SeriousFamily
Regular Contributor
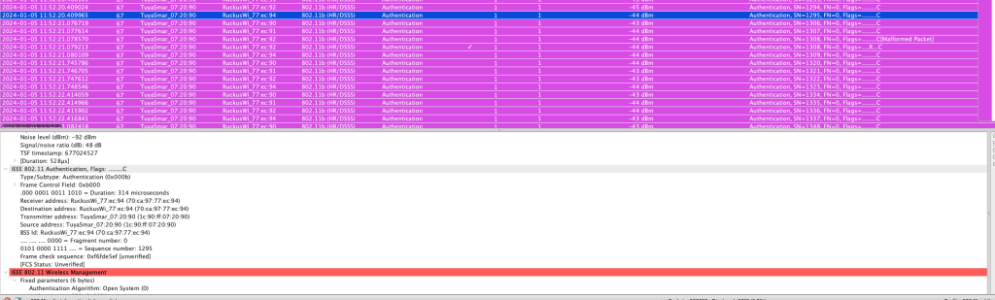
Just checked the system log on my ASUS RT-AX88U and I am also getting spammed with this stuff constantly!
I don't have any Tuya devices and the mac address doesn't appear to be one of mine.
Code:Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:46 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:51 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:56 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:56 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:48:56 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:48:56 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:49:01 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:49:01 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:49:06 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:49:06 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0 Jan 5 20:49:11 wlceventd: wlceventd_proc_event(645): eth6: Deauth_ind FC:67:1F:C5:69:CF, status: 0, reason: Unspecified reason (1), rssi:0 Jan 5 20:49:11 wlceventd: wlceventd_proc_event(685): eth6: Auth FC:67:1F:C5:69:CF, status: Successful (0), rssi:0
Need to see if I can find out how long this has been going on for
started some time in early december, the date of this thread was started december 13th.
so your on a rt ax88u and getting these things so it gets even wider not just a rt ax86u.
you also have a different address to us yours is showing as fc:67 but still links to tuya when mac lookup is used.
wifi 6 disabled here on the 2.4 - still get spam.See what disabling wifi6 on the 2.4 Ghz band does for you.