My home network is behind a CGNAT and I would like to access a couple of computers on the network remotely. I have used the Hub and Spoke guide.
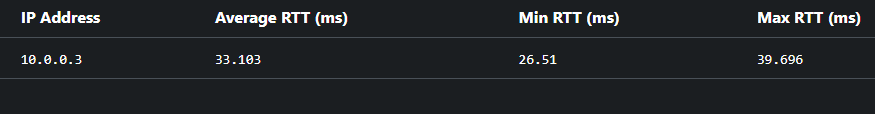
The router at home is an AX-86U running 3004.388.10.12. I have set up a VPS running a wireguard server. I have tried a couple of setups and I cannot access my lan network from remotely. I can only access the router's wireguard ip address.
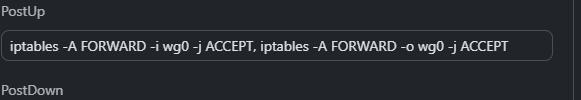
On the server I have set ip forward =1, I have tried allowed ips as 0s as well as the home network ip on both the server and my remote devices with the Asus as both 0's and the server's ip. I have tried blank iptables and several other options seen from various setups found on the internet.
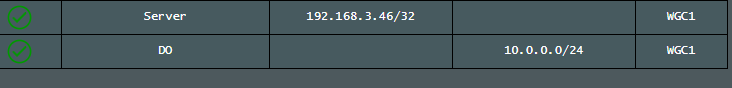
The router is running wireguard client and does not have the toggle for access intranet. I have added dns director to have WC1 to show my wg server ip's /24.
Is this an issue with the router not redirecting the wg ips to lan and back?
The router at home is an AX-86U running 3004.388.10.12. I have set up a VPS running a wireguard server. I have tried a couple of setups and I cannot access my lan network from remotely. I can only access the router's wireguard ip address.
On the server I have set ip forward =1, I have tried allowed ips as 0s as well as the home network ip on both the server and my remote devices with the Asus as both 0's and the server's ip. I have tried blank iptables and several other options seen from various setups found on the internet.
The router is running wireguard client and does not have the toggle for access intranet. I have added dns director to have WC1 to show my wg server ip's /24.
Is this an issue with the router not redirecting the wg ips to lan and back?