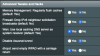
I've updated to 384.10. Done a complete clear of all data, and manually re-entered everything.
Internet still shows "Disconnected".
This is on an RT-AC86U. I also set up my older RT-AC68U, manually entered in exactly the same settings. That works fine. So it is related to the RT-AC86U.
I have a VPN connection redirecting two PC's to a VPN, so it uses policy based routing. When I turn this off, the Internet correctly shows connected. Turn it on, and goes back to disconnected (even though it remains connected).
Anybody have any idea why the VPN would affect the status?
Not that it really matters - I know it is connected so it really is just a display issue.
Internet still shows "Disconnected".
This is on an RT-AC86U. I also set up my older RT-AC68U, manually entered in exactly the same settings. That works fine. So it is related to the RT-AC86U.
I have a VPN connection redirecting two PC's to a VPN, so it uses policy based routing. When I turn this off, the Internet correctly shows connected. Turn it on, and goes back to disconnected (even though it remains connected).
Anybody have any idea why the VPN would affect the status?
Not that it really matters - I know it is connected so it really is just a display issue.