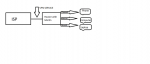
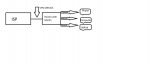
Hi! I have read up on several guides for setting up a VPN on mu ASUSMerlin router. But im still having the issue that not my whole network goes threw the vpn only my computer and not the phone and everything else connected to the network.
- Basically I want it to be setup as my superb editing skills of the photo below (pun) Could anyone guide me to the right direction.
I have the .ovpn file correctly setup via VPN Client within the router. But as I said is now encrypting every device just some.
Thanks in advance for a stupid question
- Basically I want it to be setup as my superb editing skills of the photo below (pun) Could anyone guide me to the right direction.
I have the .ovpn file correctly setup via VPN Client within the router. But as I said is now encrypting every device just some.
Thanks in advance for a stupid question