SanPe
Occasional Visitor
With the help of @xtv I found what did I do wrong. But my issue is still not solved 
Original post title: Pihole + VPN, what do I do wrong?
Hi,
I have a device running unbound+pihole (on 192.168.0.11).
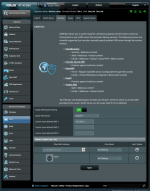
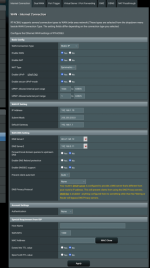
I set up my router - AC86U running latest stable merlin (on 192.168.0.1) - according to this post by dave14305 http://www.snbforums.com/threads/me...ccurate-device-names-how-to.69096/post-649388
Everything is working great.
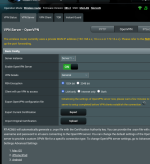
But I want to use my pihole as my DNS on my android phone. So, I set up a VPN server on the router and I'm running in a issue I cannot understand...
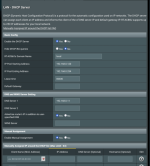
If I advertise DNS to clients, or if I include push "dhcp-option dns 192.168.0.11" on the custom config field, pihole is answering requests but I cannot access to the pihole GUI (nor ssh to the server or access any other services I host on this machine) ; still I can access to any other local machine.
Of course, if I stop advertise DNS to clients, everything is working fine except that pihole is not answering DNS requests...
What did I do wrong guys?
Thanks for your help!
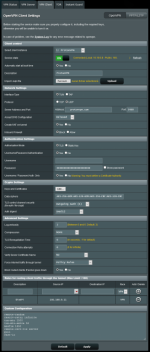
Edit: screenshots
Original post title: Pihole + VPN, what do I do wrong?
Hi,
I have a device running unbound+pihole (on 192.168.0.11).
I set up my router - AC86U running latest stable merlin (on 192.168.0.1) - according to this post by dave14305 http://www.snbforums.com/threads/me...ccurate-device-names-how-to.69096/post-649388
Everything is working great.
But I want to use my pihole as my DNS on my android phone. So, I set up a VPN server on the router and I'm running in a issue I cannot understand...
If I advertise DNS to clients, or if I include push "dhcp-option dns 192.168.0.11" on the custom config field, pihole is answering requests but I cannot access to the pihole GUI (nor ssh to the server or access any other services I host on this machine) ; still I can access to any other local machine.
Of course, if I stop advertise DNS to clients, everything is working fine except that pihole is not answering DNS requests...
What did I do wrong guys?
Thanks for your help!
Edit: screenshots
Attachments
Last edited: