting nice and secure behind the UTM lol. There is a slight impact to end clients though - I noticed ips and av and all the other stuff limits my connection down to 130Mb/s as opposed to the full 200Mb/s. The NAS however doesn't have this stuff enabled for most of it so can easily hit 160Mb/s as it did before. Obviously a slight performance penalty for the added security. Oh and btw - you won't need adblock - once you enable the web filtering it automatically blocks all that crud out.
sfx2000
Part of the Furniture
I took a look at Sophos' UTM last week, out of curiosity. It left me far more impressed than when I tried pfsense and IPTraffic, a few months ago. It felt far more polished as a product, and more straightforward to configure/manage as well.
Sophos UTM isn't that bad - and it runs ok in virtualization as well - there's an article on the main site where someone does just that on a QNAP NAS box via their VM solution...
Once one goes over to x86, there's quite a few options - Sophos UTM is one - pfSense, RouterOS, VyOS - these are just some of the options available.
I use Sophos XG 16 on a VM. It is similar to Sophos UTM but has a more beautiful UI. I'm happy with it.
https://www.sophos.com/en-us/products/free-tools/sophos-xg-firewall-home-edition.aspx
https://www.sophos.com/en-us/products/free-tools/sophos-xg-firewall-home-edition.aspx
Last edited:
In terms of IPS Sophos UTM/XG is better.
I use Sophos XG 16 on a VM. It is similar to Sophos UTM but has a more beautiful UI. I'm happy with it.
https://www.sophos.com/en-us/products/free-tools/sophos-xg-firewall-home-edition.aspx
What or Why should one choose XG over UTM? I don't care about the GUI - I am ONLY interested in the network security part so to speak....?
Look at the sophos forums and read about all the users who have migrated from utm to XG. A lot of complaints of either missing functionality or wierd gui based issues. I'd advise to stay away from it for now tbh.In terms of IPS Sophos UTM/XG is better.
Sent from my D6603 using Tapatalk
Similar threads
- Replies
- 192
- Views
- 28K
Similar threads
Similar threads
-
-
-
-
-
Asuswrt-Merlin 3004.288.8_4 /jffs Partition Nuked on Random Reboot
- Started by garycnew
- Replies: 6
-
-
-
-
-
Latest threads
-
-
-
-
-
Solved GT-AX6000 and GT-AXE16000 Antennas: interchangeable?
- Started by ika
- Replies: 5
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
