adfontes
New Around Here
Hey Guys.
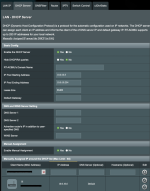
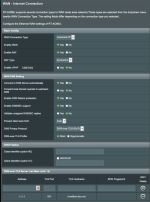
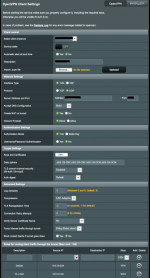
I have a DNS leak and I hope someone can point me into the right direction to fix it.
What works (no DNS leak):
Hardware: RT-AC86U
Installed scripts: Diversion
Thanks
I have a DNS leak and I hope someone can point me into the right direction to fix it.
What works (no DNS leak):
- DoT + VPN (without policy rules)
- VPN + Policy Rules
- DoT + OpenVPN & Policy Rules enabled
Hardware: RT-AC86U
Installed scripts: Diversion
Thanks