Re-visiting the post and looking closer, none of the screenshots pop up in full resolution..
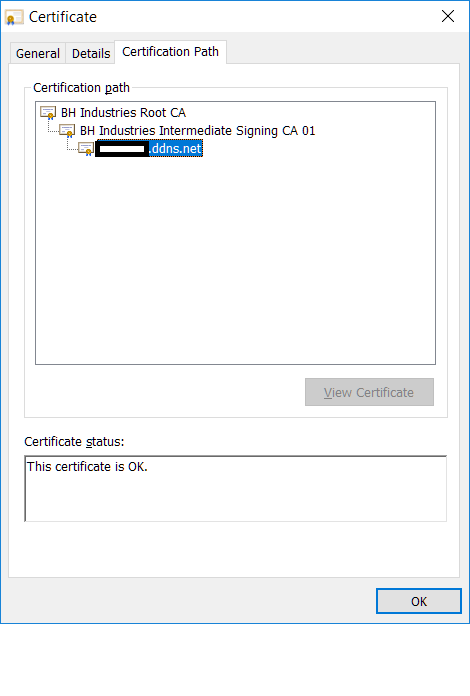
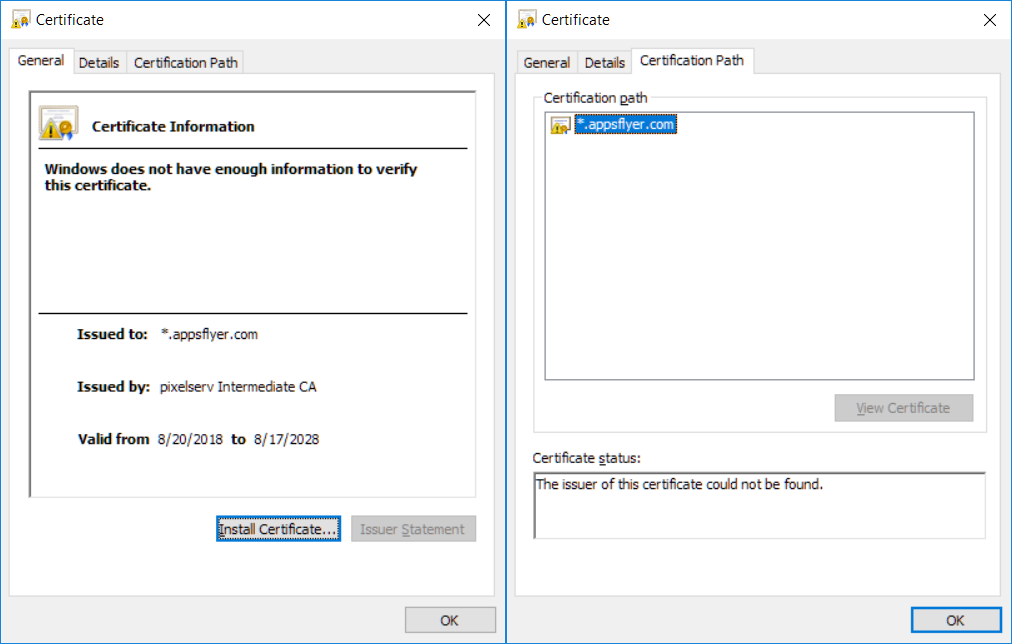
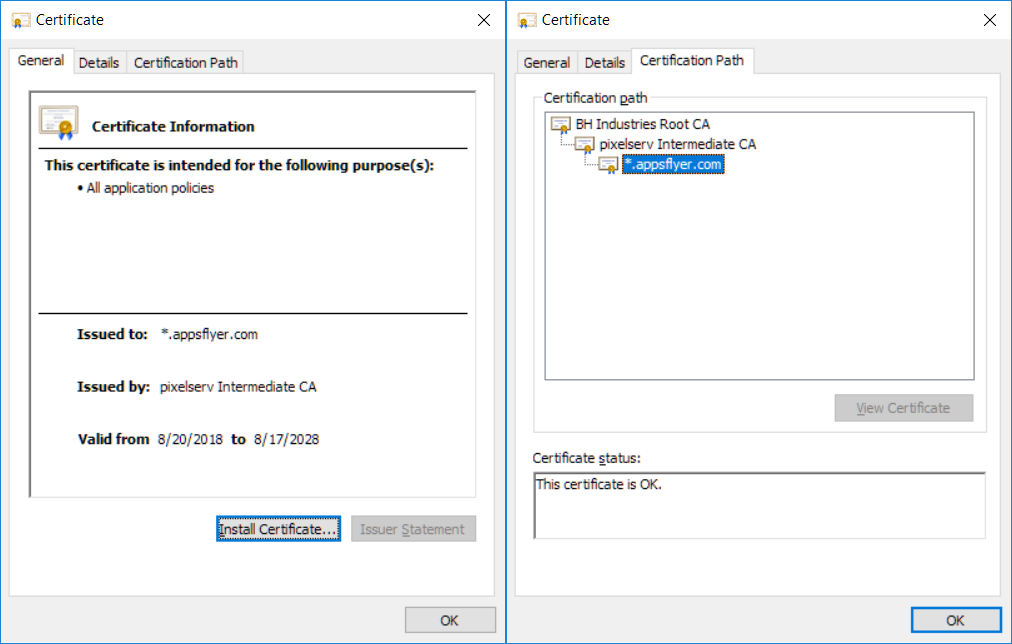
You aren't expected as usual to import the immediate CA cert generated for use in pixelserv-tls. I can't recall doing that in my development tests two years ago. And I didn't receive complaints from the gent who deploys it to his one million users..
But there is a chance he might be deploying the intermediate cert as well. I need to find time to re-test and confirm it there is an issue.
Not sure what you mean about full resolution...the pics I posted? They appear in normal res on my end, plenty large/clear enough to see what I am indicating. Apologies if you have some type of visual impairment and have requested a specific type of shot (being totally real here...not facetious).
In any event, I think my 3rd explanation in my post is probably the correct one and there is not an issue. I've done several tests with both the self signed certs and my PKI and the stats look similar so I think I have the PKI setup correctly.
I am however having another issue which is pretty problematic. At first I thought it was AB-solution, but my testing shows I don't have the problem with just AB-solution,
only when I use pixelserv with it. I have done my testing both with my PKI and the original certs (OOB config) and got the same results. I originally posted this as an issue in the AB thread (issue #2
here), but am going to move it here based on further testing.
The summation is:
I'm not sure how much more info I can give other than pixelserv On = horrible lag on snbforums, pixelserv Off = seemingly normal usage. I can basically recreate this at will. Any ideas?
Now that I've done more testing on this and I can definitively conclude that pixelserv is causing this problem - or at least exacerbating it. It's almost a show stopper for me, and I really don't want it to be as I'd like to remain a disciple in the pixelserv fold

My testing was done with Chrome (my preferred browser), IE, and Edge. When I visit this a forum thread with each with pixelserv turned on, I get the following differences in how blocked ads are displayed. I'm not sure how important this is, but it is interesting (especially IE's behavior) and may provide a data point to my real issues:
Links to pics:
-
Chrome
-
IE
-
Edge
In addition to these viewing differences, both Chrome and IE are unbearable laggy. If I try to scroll the page using the right-most scroll bar (or arrow keys), if I try to select text, or if I am typing it is very jumpy. For instance, at least every other sentence I type right now I am having a delay of 3-5 seconds for text to catch up. It takes sometimes 3+ seconds for an incorrectly spelled word to be highlighted, etc. All around just a bad experience that makes it seem I'm working on a 15 year old computer, not an i7 with 32GB of RAM.
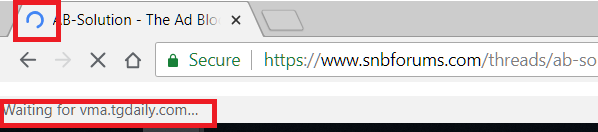
Additionally, Chrome seems to never fully finish even loading the page (or at least it takes several minutes, after which time the lagginess remains). What I see in Chrome's address bar is the loading wheel constantly spinning and addresses flashing in the lower left corner as if it is trying to access those resources. Here is an example of the two areas:
If I go into AB-solution and disable pixelserv, this issue goes away.
I have seen similar behavior on at least a couple other sites over the past week or so as I've been setting up this solution, unfortunately I can't remember which ones. However based on my ability to recreate this at will with SNBforums I think that's enough to work with.
I could really use some advice on this as it is pretty unbearable.
thanks.
UPDATE:
I've got some more damning evidence showing that pixelserv is definitely negatively influencing Chrome's behavior (in my setup).
I started Chrome up with no extension/plugins and visited this site.
One time with pixelserv enabled (and exhibiting the issues), and one time without.
Each time I let chrome settle for about 30 seconds to finish loading the page and any chrome initial resources.
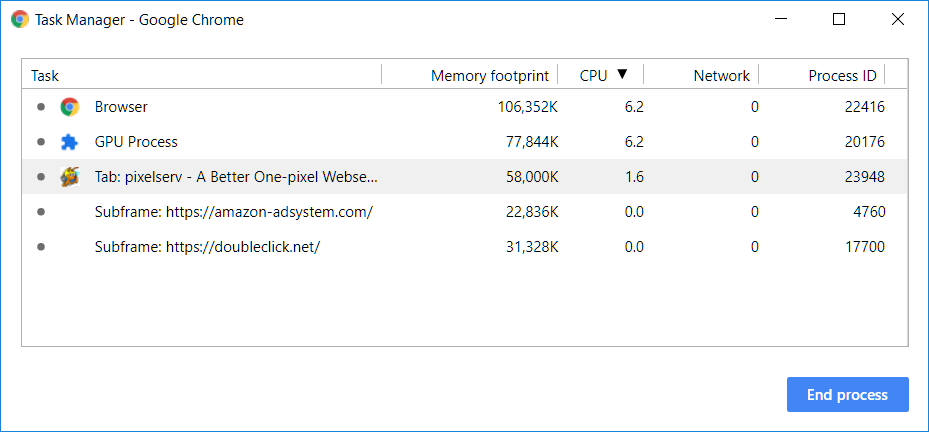
This is what Chrome's task manager shows when pixelserv is disabled:
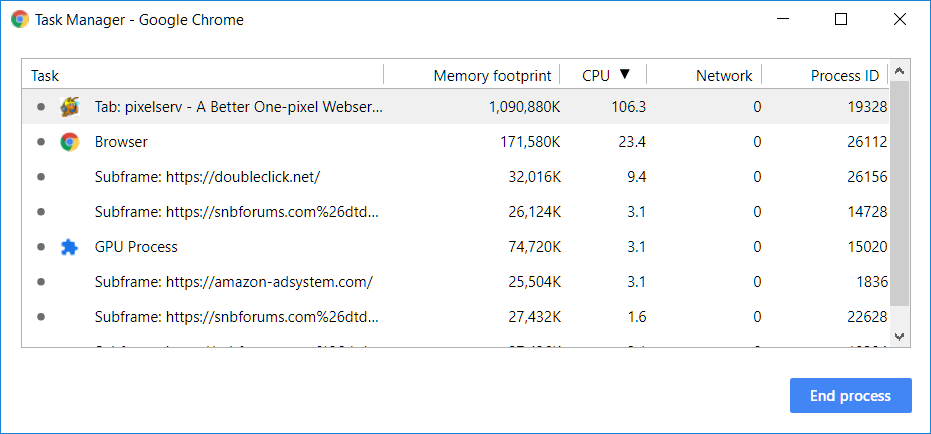
Relatively small cpu and mem footprint. But this is the exact same test with pixelserv enabled on the router:
That was after about 30 seconds. Within another 30 it had climbed to 1.5 GB memory footprint and continued to climb.
Obviously something isn't right here.
It is entirely possible that I have a misconfiguration somewhere - but this is all a pretty straight forward setup. As mentioned I have these issues with using the default PKI setup as well (as my PKI is the only
special setup I've done).
Note that most websites don't seem to exhibit this behavior - but seemingly some do.