This is a good example of how NOT all firmware is created equal, and why the choice of firmware is NOT arbitrary or to be taken lightly.
As
@ColinTaylor suggests, you could use guest networks, but this limits you to wireless only. And it's an all or nothing solution. It's not going to be easy to make exceptions (e.g., provide access to a printer on the private network from a guest network, or chromecast to a device on the guest (IOT) network from the private network). AFAIK, access between the guest networks isn't possible either. Merlin doesn't implement guest networks in a consistent manner either, sometimes using the same IP network (presumably isolated w/ ebtables), other times using different IP networks (isolated w/ iptables). When guests are using the same IP network as the private network, now you have the issue of users on some networks being able to "see" (through network discovery) other devices if NOT necessarily access them (a security issue for some ppl), and perhaps requiring more than a class C network for larger numbers of users.
For the more general and useful purposes of just adding and isolating wired/wireless networks as you see fit, Merlin was just never designed for these purposes.
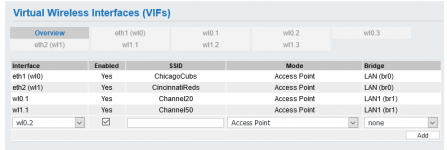
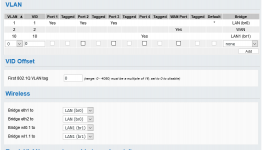
Contrast that to something like FT (FreshTomato) which *is* designed from the ground up (i.e., natively) to provide such support. Everything in FT starts w/ a bridge, to which you assign whatever wired ports and/or wireless APs/VAPs you need, all of which are isolated by default, and w/ exceptions made possible via the GUI (LAN Access section), or worst case iptables.
The closest thing we have to the kind of capability you seek w/ Merlin is by
@Jack Yaz, who's apparently (last I heard) working on some script(s). But even that will be a compromise since it's NOT integrated into the GUI.
IOW, the two firmwares are purposely designed to solve different problems. And it's why it matters which firmware you choose when designing your network. Of course, they both have other advantages and disadvantages. YOU have to decide which best meets your design requirements w/ the least compromises.
That's why even though I often use and recommend Merlin for my own customers, for my *personal* primary router, I still use FT. Having these sorts of capabilities are fundamental to my network architecture, regardless the other benefits Merlin offers.
Of course, the better option would probably be to NOT use these routers AT ALL for these purposes, but manage it all w/ a prosumer layer 3 managed switch and standalone APs/VAPs. But given the cost and additional complexity, probably NOT a practical solution for most users.