postoronnim-v
Regular Contributor
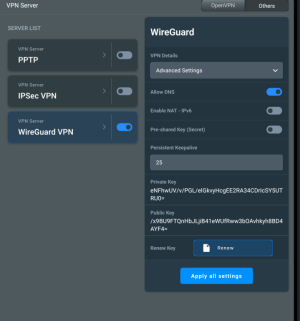
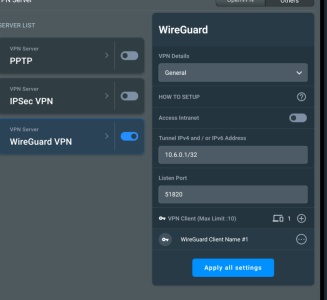
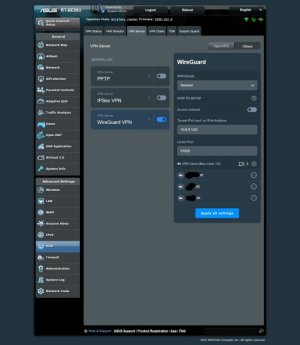
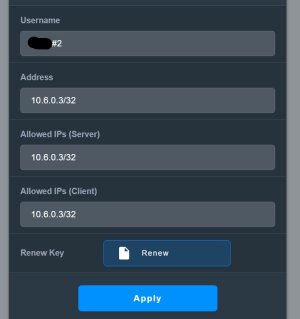
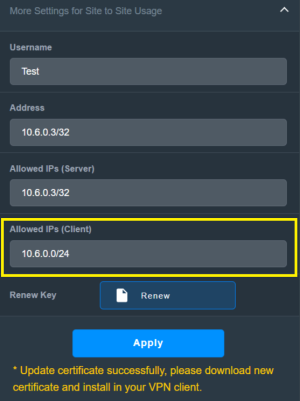
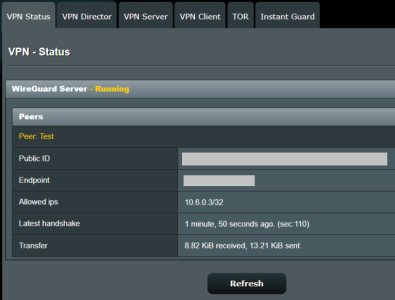
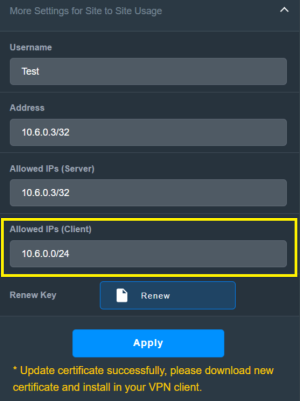
There's no such option in the client settings. This means the client can set these values at their own discretion."In WireGuard, the "AllowedIPs" setting for a client specifies which IP addresses or subnets the client is allowed to route through the VPN tunnel."