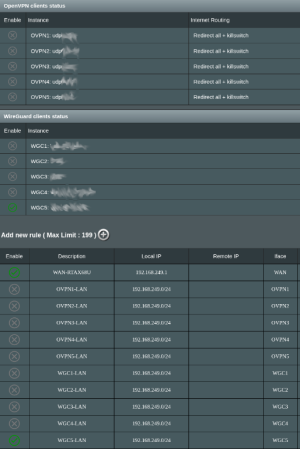
The VPN Director page's Add a Rule dialog box gives the user an example of how to route an entire network to the VPN tunnel:
* IP addresses can be entered in CIDR format (for example, 192.168.1.0/24).
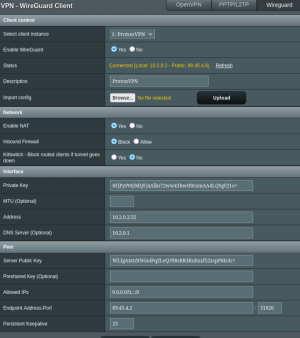
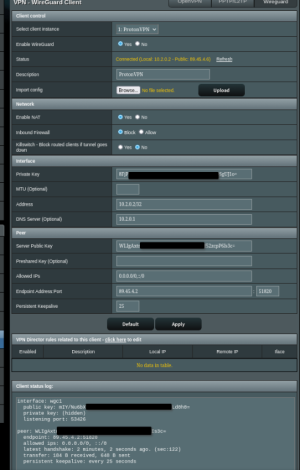
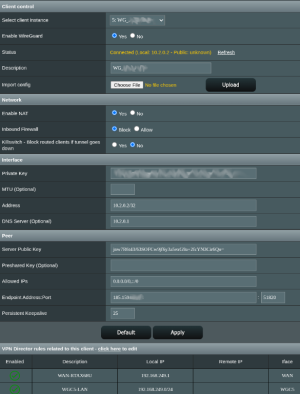
Attached are some examples of how my VPN Director is configured to use the free version of ProtonVPN WireGuard. In my examples the router is 192.168.2.1 and set to WAN, and because I'm using 2 Pi-Holes on Raspberry Pi's, I have those routed to WAN and not through the ProtonVPN tunnel. These work for my use case. One will have to configure the rules for their own individual use case.
The VPN Director settings example:
View attachment 69126
ProtonVPN WireGuard Client page showing it connected with the public IP address the tunnel is using.
View attachment 69127
Web browser showing what my IP is with the ProtonVPN WireGuard tunnel active:
View attachment 69128
This is very helpful - thanks so much! Here are my use-case questions:
- Assume:
-- Router is at 192.168.1.100
-- server is at 192.168.1.201
-- TV is at 192.168.1.202
-- PC is at 192.168.1.202
WGC1: 80.64.50.10
Ext: ISP IP: 136.26.101.45
If I want my PC alone to use the vpn tunnel - then I'd create a rule that 'assigns' 192.168.1.202/24 to WGC1 (assuming WGC1 is my VPN tunnel client)
For my Server and TV I would assign 192.168.1.202/24 and 192.168.1.201/24 to WAN
If that is my only rule then all my traffic on my PC is using - 86.64.50.10 (vpn tunnel)
My TV, Server and Router are all using: 136.26.101.45
Sound right?
Why would I need/want to have a rule for my router to use WAN? what happens if I don't...
... basically what VPN director is doing (when enabled and connected) - is I now have 2 WAN ports... where WAN is my external ISP IP and WGC1 is my VPN Tunnel... if that assumption is correct then it sounds like I have to put a rule in for ALL my clients?
Is there a way to add a single rule so ALL clients are using the VPN tunnel? If I do that is there then a hierarchy to the rules? (meaning if my first rule is ALL clients > WGC1 but I add a 2nd rule where PC > WAN... does the 2nd rule still work (is it even allowed?)