VeloxNEx
Occasional Visitor
Hi everybody... First post. I'm running the Asuswrt-merlin firmware. It's pretty great!
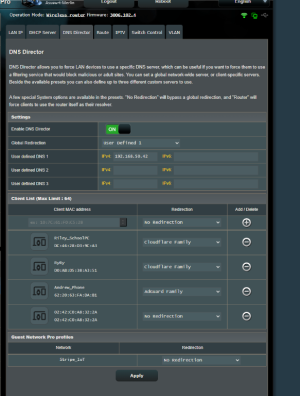
There's a larger story but I think my DNS director hates me. I pointed it at the User defnied 1 at my pihole and it seemed to put the iptable entry last, which mean it'll basically never get hit.
If I remove the automatically generated "RETURN" enteries the pihole gets the traffic and everything seems to be functional. But if for any reason I have to save the DNS Director again, those enteries get re-entered and the pihole is back down at the bottom.
Outside of not using the DNS director, is this expected/normal? Have I done something to break the DNS director? Does it just hate me?
There's a larger story but I think my DNS director hates me. I pointed it at the User defnied 1 at my pihole and it seemed to put the iptable entry last, which mean it'll basically never get hit.
Code:
#iptables -t nat -L DNSFILTER -v
Chain DNSFILTER (4 references)
pkts bytes target prot opt in out source destination
0 0 DNAT all -- any any anywhere anywhere MAC DC:46:28:D3:9C:A3 to:1.1.1.3
0 0 DNAT all -- any any anywhere anywhere MAC D0:AB:D5:38:A3:51 to:1.1.1.3
0 0 DNAT all -- any any anywhere anywhere MAC 62:20:63:FA:DA:B1 to:94.140.14.15
6 495 RETURN all -- any any anywhere anywhere MAC 02:42:C0:A8:32:2A
87 6296 RETURN all -- br52 any anywhere anywhere
1002 70167 RETURN all -- br0 any anywhere anywhere
0 0 RETURN all -- br0 any anywhere anywhere
0 0 DNAT all -- any any anywhere anywhere to:192.168.50.42
#@GT-BE98_Pro-C528:/tmp/home/root#If I remove the automatically generated "RETURN" enteries the pihole gets the traffic and everything seems to be functional. But if for any reason I have to save the DNS Director again, those enteries get re-entered and the pihole is back down at the bottom.
Outside of not using the DNS director, is this expected/normal? Have I done something to break the DNS director? Does it just hate me?