MaverickPenguinX
Occasional Visitor
Hi
ASUS IPSEC IKEv1 XAUTH/PSK server to IKEv1 XAUTH/PSK + IKEv2 EAP server.
Both profiles can run parallel.
You should to get Let's encrypt certificate for your ddns.
Without letsencrypt, you need to generate self-signed certificate and install CA to trusted root CA of each devices. I don't like this progress.
Just follow these threads
IKEv2 server share the same username and password with IKEv1.
https://www.snbforums.com/threads/asus-ipsec-vpn-server.44973/#post-473984
https://www.snbforums.com/threads/asus-ipsec-vpn-server.44973/page-4#post-531279
Merlin firmware supports ipsec.postconf and strongswan.postconf since 384.9
So no need additional script to build IKEv2 server for windows 10 clients.
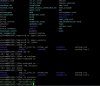
Here is my latest ipsec.postconf
nano /jffs/scripts/ipsec.postconf
Code:#!/bin/sh CONFIG=$1 source /usr/sbin/helper.sh pc_append "" $CONFIG pc_append "ca letsencrypt" $CONFIG pc_append " cacert=/jffs/.le/$(nvram get ddns_hostname_x)/ca.cer" $CONFIG pc_append " auto=add" $CONFIG pc_append "" $CONFIG pc_append "conn IKEv2-EAP" $CONFIG pc_append " keyexchange=ikev2" $CONFIG pc_append " left=$(nvram get wan0_ipaddr)" $CONFIG pc_append " leftid=@$(nvram get ddns_hostname_x)" $CONFIG pc_append " leftsubnet=0.0.0.0/0" $CONFIG pc_append " leftfirewall=yes" $CONFIG pc_append " leftauth=pubkey" $CONFIG pc_append " leftcert=/jffs/.le/$(nvram get ddns_hostname_x)/$(nvram get ddns_hostname_x).cer" $CONFIG pc_append " right=%any" $CONFIG pc_append " rightdns=$(nvram get lan_ipaddr)" $CONFIG pc_append " rightsourceip=10.10.11.0/24" $CONFIG pc_append " rightauth=eap-mschapv2" $CONFIG pc_append " eap_identity=%any" $CONFIG pc_append " dpdtimeout=30s" $CONFIG pc_append " dpdaction=clear" $CONFIG pc_append " dpddelay=10s" $CONFIG pc_append " auto=add" $CONFIG pc_append " leftfirewall=yes" $CONFIG pc_append " lefthostaccess=yes" $CONFIG pc_append " leftauth=pubkey" $CONFIG pc_append " dpddelay=10s" $CONFIG pc_append " rekey=no" $CONFIG pc_append " auto=add" $CONFIG
For windows add connection via powershell:
Add-VpnConnection -Name "home" -ServerAddress YOURDOMAIN.asuscomm.com -TunnelType "Ikev2"
I added in the code you suggested and I get the error that my IKE Credentials are unacceptable. I'm not quite sure what you mean by IKE 1 udername and pass is the same as IKE2, are we talking about the IPSec username and pass that you make in the Asus IPsec VPN section?