This post is just FYI.
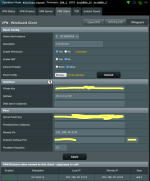
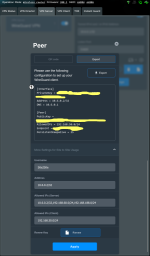
I have successfully got my two way communication between two LAN connected through Wireguard. However, the VPN Status at the server end doesn't show as connected. The VPN Status at the client end does correctly show the connection. Because everything is working well, I'm loath to mess with it and I just figure that the status of wireguard connections may not be always detected easily?
The important thing to me is it is working well, all devices in the LANs can connect to each other as if it was one big LAN with two /24 subnets.
I have successfully got my two way communication between two LAN connected through Wireguard. However, the VPN Status at the server end doesn't show as connected. The VPN Status at the client end does correctly show the connection. Because everything is working well, I'm loath to mess with it and I just figure that the status of wireguard connections may not be always detected easily?
The important thing to me is it is working well, all devices in the LANs can connect to each other as if it was one big LAN with two /24 subnets.
Attachments
-
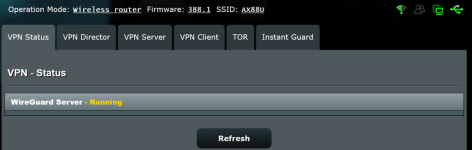 FireShot Pro Webpage Capture 003 - 'ASUS Wireless Router RT-AX88U - VPN Status' - 192.168.50.1.png58.5 KB · Views: 407
FireShot Pro Webpage Capture 003 - 'ASUS Wireless Router RT-AX88U - VPN Status' - 192.168.50.1.png58.5 KB · Views: 407 -
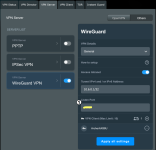 FireShot Pro Webpage Capture 002 - 'ASUS Wireless Router RT-AX88U - VPN Client' - 192.168.50.1.png80.1 KB · Views: 376
FireShot Pro Webpage Capture 002 - 'ASUS Wireless Router RT-AX88U - VPN Client' - 192.168.50.1.png80.1 KB · Views: 376 -
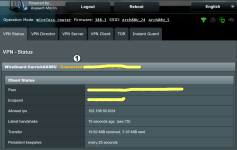 FireShot Pro Webpage Capture 001 - 'ASUS Wireless Router RT-AX88U - VPN Status' - 192.168.60.1.png142 KB · Views: 424
FireShot Pro Webpage Capture 001 - 'ASUS Wireless Router RT-AX88U - VPN Status' - 192.168.60.1.png142 KB · Views: 424