Hi guys,
I have successfully blocked 3 of my network cameras from accessing the internet.
I know there is an easy way to block network devices by following this method:
Network Map > Clients >Under Client Status > Click the network devices for its on the Ethernet icons > Block Internet Access

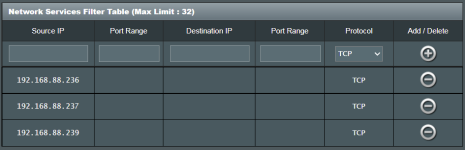
However, I am interested to know whether Firewall > Network Services Filter works?
As I am confused about whether the filter works for incoming traffic or outgoing traffic?
(I am confused about the Source IP & Destination IP)
Does the configuration below block all traffic in both ways? Incoming & Outgoing?
See below:

Thanks.
Appreciate someone can clarify.
I have successfully blocked 3 of my network cameras from accessing the internet.
I know there is an easy way to block network devices by following this method:
Network Map > Clients >Under Client Status > Click the network devices for its on the Ethernet icons > Block Internet Access
However, I am interested to know whether Firewall > Network Services Filter works?
As I am confused about whether the filter works for incoming traffic or outgoing traffic?
(I am confused about the Source IP & Destination IP)
Does the configuration below block all traffic in both ways? Incoming & Outgoing?
See below:
Thanks.
Appreciate someone can clarify.
Last edited: