Since I consider myself a coder, I scripted these copy and paste instructions in this thread as an automated procedure.
What does
ca_cert_check.sh do
- Checks if the script needs to run on your router. Only run it on routers with outdated firmware where you get the dreaded "All download attempts failed, exiting amtm now.".
- Sets curl download to insecure mode temporarily.
- Checks for and downloads when missing /jffs/ca-bundle.crt
(downloaded from
https://raw.githubusercontent.com/R...er/release/src/router/rom/certs/ca-bundle.crt).
- Checks for /jffs/scripts/services-start and enters when missing the entry 'mount -o bind /jffs/ca-bundle.crt /etc/ssl/certs/ca-certificates.crt # Added by amtm'
- Checks if Entware is installed and if so installs package curl when missing.
- If Entware is not installed it will prompt you to open
amtm and install it with
ep.
- The full script command posted below must be run again after installing Entware to finish up the check.
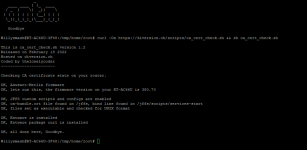
- The script does not need to be run again if at the end it says "OK, all done here, Goodbye."
- The script removes the temporary curl insecure mode.
- The script removes itself from the router after each run.
- Running this script repeatedly with the same outcome does not harm your router.
Your router should again be able to run amtm without errors, even after a reboot.
What does ca_cert_check.sh
not do
- It does not remove your hand pasted commands into files from this thread - you have to do that yourself first.
Copy and paste the full ca_cert_check.sh line into your routers SSH terminal an press Enter
Code:
curl -Os https://diversion.ch/scripts/ca_cert_check.sh && sh ca_cert_check.sh
If nothing happens after the above step, you will need to initially set your router to download in insecure mode from my website.
Paste this into the SSH terminal and press Enter
Code:
echo insecure >> $HOME/.curlrc
After this, copy and paste the ca_cert_check.sh line again. It should run now. The insecure mode will be disabled when completing the ca_cert_check.sh checks.