Hi good people!
I am trying to improve my home security and part of it would be to block the tapo cameras from internet, but would like to connect to vpn and then be able to access them.
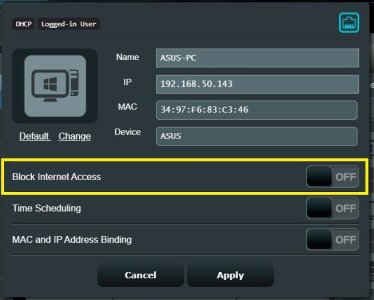
I have tried the simplest method found, just using the block internet in the asus app, but I am not able to access it when using vpn to my router. Parental controls, adding there and blocking, the same. In the VPN settings, the option "Client will use VPN to access" is set to "both".
So, please help on how can I block the device from being exposed to internet (Tapo App or anything) and being able to use it only when connected through VPN or the local wifi?
I AX88U with the latest merlin firmware and skynet.
After this, upnp research and restricting plex access and such stuff, but that is to come.
Any help is appreciated.
I am trying to improve my home security and part of it would be to block the tapo cameras from internet, but would like to connect to vpn and then be able to access them.
I have tried the simplest method found, just using the block internet in the asus app, but I am not able to access it when using vpn to my router. Parental controls, adding there and blocking, the same. In the VPN settings, the option "Client will use VPN to access" is set to "both".
So, please help on how can I block the device from being exposed to internet (Tapo App or anything) and being able to use it only when connected through VPN or the local wifi?
I AX88U with the latest merlin firmware and skynet.
After this, upnp research and restricting plex access and such stuff, but that is to come.
Any help is appreciated.