dave14305
Part of the Furniture
Pixelserv 2.3.1 to generate the domain certs properly to iOS new requirements.Apparently the iPhone device I have on my network isn't trusting the pixelserv certificate even though it's 2048 bit. What am I missing?
Pixelserv 2.3.1 to generate the domain certs properly to iOS new requirements.Apparently the iPhone device I have on my network isn't trusting the pixelserv certificate even though it's 2048 bit. What am I missing?
If your CA is 2048 bit and SHA-2, you’re using pixelserv 2.3 or newer, and have manually trusted the certificate on the iPhone in settings, general, about then the only further idea I have is to purge your generated certificates in /opt/car/cache/pixelserv to ensure they’re generated with the current version/requirementsApparently the iPhone device I have on my network isn't trusting the pixelserv certificate even though it's 2048 bit. What am I missing?
If your CA is 2048 bit and SHA-2, you’re using pixelserv 2.3 or newer, and have manually trusted the certificate on the iPhone in settings, general, about then the only further idea I have is to purge your generated certificates in /opt/car/cache/pixelserv to ensure they’re generated with the current version/requirements
Are you running the latest Diversion v4.1.8? If not, you'll have to update and carefully follow the instructions in the release notes for 4.1.8: https://diversion.ch/I know it's 2048 as diversion reported that. How do I know whether it's SHA-2 or not?
Inspecting the certificate. It’s highly unlikely that you’re not using SHA-2 (probably SHA-256) because all methods of certificate generation around these parts use it. SHA-1 has been out of favor for many years due to insecurity.I know it's 2048 as diversion reported that. How do I know whether it's SHA-2 or not?
from the command line:I know it's 2048 as diversion reported that. How do I know whether it's SHA-2 or not?
openssl x509 -in /opt/var/cache/pixelserv/ca.crt -noout -textSignature Algorithm: sha256WithRSAEncryptionopenssl genrsa -out ca.key 2048
openssl req -key ca.key -new -x509 -days 3650 -sha256 -extensions v3_ca -out ca.crt -subj "/CN=Pixelserv CA" -config /tmp/diversion/div-openssl.cnfdiversion disable && cd /opt/bin && wget -O Pixelserv.zip https://github.com/kvic-z/pixelserv-tls/releases/download/v2.3.1/pixelserv-tls.2.3.1.Entware-3.x.aarch64softfloat.zip && opkg install p7zip && 7za e Pixelserv.zip *.dynamic -r && rm pixelserv-tls && mv pixelserv-tls.armv8.ent.performance.dynamic pixelserv-tls && chmod +x pixelserv-tls && rm Pixelserv.zip && opkg remove p7zip && cd -- && diversion enablediversion disable && cd /opt/bin && wget -O Pixelserv.zip https://github.com/kvic-z/pixelserv-tls/releases/download/v2.3.1/pixelserv-tls.2.3.1.Entware-ng.armv7softfloat.zip && opkg install p7zip && 7za e Pixelserv.zip *.dynamic -r && rm pixelserv-tls && mv pixelserv-tls.arm.ent.performance.dynamic pixelserv-tls && chmod +x pixelserv-tls && rm Pixelserv.zip && opkg remove p7zip && cd -- && diversion enableAlright, I hear you all.
I've just pushed a Diversion update, no version change
What's new
- Option in ep, 6, 3 to update pixelserv-tls to v2.3.1 (@Jack Yaz version) for all router models.
Use u to update.
Naw, you learned something new!Very cool!
So I should have just waited one more day.
Gotta love this forum.
Naw, you learned something new!
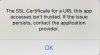
Did you already follow the CA import instructions here: https://github.com/kvic-z/pixelserv-tls/wiki/Create-and-Import-the-CA-Certificate#iosandroidView attachment 21130
Woah. Something new on me.
Using an app and suddenly see this warning. Only occurs when using this specific app. Just upgraded to iOS 13.3.1, am on pixelserv-tls 2.3.1, ac86u, merlin’s 384.14_2. Only happens when using my router with pixelserv on it, mobile data is fine unless I VPN into my router, which leads me to think it’s pixelserv related.
Its a quasi-government app which makes me reach for my tin foil hat. But then again, considering the country I live in, a tin foil hat is a requirement.
Any ideas?
@^Tripper^, did you fully remove any old ca.crt certificates and only then import the latest pixelserv-tls v2.3.1 generated one on that iPhone?
Did you already follow the CA import instructions here: https://github.com/kvic-z/pixelserv-tls/wiki/Create-and-Import-the-CA-Certificate#iosandroid
If so, the app might have the expected certificate pinned and warns you if it doesn't match.
Update; no dice. Deleted the app, rebooted the phone, reinstalled and still getting the error.
Hmmm... wonder what “checks” this app does.
Not exactly. I'm speculating that the expected certificate signature is hard-coded in the app and the pixelserv-generated certificate signature doesn't match that. A way to prevent spoofing of certs, but it's hard to say with any certainty what they're doing inside.@dave14305 To clarify, you’re saying the app has maybe “recorded” the cert and is throwing up the error as the new cert doesn’t match what it’s expecting? Didn’t think of that, will try deleting the app and trying again, that may possibly sort this out.
We use essential cookies to make this site work, and optional cookies to enhance your experience.
