kstamand
Regular Contributor
Does Diversion work with Guest Network Pro Profiles / Vlan? If yes, is there any additional configuration outside of what the Diversion script does?
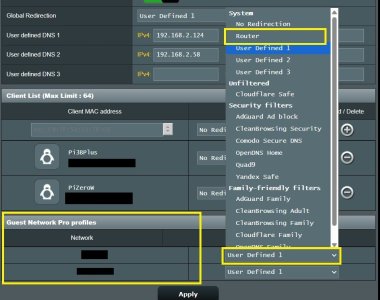
Reason I ask is, it appears Diversion works as expected for the Wireless Network SSID (Main Network), but not for the additional SSID / VLAN Profiles created under Guest Network Pro (sites that are in Diversion's blocklist work under Guest Network Pro SSID / VLAN (as in, sites in blocklist are working, whereas I expected them to be blocked), but not under the Wireless Network SSID (as in, sites in blocklist are successfully being blocked) >> I was hoping the blocks would affect each VLAN, but no).
Looking at the dnsmasq-#.conf files that are created for each Guest Network Pro SSID/VLAN, I do not see the same Diversion Directives as I do under dnsmasq.conf
Thanks in advance
Edit: looking in dnsmasq.log, I don’t see any query / responses for any of the Guest Network Pro SSID / VLAN) - if I’m not mistaken, I expected to see query records for each.
Reason I ask is, it appears Diversion works as expected for the Wireless Network SSID (Main Network), but not for the additional SSID / VLAN Profiles created under Guest Network Pro (sites that are in Diversion's blocklist work under Guest Network Pro SSID / VLAN (as in, sites in blocklist are working, whereas I expected them to be blocked), but not under the Wireless Network SSID (as in, sites in blocklist are successfully being blocked) >> I was hoping the blocks would affect each VLAN, but no).
Looking at the dnsmasq-#.conf files that are created for each Guest Network Pro SSID/VLAN, I do not see the same Diversion Directives as I do under dnsmasq.conf
# start of Diversion directives #
conf-file=/opt/share/diversion/list/allowlist.conf
conf-file=/opt/share/diversion/list/blockinglist.conf
conf-file=/opt/share/diversion/list/denylist.conf
log-async
log-queries
log-facility=/opt/var/log/dnsmasq.log
# end of Diversion directives #
Also, if it matters, under LAN Settings, DNS Director is enabled and set to Router.Thanks in advance
Edit: looking in dnsmasq.log, I don’t see any query / responses for any of the Guest Network Pro SSID / VLAN) - if I’m not mistaken, I expected to see query records for each.
Last edited: