RebornVampie
Occasional Visitor
There is much (outdated) information and I didnt find a step by step manual so I am trying to create one while fixing the network myself. I am trying to summarize it one topic. I have used OTHER peoples information. I am an ICU nurse with an interest in technology and usually am able to fix things with comprehensive reading. I appreciate feedback and recommendations.
Situation:
- Current setup: ONT -> ISP router - AC68U (merlin, wired) as acces point, AX58U (merlin, wired) as second access point.
- New setup: ONT -> AX88U pro (merlin) as main router - AX88u (asus, wired) as node - AX58u (asus, wired) as node.
House is three stories, classical European stone house from 1980s. We laid preproduced high quality CAT6A cables to every floor.
Reason:
My girlfriend and me are moving in together and this is a good moment to have a system overhaul.
Goals:
get an easily managable network running maximum capacity both on WiFi and LAN by using AiMesh. Have a safe protected WiFi.
Devices: 2 synology (DS218+ (externally accessable (VPN, Plex etc)), DS416), Hue lights, google audio x4, google home speaker x2, Somfy Connexoon (Sunshade + Shutters), Honeywell Round WiFi, Toshiba AC, Imou camera's x5, solar panels. Phones, laptops, computers. (Getting them managed in homekit as soon as we are living together . Everything works individually now.)
. Everything works individually now.)
Basic setup:
1. download and extract current firmware of every router to PC (ozarkedge, jan 6th). Merlin on main and original Asus on nodes. Advantage: easy update, turn auto update OFF
2. wire the PC to router LAN (ozarkedge, jan 6th)
3. browse to the router's default LAN IP address (ozarkedge, jan 6th)
4. perform the quick internet setup routine, skipping WAN (ozarkedge, jan 6th)
5. upload the current firmware (ozarkedge, jan 6th)
6. Hard Reset that firmware to its default settings (ozarkedge, jan 6th) How To: https://www.asus.com/us/support/faq/1039074/
7. perform the quick internet setup routine for real. (ozarkedge, jan 6th)
AiMesh setup (wired backhaul (main LAN to node WAN) is best performance):
8. login to main router
9. press search (1-2 minutes)
10. click add (2-5 minutes).
Do it one by one.
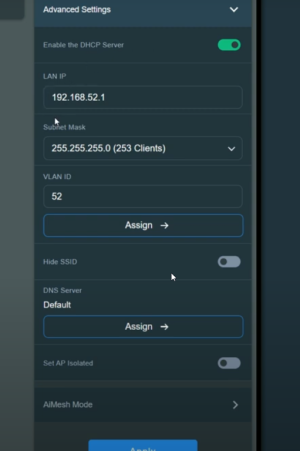
11. settings

 dongknows.com
dongknows.com
Sources: https://www.snbforums.com/threads/asus-rt-axu88-pro-install-and-setup-questions.93475/
Situation:
- Current setup: ONT -> ISP router - AC68U (merlin, wired) as acces point, AX58U (merlin, wired) as second access point.
- New setup: ONT -> AX88U pro (merlin) as main router - AX88u (asus, wired) as node - AX58u (asus, wired) as node.
House is three stories, classical European stone house from 1980s. We laid preproduced high quality CAT6A cables to every floor.
Reason:
My girlfriend and me are moving in together and this is a good moment to have a system overhaul.
Goals:
get an easily managable network running maximum capacity both on WiFi and LAN by using AiMesh. Have a safe protected WiFi.
Devices: 2 synology (DS218+ (externally accessable (VPN, Plex etc)), DS416), Hue lights, google audio x4, google home speaker x2, Somfy Connexoon (Sunshade + Shutters), Honeywell Round WiFi, Toshiba AC, Imou camera's x5, solar panels. Phones, laptops, computers. (Getting them managed in homekit as soon as we are living together
Basic setup:
1. download and extract current firmware of every router to PC (ozarkedge, jan 6th). Merlin on main and original Asus on nodes. Advantage: easy update, turn auto update OFF
2. wire the PC to router LAN (ozarkedge, jan 6th)
3. browse to the router's default LAN IP address (ozarkedge, jan 6th)
4. perform the quick internet setup routine, skipping WAN (ozarkedge, jan 6th)
5. upload the current firmware (ozarkedge, jan 6th)
6. Hard Reset that firmware to its default settings (ozarkedge, jan 6th) How To: https://www.asus.com/us/support/faq/1039074/
7. perform the quick internet setup routine for real. (ozarkedge, jan 6th)
AiMesh setup (wired backhaul (main LAN to node WAN) is best performance):
8. login to main router
9. press search (1-2 minutes)
10. click add (2-5 minutes).
Do it one by one.
11. settings

ASUS AiMesh Setup Guide: Detailed Steps and 100% Solid Tips | Dong Knows Tech
Here's the detailed AiMesh setup guide for that weekend project of building a robust Wi-Fi system for your home using a few ASUS routers. Check it out!
Last edited: