...or pfSense, OPNsense, etc. BTW I have not set up a BARE Linux box as a router/firewall since...oh...probably 2000! Unless you are (or want to be) a wizard with raw iptables, best to find a distribution that has simple router/firewall front end (anyone remember Mandrake Single Network Firewall?).
Sorry to reply to this slightly old thread, but this caught my interest. You don't need to learn or use raw iptables at all. Shorewall is the tool here, and I love it. After years of using pfSense, I got sick of it corrupting itself and chewing up my config; and while OPNsense is nice enough it can't implement WireGuard properly due to an upstream bug (and it'd only be in user space anyway).
My solution this month? A refurb SFF Dell Optiplex 7010 from eBay (Core i7 3770, 8GB RAM, 128GB SSD, Intel Pro 1000PT server NIC) and a headless Arch Linux install with the linux-hardened kernel. I took 30 mins to add the Arch base, with dnscrypt-proxy for (encrypted) DNS, dhcpd for DHCP, and Shorewall for the stateful firewall. Oh, and the WireGuard kernel module of course.
Shorewall has simple config files that live in /etc/shorewall, and you edit them to reflect your network. No iptables stuff, no weird code or syntax. Just a few easy to follow tables that you fill in as needed with normal English language. Shorewall then reads those files on boot and uses them to configure Netfilter directly, and then exits. Simple. For my uses I just set ./interfaces with the five NICs I had available, then ./zones to list WAN, LAN, DMZ and VPN, ./policy to allow firewall to all, LAN via VPN tunnel only, DMZ to WAN, and to drop traffic from DMZ to LAN. The ./rules file allows easy DNAT and other rules, again in a human readable pro forma table format ('ACCEPT WAN DMZ 80 tcp'), then just two lines in the ./snat file to masquerade LAN and DMZ. Literally five minutes' work (mostly typing out my DNAT rules) and it's been solid ever since.
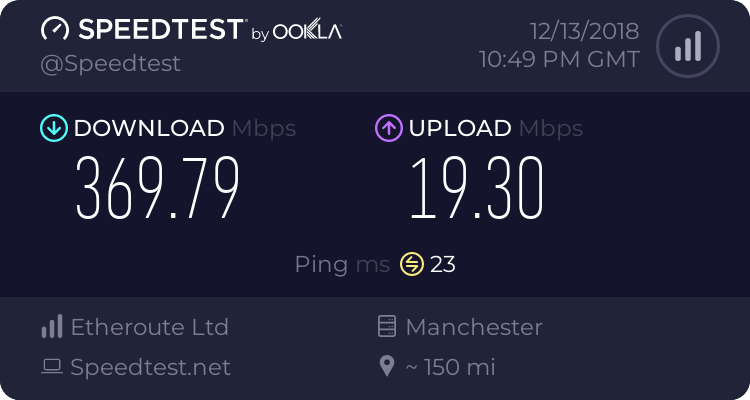
I have a 380/20 cable connection and get that 24/7 over WAN, and the i7 gives me a comfortable ~370 over the WireGuard VPN with all 8 threads simmering away barely in double figures under full network load. My uptime shows that overall system load averages are in the order of 0.01 to 0.1, and we don't have a quiet network!
Not that I disagree with your points in general, but I did want to add for future readers that not only is a Linux router possible, but could be preferable - and it's practically easy these days even with multiple subnets and VPNs. Shorewall is a beautiful thing. <3 Because it's only a base Arch install it doesn't need much updating, and is very stable. Arch being close to upstream means fast bug and security fixes too.
Here's a rough (slightly outdated)
network topology of my home.
Here's
my GitHub with my Shorewall configs and my custom WireGuard scripts and systemd service.
Finally here's a speed test from a LAN client connected via WireGuard:
Sorry... As you were.