gil80
Regular Contributor
Hi all.
I'm new here.
I'm running Pi-Hole adblocker alongside my router.
The Pi-Hole IP address is 192.168.1.2.
In the Asus router under LAN DHCP settings, I set the DNS to the Pi's IP address 192.168.1.2.
Under WAN, I set the Obtain DNS automatically to NO and left it empty but also experimented with setting it manually to 192.168.1.2.
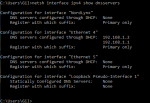
In both cases, after flushing the DNS on my PC, I ran: netsh interface ipv4 show dnsservers
And for my PC's ethernet port, it seems that the router is refusing to let 192.168.1.2 be the DNS. It distributes itself as a DNS alongside Pi-hole, despite having only defined Pi-hole as a DNS via the router's DHCP settings.
Is there a way to overcome this to make sure my clients are using 192.168.1.2 as the DNS and the router won't distribute 192.168.1.1 as the DNS?
I'm new here.
I'm running Pi-Hole adblocker alongside my router.
The Pi-Hole IP address is 192.168.1.2.
In the Asus router under LAN DHCP settings, I set the DNS to the Pi's IP address 192.168.1.2.
Under WAN, I set the Obtain DNS automatically to NO and left it empty but also experimented with setting it manually to 192.168.1.2.
In both cases, after flushing the DNS on my PC, I ran: netsh interface ipv4 show dnsservers
And for my PC's ethernet port, it seems that the router is refusing to let 192.168.1.2 be the DNS. It distributes itself as a DNS alongside Pi-hole, despite having only defined Pi-hole as a DNS via the router's DHCP settings.
Is there a way to overcome this to make sure my clients are using 192.168.1.2 as the DNS and the router won't distribute 192.168.1.1 as the DNS?